How to integrate Azure AD (Entra ID) SAML SSO with your auth provider
Learn how to integrate Azure AD SSO with Logto using standard SAML connector.
Logto provides a out of box SAML connector to integrate with SSO identity providers. Each provider has its own specific information to configure. This guide will walk you through the steps to integrate Azure AD with Logto.
Create an new SAML social connector in Logto
-
Visit your Logto Cloud Console and navigate to the connector section.
-
Switch to the Social connectors tab and click Add Social Connector button on the top right.
-
Select the SAML connector.
You will be presented with the SAML connector creation form:
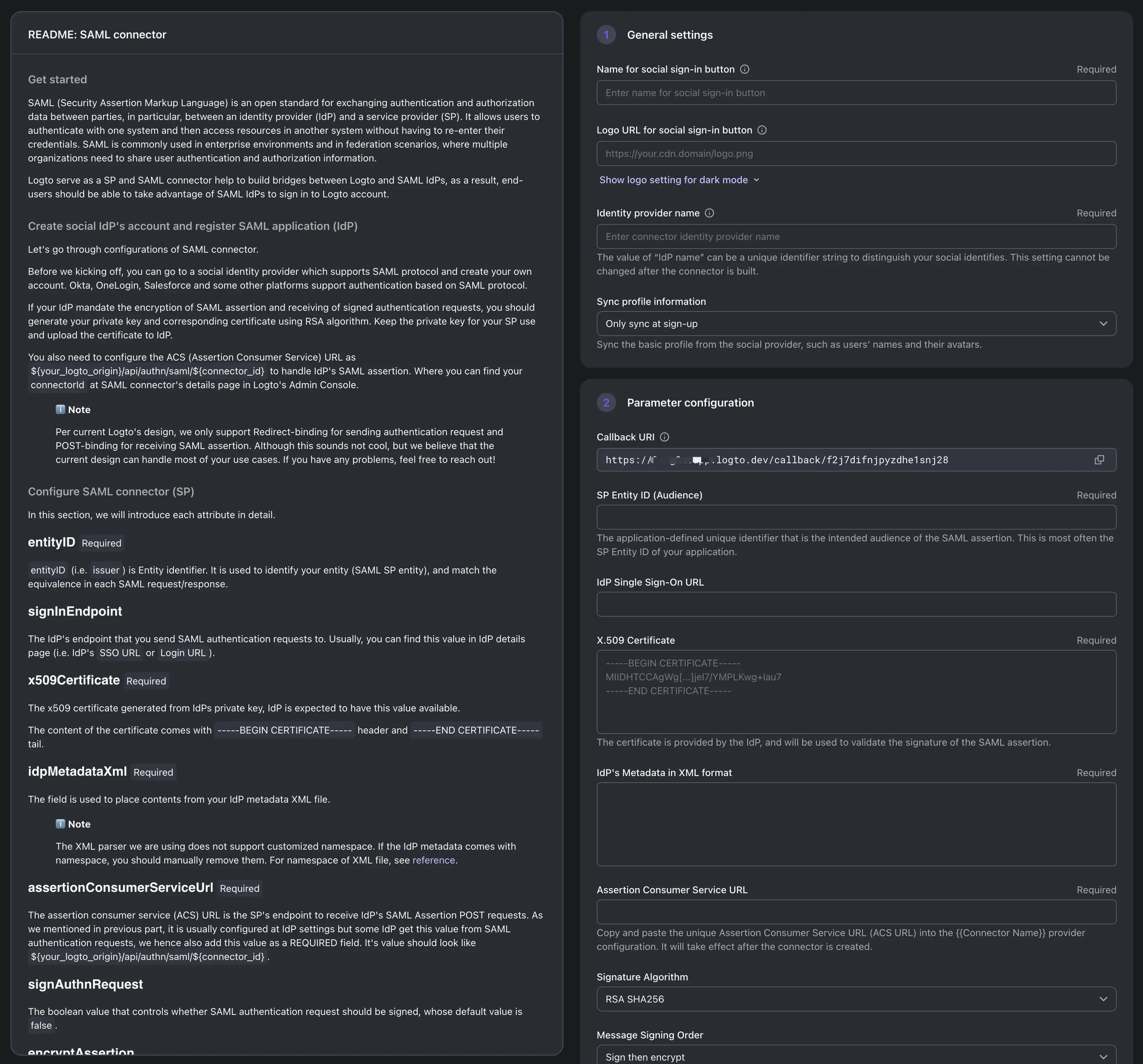
-
Fill in the connector general information
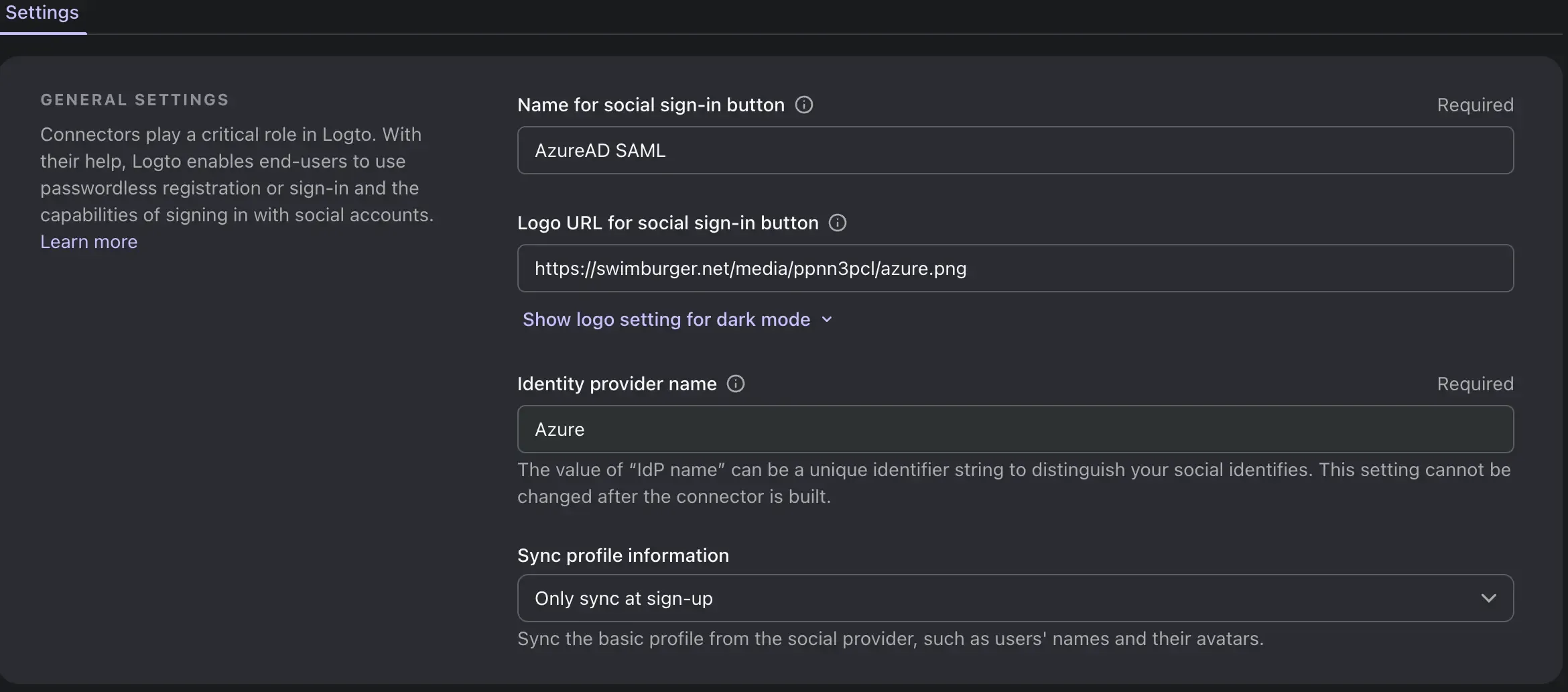
Field Name Description Name for social sign-in button The name of the social sign-in button that will be displayed on the login page. Logo URL for social sign-in button The logo URL of the social sign-in button that will be displayed on the login page. Identity provider name The name of the identity provider. That may help you identify the target provider of the connector. Sync profile information Whether to sync the user profile information from the identity provider only after the initial sign-up or after each sign-in session. -
Set Entity Id and Assertion Consumer Service URL
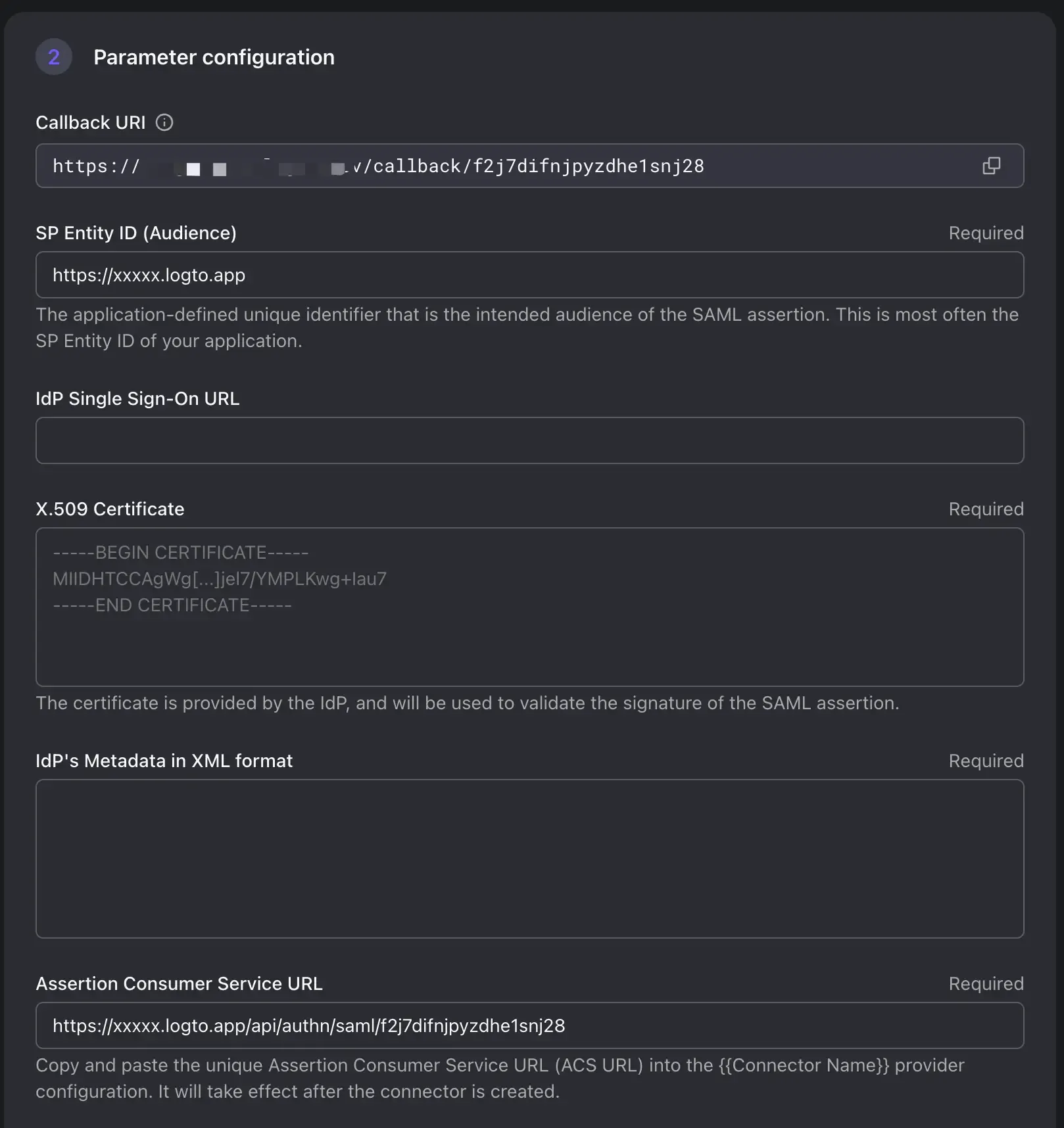
Entity ID" and an "ACS URL" are essential components used in the SAML exchange process for identity and service providers.
SP Entity ID: The Entity ID is a unique identifier that represents a SAML entity within a SAML-based system. It is used to distinguish different participants in the SAML exchange. The SP Entity ID helps both the IdP a to recognize request audience and establish trust.
ACS URL (Assertion Consumer Service URL): The ACS URL is a specific endpoint provided by the Service Provider (Logto) where the Identity Provider (IdP) sends the SAML assertion after successful authentication. Once a user is authenticated by the IdP, the IdP generates a SAML assertion containing user attributes and digitally signs it. The IdP then sends this assertion to the ACS URL of the SP. The SP validates the assertion, extracts user attributes, and logs the user in.
Field Name Description Example SP Entity ID (Audience) SP Entity used by AzureAD to identify the identity of the Logto. Use your Logto tenant endpoint as the EntityID is recommended https:// <tenant-id>.logto.appIdP single sign-on URL IdP SignIn endpoint. Optional in Azure. This field is used for SP to identify IdP initiated sign-in session. Currently Logto does NOT support IdP initialed sign-in session. Please leave this field blank X.509 Certificate The IdP certificate used to sign the SAML assertion. (We will retrieve this certificate from AzureAD later) IdP Metadata in XML format The IdP metadata XML file content. (We will retrieve this file from AzureAD later) Assertion Consumer Service URL The ACS URL of the SP. SP(Logto) endpoint to receive SAML assertion requests. Replace the tenant-id and connector-id with you own. https:// <tenant-id>.logto.app/api/authn/saml/<connector-id>
Create a SAML SSO application in Azure portal
-
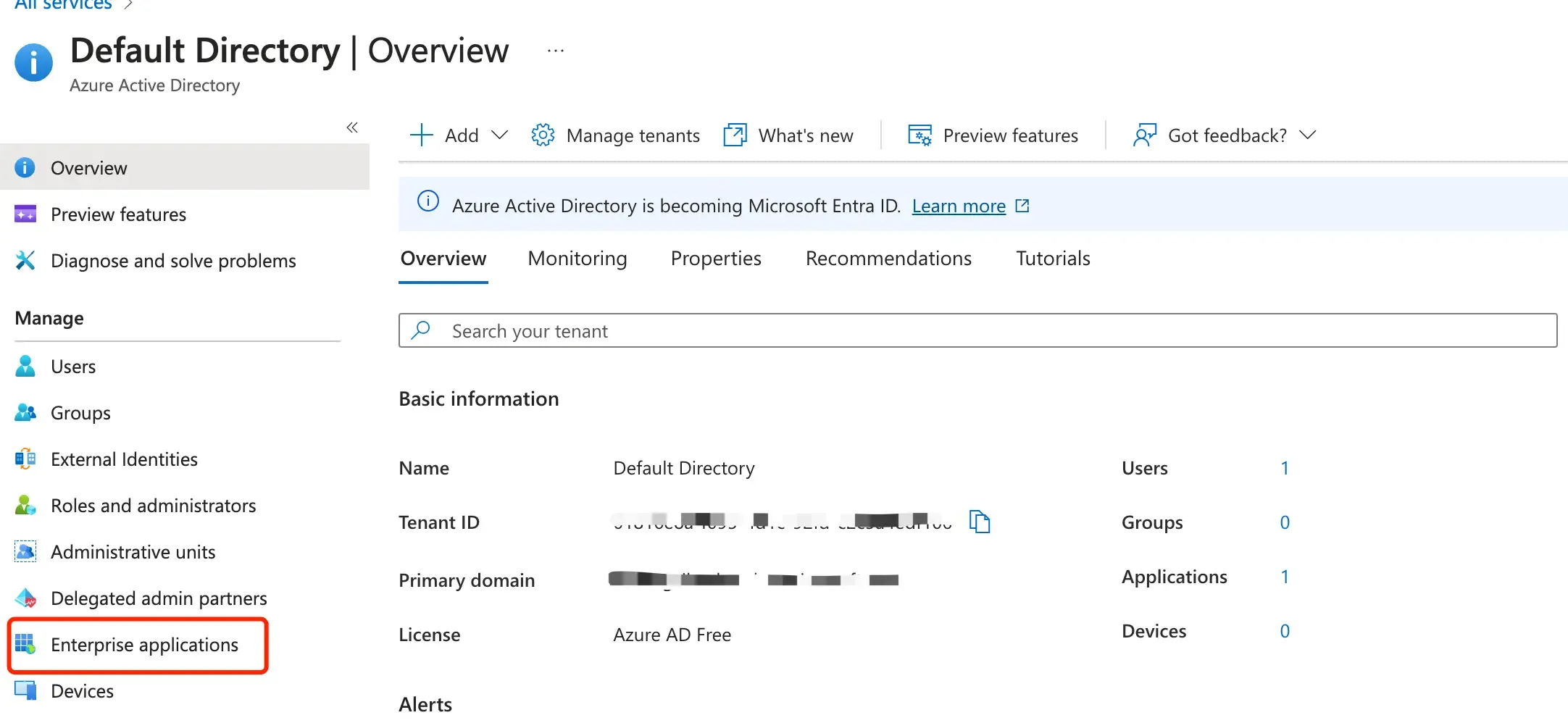
Log in to the Azure Active Directory dashboard. Select “Enterprise Applications”.
-
Select “New Application” → “Create your own application”.

-
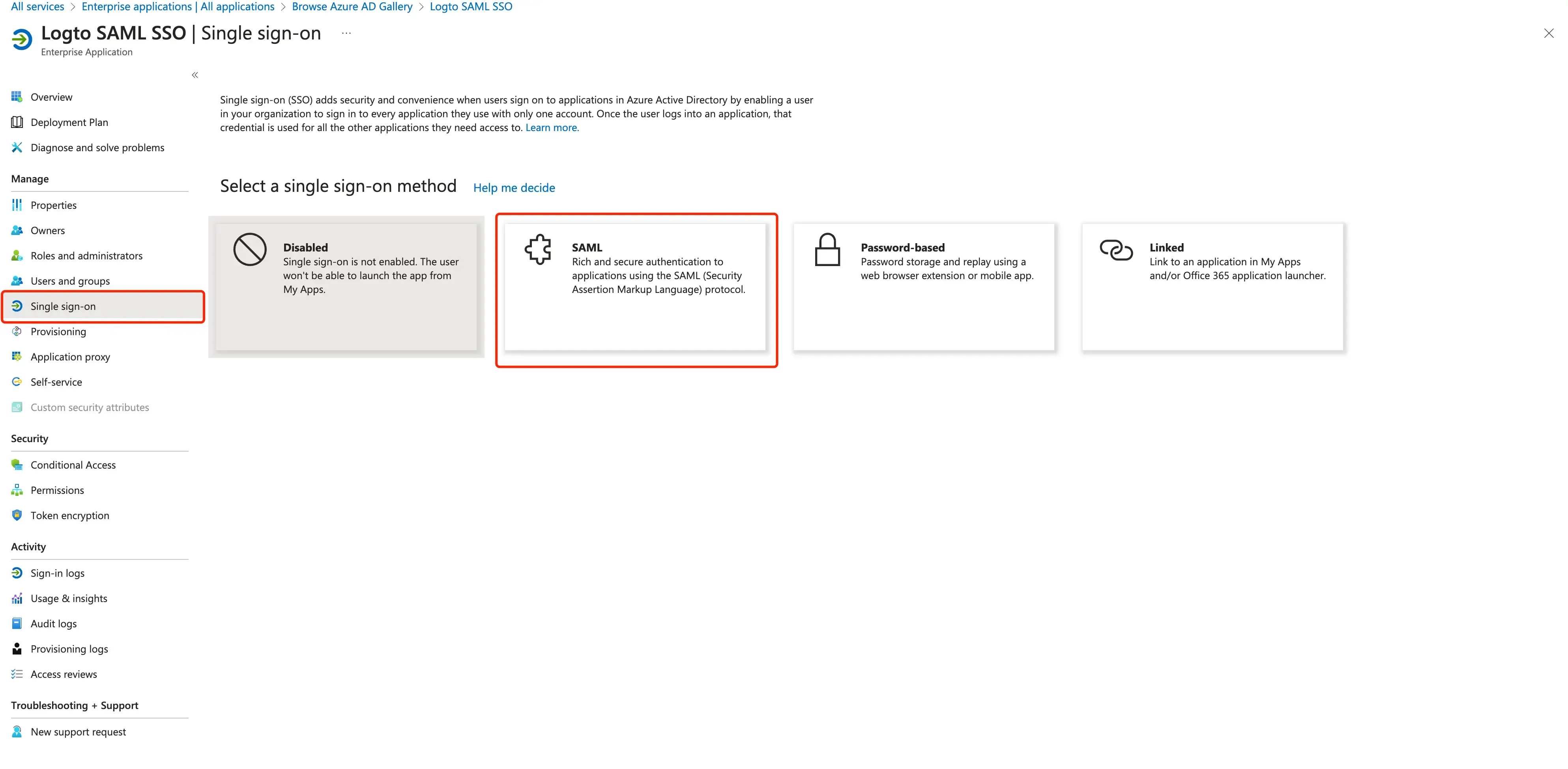
Init a SAML application.
-
Fill in the configuration with
EntityIdandACS URLyou have set in Logto.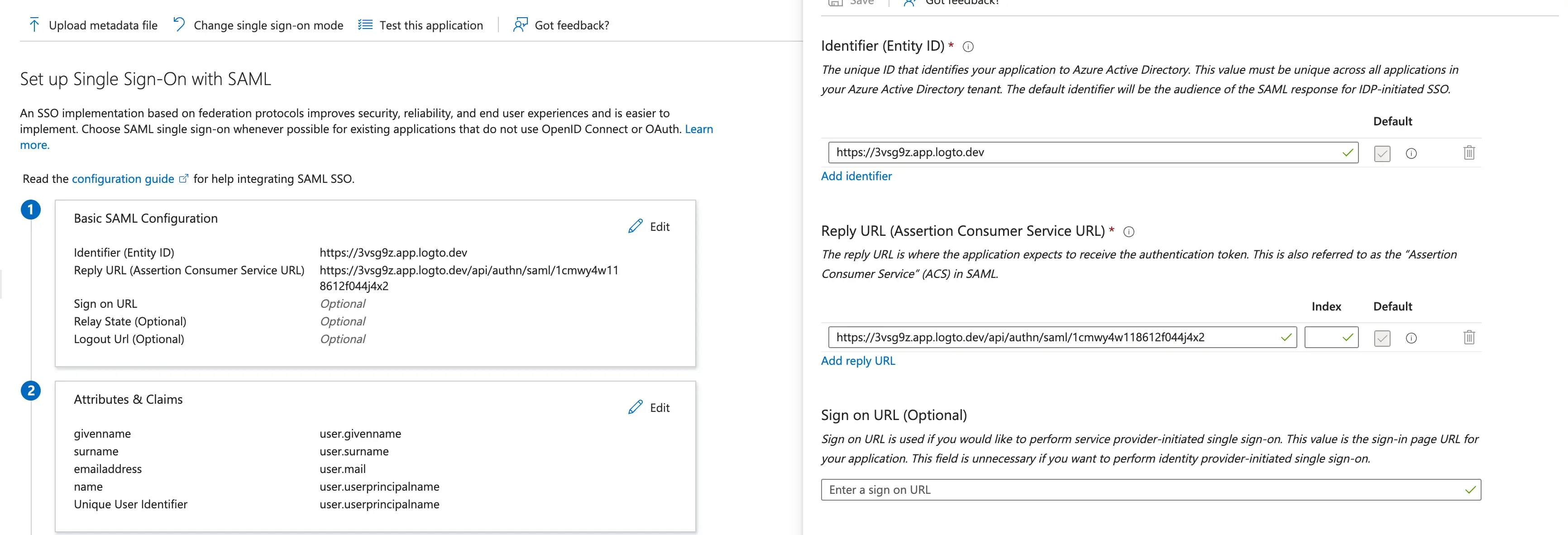
-
Configure user attributes and claims
You can configure the user attributes by clicking on the "Edit" button in the "User Attributes & Claims" section.
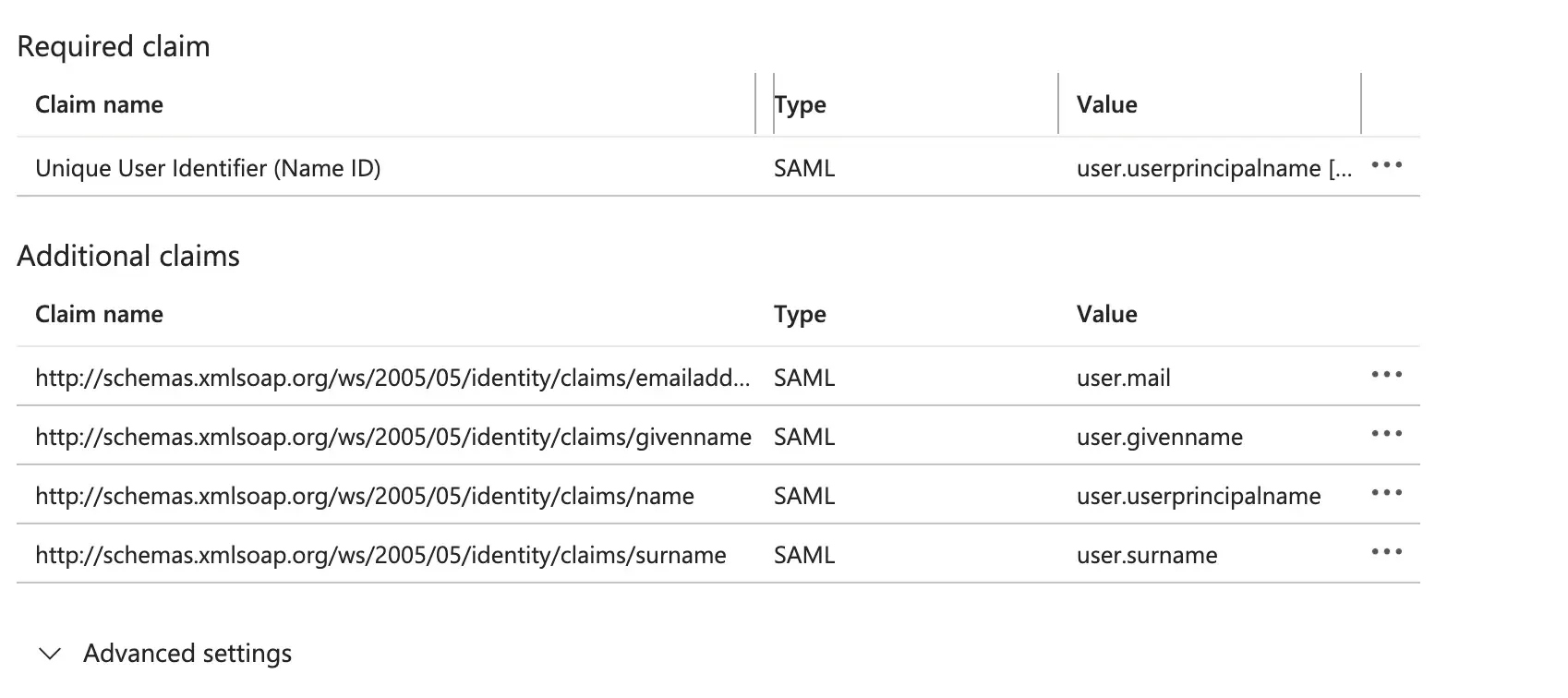
Logto requires the following basic user attributes to be sent in the SAML assertion:
Claim Name Attribute Name http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddressuser.mail http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameuser.name -
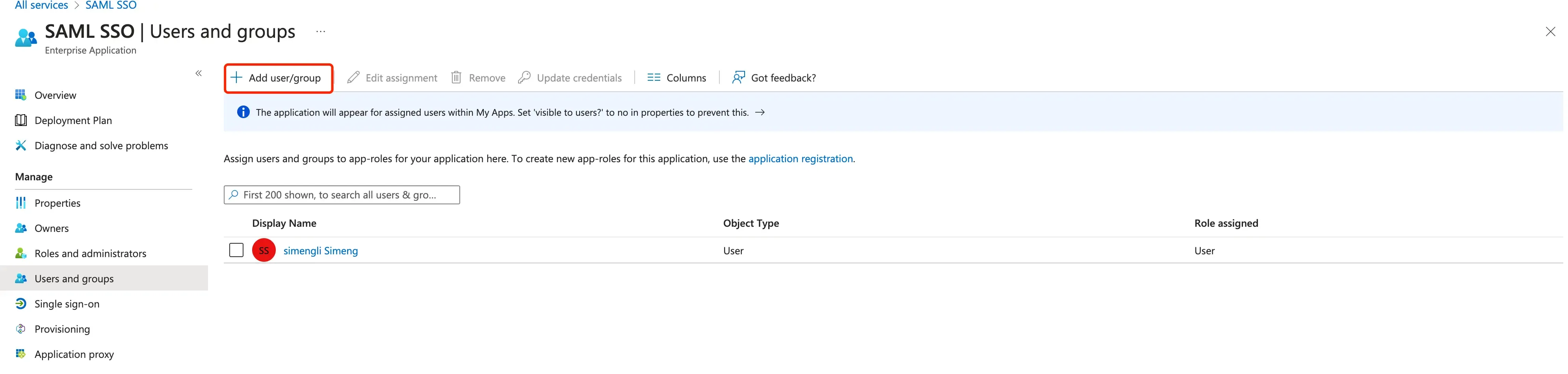
Assign groups and users to the SAML application In order for users or groups of users to be authenticated, we will need to assign them to the AzureAD SAML application. Select “Users and groups” from the “Manage” section of the navigation menu. The select “Add user/group”.
-
Obtain the AzureAD IdP details by downloading certificates and metadata file. Download the
Federation Metadata XMLfile and theCertificate (Base64)file by clicking on the "download" button. You will need these files to complete the SAML connector creation in Logto.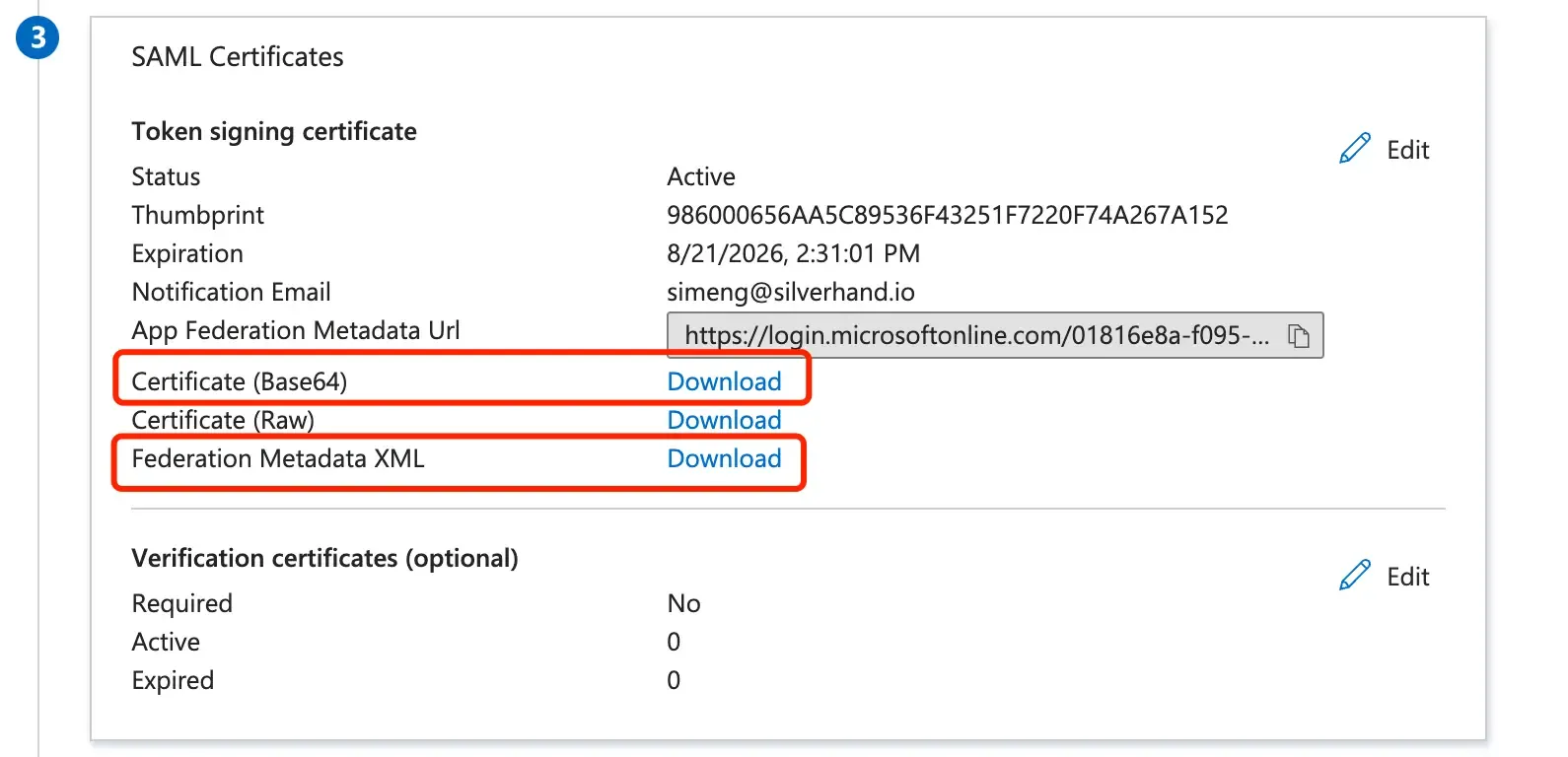
Finish the SAML connection creation back in Logto
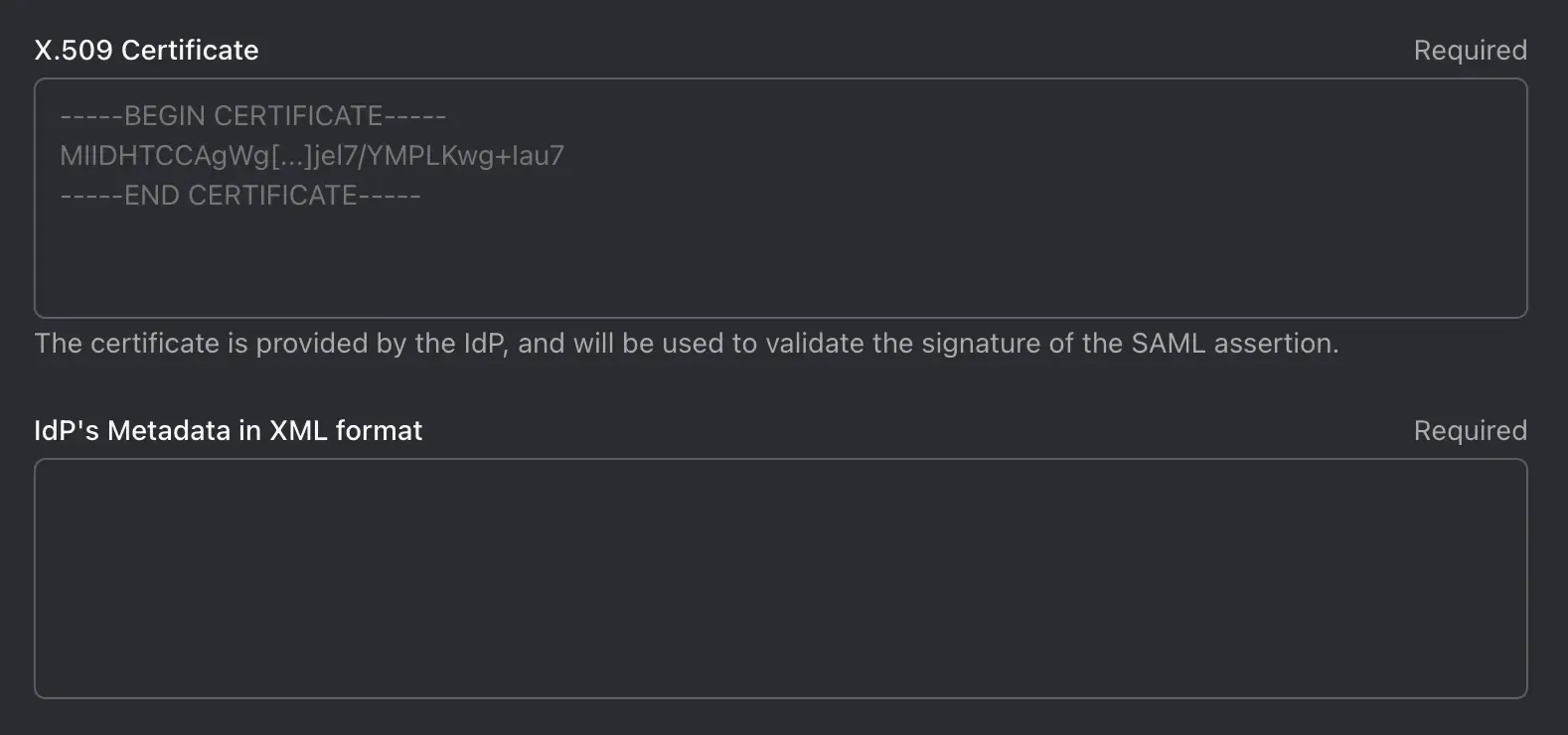
Switch back to the Logto Cloud Console's SAML connector creation form and continue fill in the IdP details. Copy the IdP metadata XML file content to the IdP metadata field. Paste the IdP certificate to the IdP certificate field.
Set the user profile mapping
Based on the AzureAD user claim settings, you may proceed set the key mapping configs in Logto:
Logto available user fields are:
Click on “Save and Done”.
Enable the SAML connector
Once you have finished the SAML connector creation, you can enable the connector by navigating to the "Sign-in experience" section and add the connector as the "Social sign-in" method:
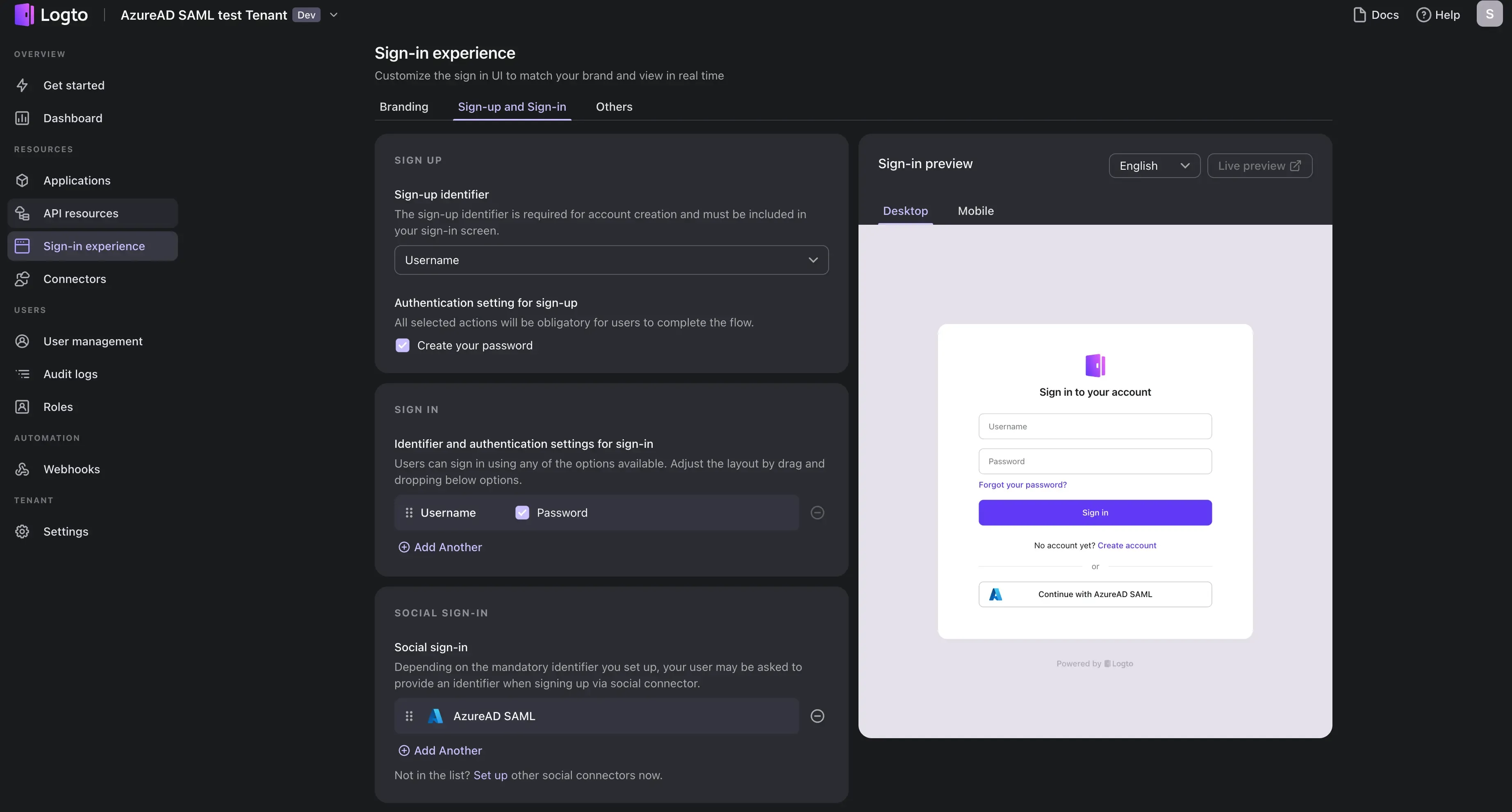
Verify your AzureAD SSO sign-in using our preview demo-app:
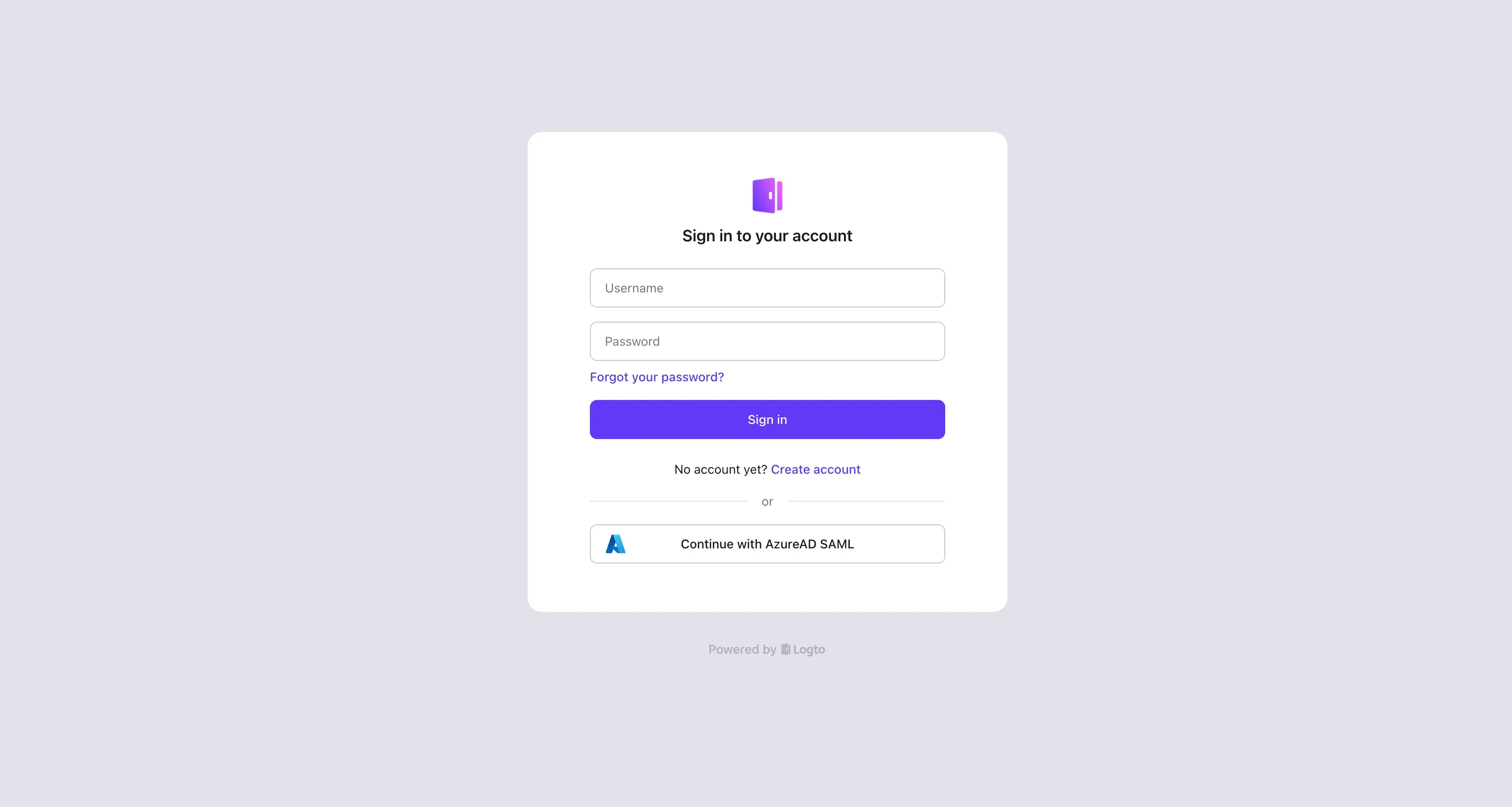
Congratulations! You have successfully integrated AzureAD SSO with Logto. You can now use AzureAD to sign in to your Logto account.

