Organization and Role-based access control: How to design your authorization model for your product
What is organization
Definition
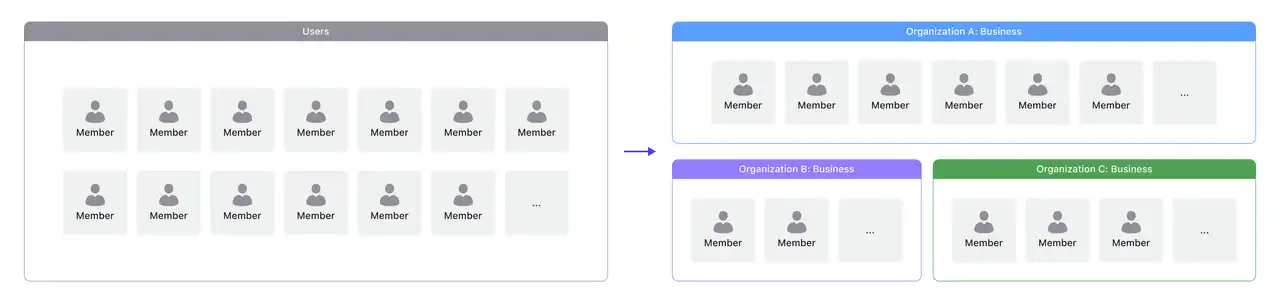
The organization is a group of users(identities) and can represent the teams, business customers, and partner companies who can access your application.
Organization is particularly effective in business-to-business (B2B) settings. In contrast to individual consumers, business clients often consist of teams, organizations, or entire companies, rather than just one person. The introduction of an organization as an entity is important, as it not only groups users but also provides a context for tenant isolation in multi-tenant apps.
Use cases
With this fundamental element, you can now build the must-have features for your B2B products:
- Build a multi-tenant architecture to isolate clients’ data and resources.
- Application access levels are defined by roles assigned to organization members.
- Provisioning members on an invitation and just-in-time basis.
- Organizations can each have a single sign-on (SSO) authentication experience.
What is role-based access control?
Definition
Role-Based Access Control (RBAC) is a method of assigning permissions to users based on their roles. Role-based access control is a policy-neutral access control mechanism defined around roles and privileges. The components of RBAC such as role permissions, user-role, and role-role relationships make it simple to perform user assignments. A study by NIST has demonstrated that RBAC addresses many needs of commercial and government organizations.
Use cases
Previously, we've developed several guides to help you use RBAC to meet your business requirements. Take a look at these easy-to-follow tutorials to get started quickly.
🔐 Role-Based Access Control (RBAC) | Logto Docs
Using different authorization models in Logto for best practice
Role-based access control and organization are key components of Logto's authorization features. As a comprehensive identity management platform, Logto offers tailored solutions for various scenarios and layers, catering to developers and businesses for diverse product architectures.
API role-based access control
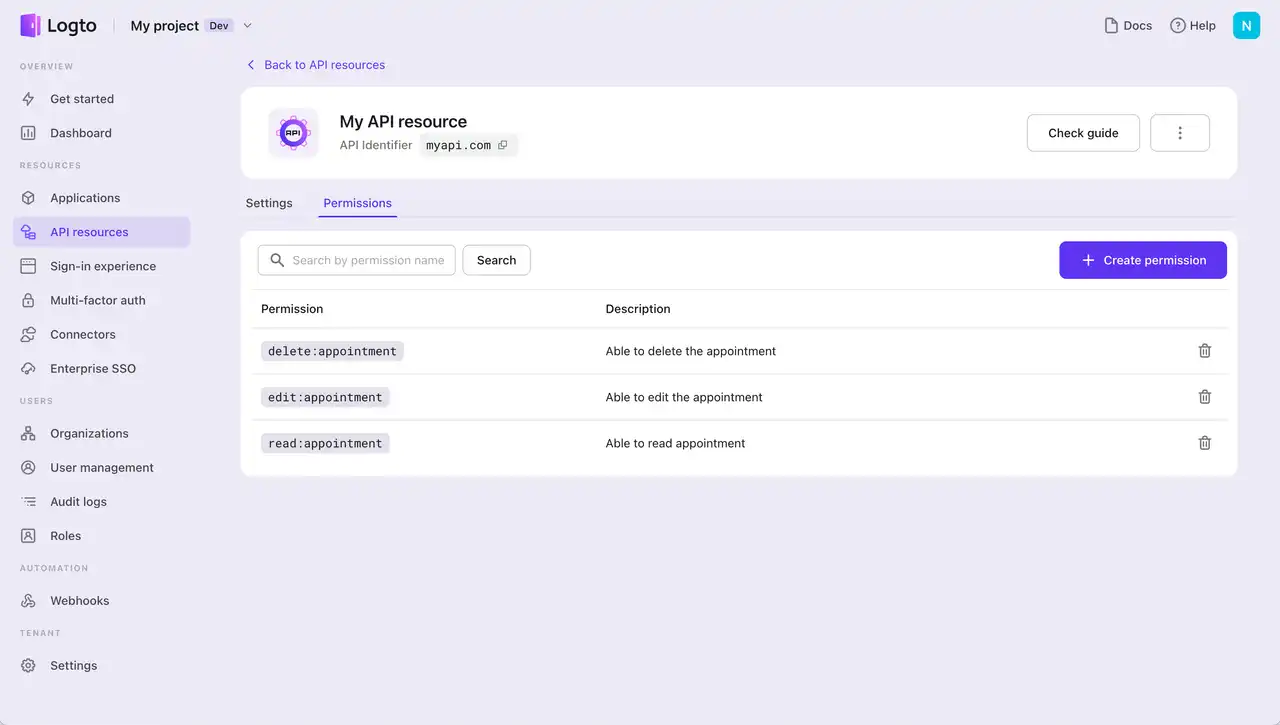
To protect general API resources that are not specific to any organization and don’t need context restrictions, the API RBAC feature is ideal.
Just register the API and assign permissions to each resource. Then, control access through the relationship between roles and users.
API resources, roles, and permissions here are “democratized” under a unified identity system. This is pretty common in the B2C product with less hierarchy and doesn’t need a very deep level of data isolation.
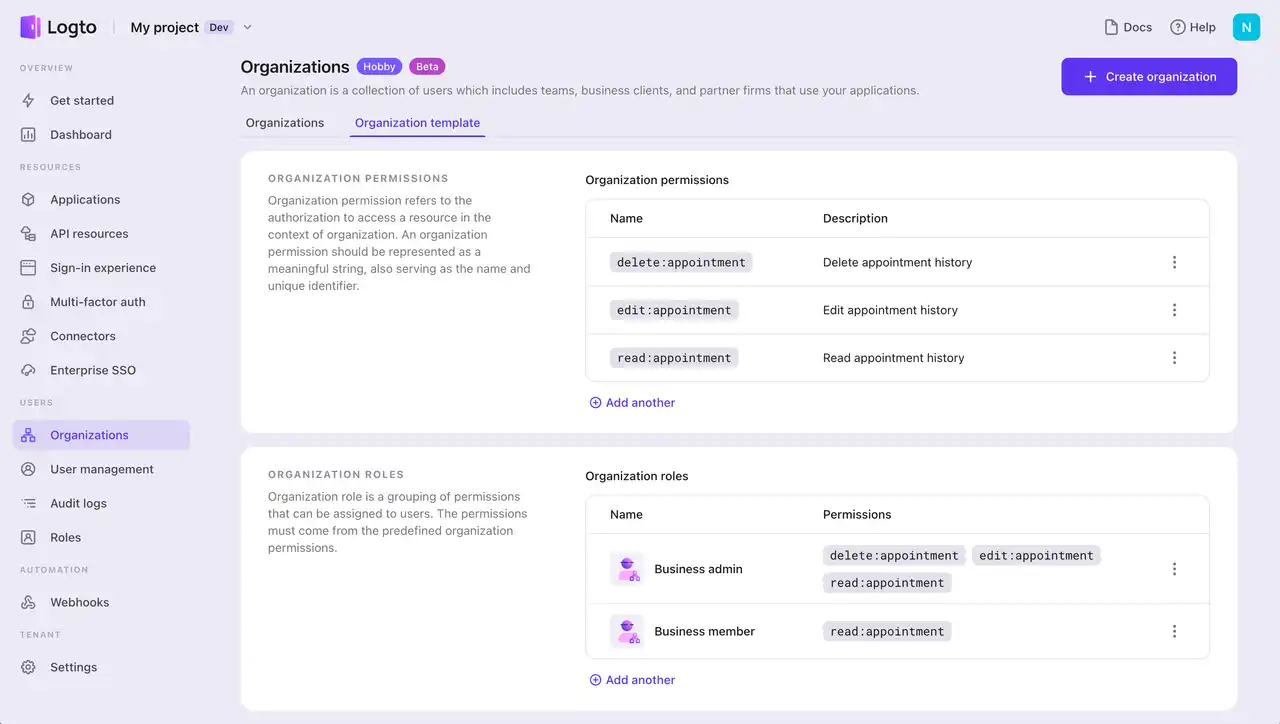
Organization role-based access control
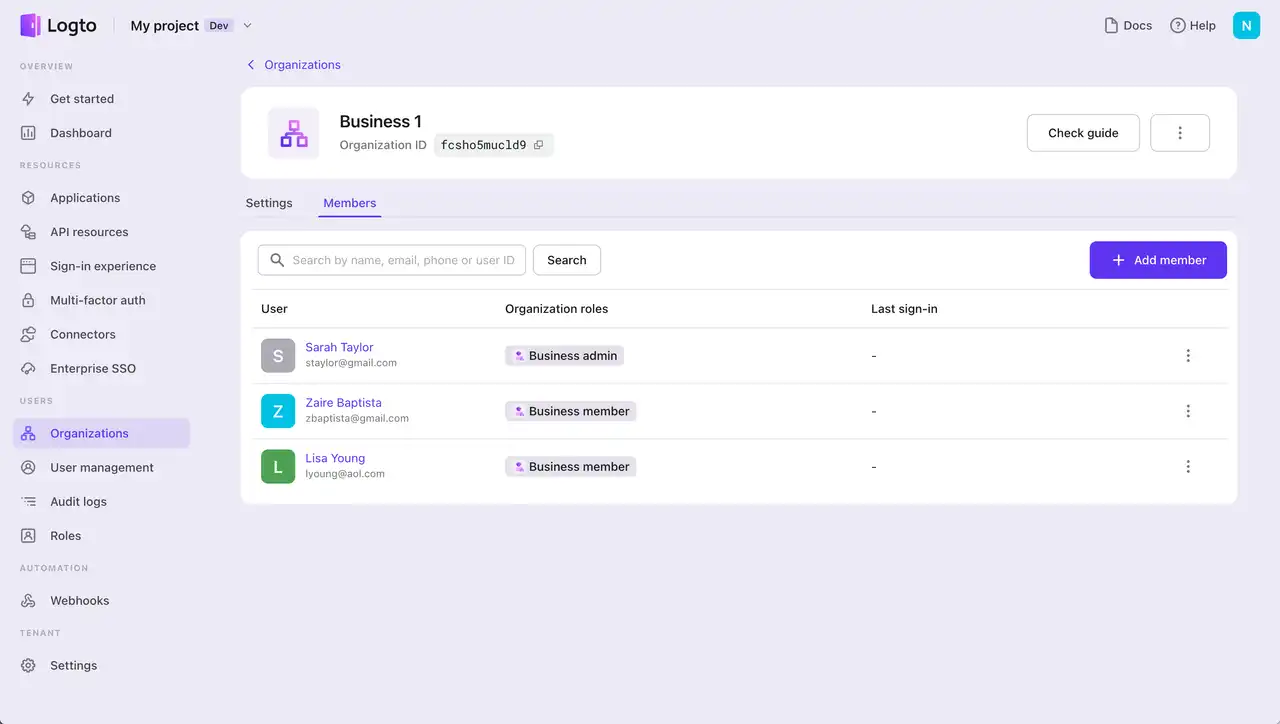
In the B2B and multi-tenant environment, tenant isolation is necessary. To achieve this, organizations are used as a context for isolation, meaning RBAC is effective only when a user belongs to a specific organization.
Organization RBAC focuses on controlling access at the organization level rather than the API level. This provides significant flexibility for organization-level self-management in the long run but still within a unified identity system.
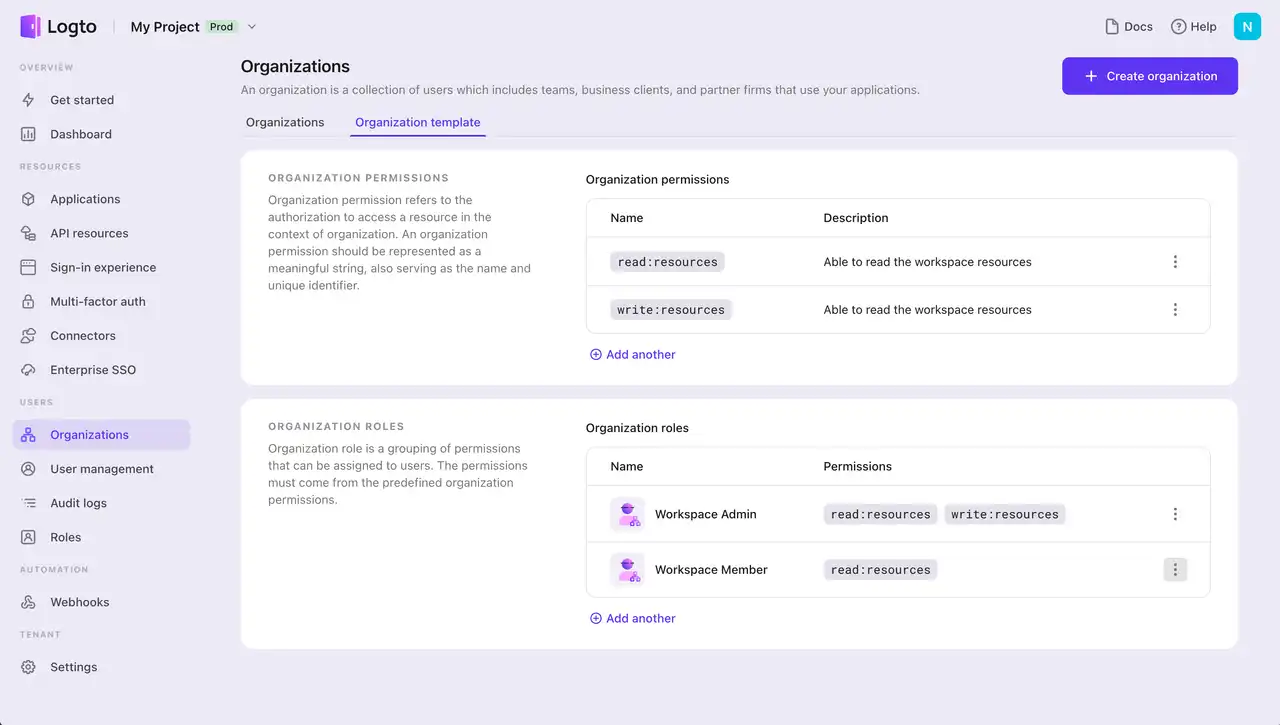
A key feature of organization RBAC is that roles and permissions are generally the same across all organizations by default, which makes Logto “organization template” extremely meaningful for improving development efficiency.
This aligns with the shared philosophy of multi-tenant apps, where access control policies and identities are common infrastructure components across all tenants (app tenants), a common practice in SaaS products.
Choosing and designing the appropriate authorization model
When selecting the right authorization model, consider these questions:
- Are you developing a B2C, B2B, or a combination of both types of products? Are identities considered as business identities?
- Does your app need a multi-tenant architecture?
- Is there a need for a certain level of isolation in your app, as determined by the business unit?
- What permissions and roles need to be defined within the context of the organization, and which ones are not?
A B2C app
Let's use a web application example: BookHarber, an online bookstore. BookHarber offers a wide range of features for customers and staff, ensuring a seamless and secure shopping experience.
Key features of BookHarber include:
- Browsing and Purchasing Books: Users can easily search for and purchase books from a diverse collection, spanning various genres and authors.
- Order Management and Logistics Tracking: Registered customers can manage their orders, track shipping, and receive updates on their purchases.
- Special Offers and Holiday Activities: BookHarber provides exclusive discounts and promotions during special events and holidays to engage and reward its customer base.
- Customer Support: Customers can open support tickets to address any concerns or issues they may encounter, receiving prompt assistance from BookHarber staff.
- Customer Management: Staff members with different roles have the ability to manage various aspects of the platform, such as customer accounts, order processing, and issue resolution.
Roles
In the BookHarber ecosystem, we can identify several key user roles, such as:
- Guest: Unregistered users who can browse the website, search for books, and view special offers.
- Customer: Registered users who can purchase books, manage orders, track logistics, and open support tickets.
- Store Admin: Staff members responsible for overseeing the overall management and operations of the platform. With full access.
- Books Manager: Staff members in charge of book and category management.
- Customer Service Agent: Staff members tasked with responding to support tickets.
- Third-Party Logistics Provider: External partners responsible for managing and tracking the shipping and delivery of orders.
- Marketing Staff: Staff members responsible for promoting BookHarber, responsible for managing special offers and events.
Previously, we've developed several guides to help you use RBAC to meet your business requirements. Take a look at these easy-to-follow tutorials to get started quickly.
Mastering RBAC in Logto: A Comprehensive Real-World Example
B2B app
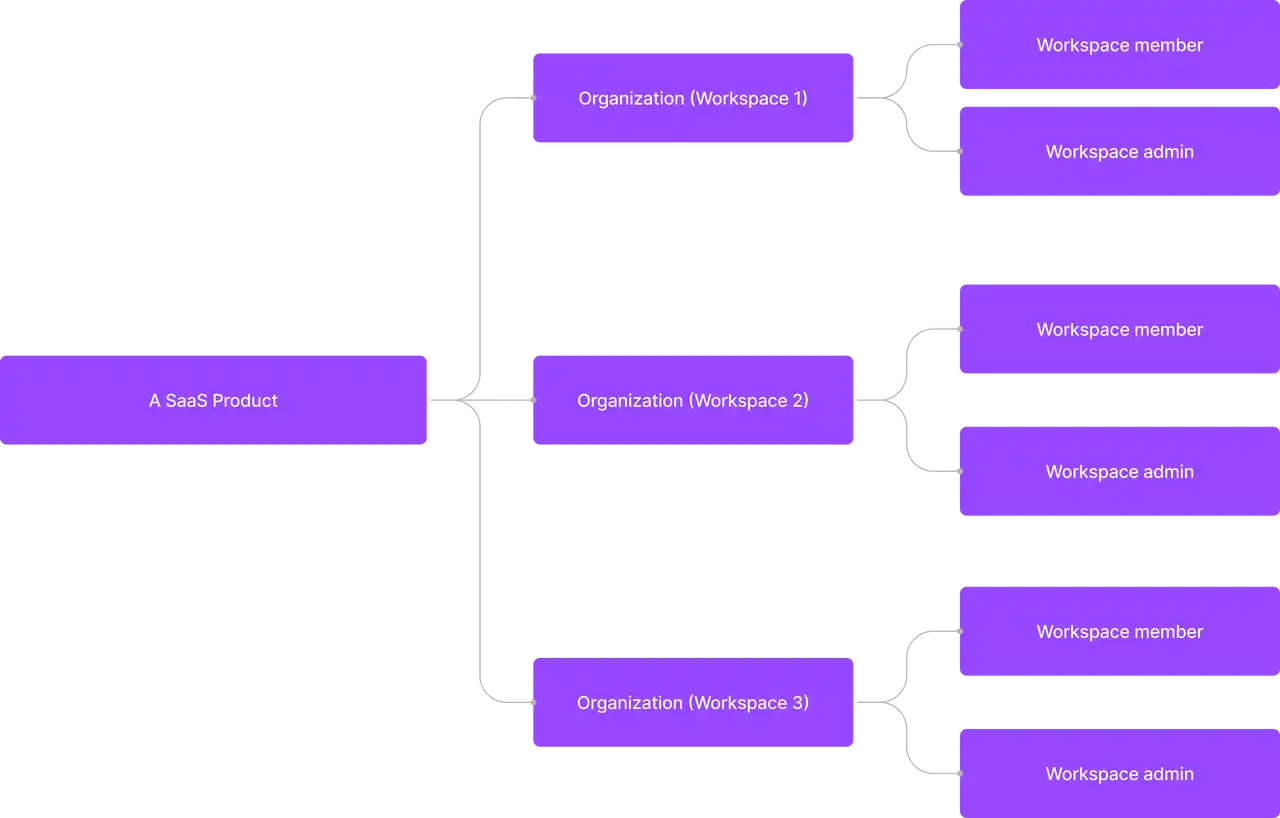
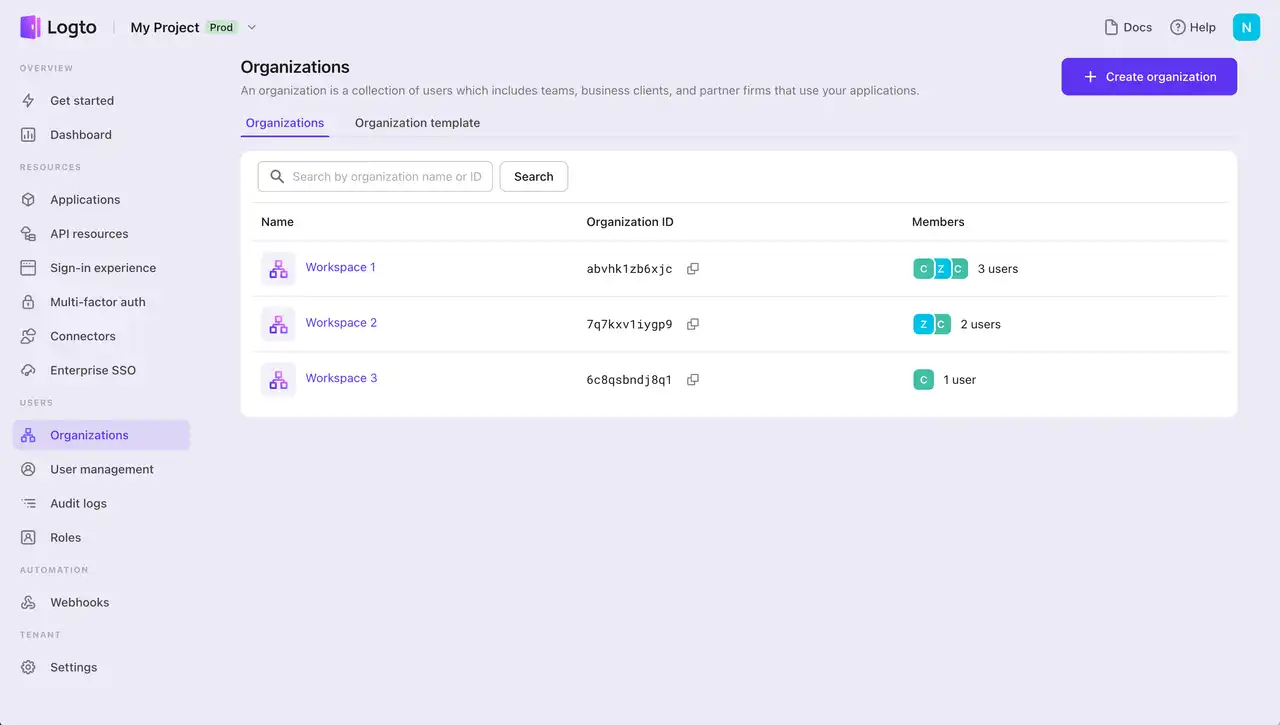
Multi-tenant apps often find their place in business-to-business (B2B) solutions like productivity tools, enterprise resource planning (ERP) systems, and other software-as-a-service (SaaS) products. In this context, each "tenant" typically represents a business customer, which could have multiple users (its employees). Additionally, a business customer might have multiple tenants to represent distinct organizations or business divisions.
Create a few organizations
Define organization template for organization-level access control
Hybrid B2B & B2C app
B2B applications go beyond SaaS products and often involve the use of multi-tenant apps. In B2B contexts, these apps serve as a common platform for various teams, business clients, and partner companies to access your applications.
For instance, consider a ride-sharing company that provides both B2C and B2B apps. The B2B apps serve multiple business clients, and employing a multi-tenant architecture can help the management of their employees and resources. To illustrate, if the company wishes to maintain a unified user identity system, it can design an architecture like the following example:
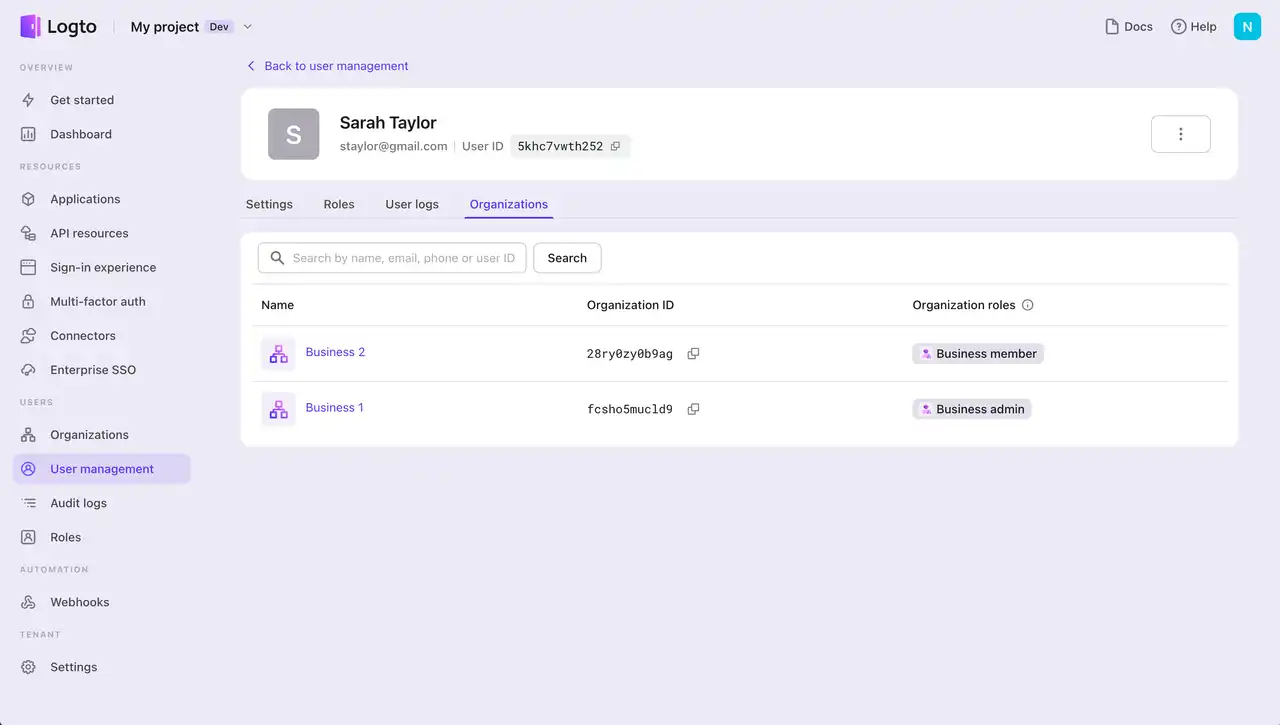
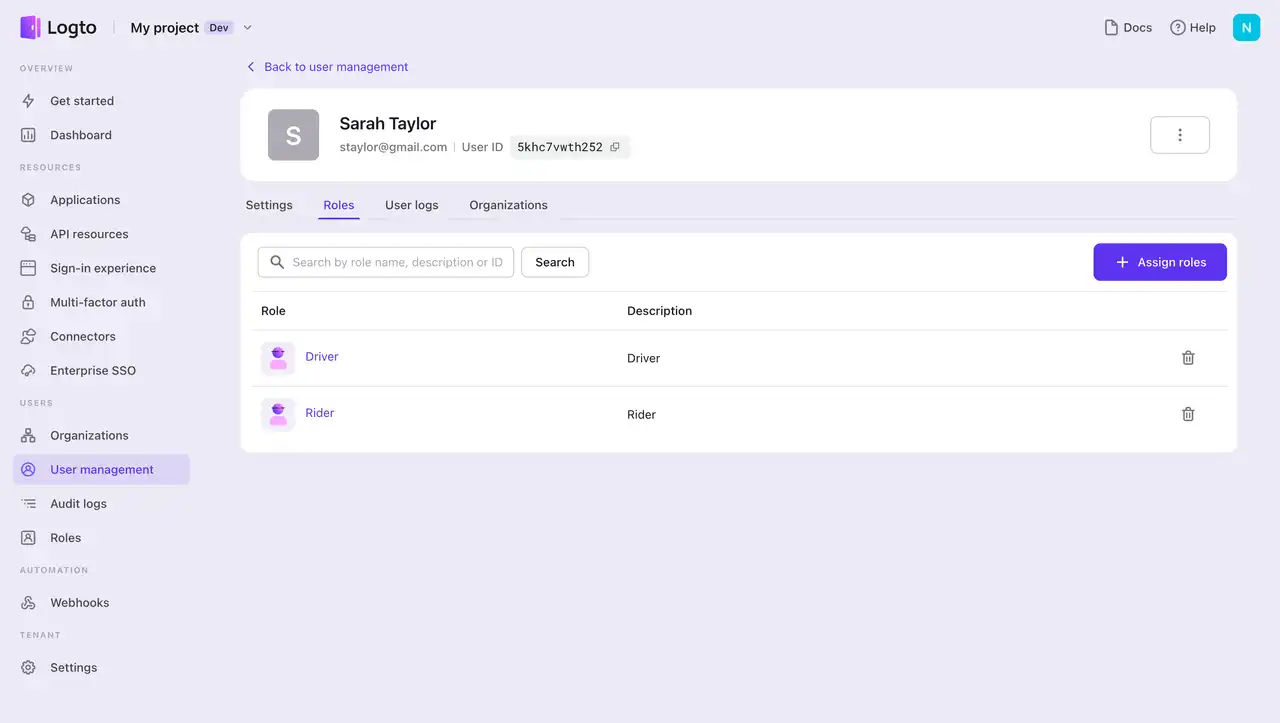
Let's use Sarah as an example. Sarah has both a personal and a business identity. She uses the ride-sharing service as a passenger and also works as a driver in her spare time. In her professional role, she also manages her own personal business and uses this business identity to be a partner with Business 1.
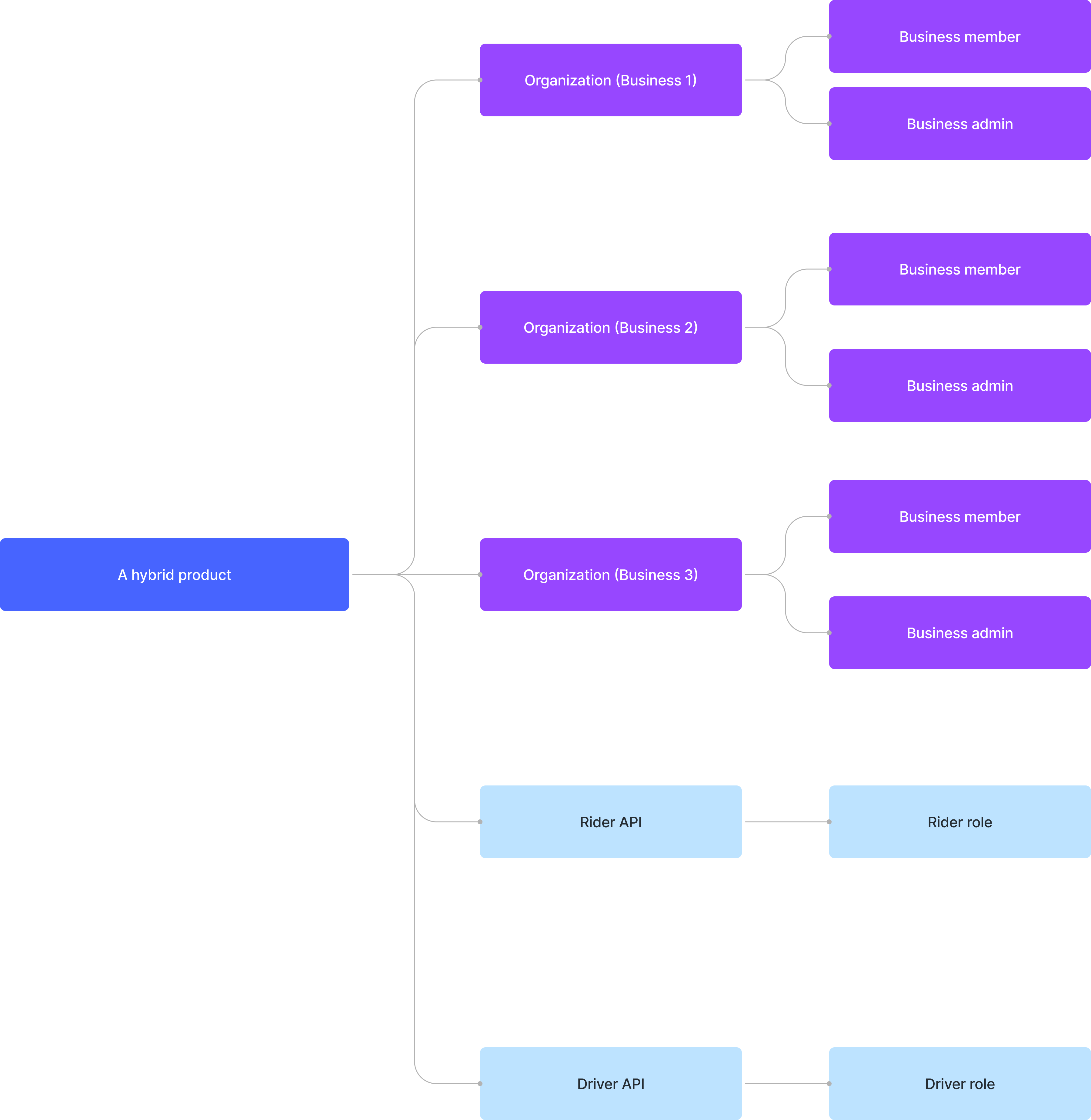
Entities set up in Logto
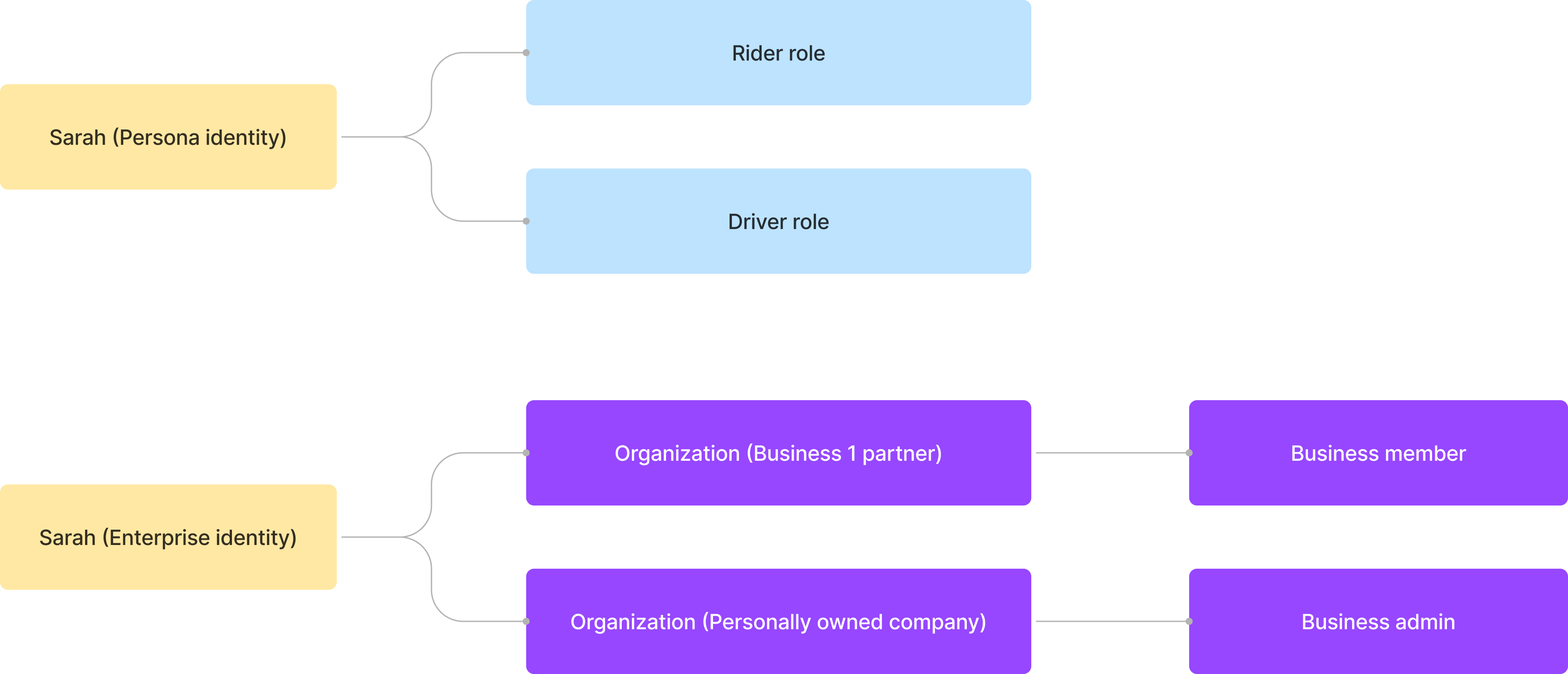
A user’s identity and role map
Define API resources, user roles
Set up organizations
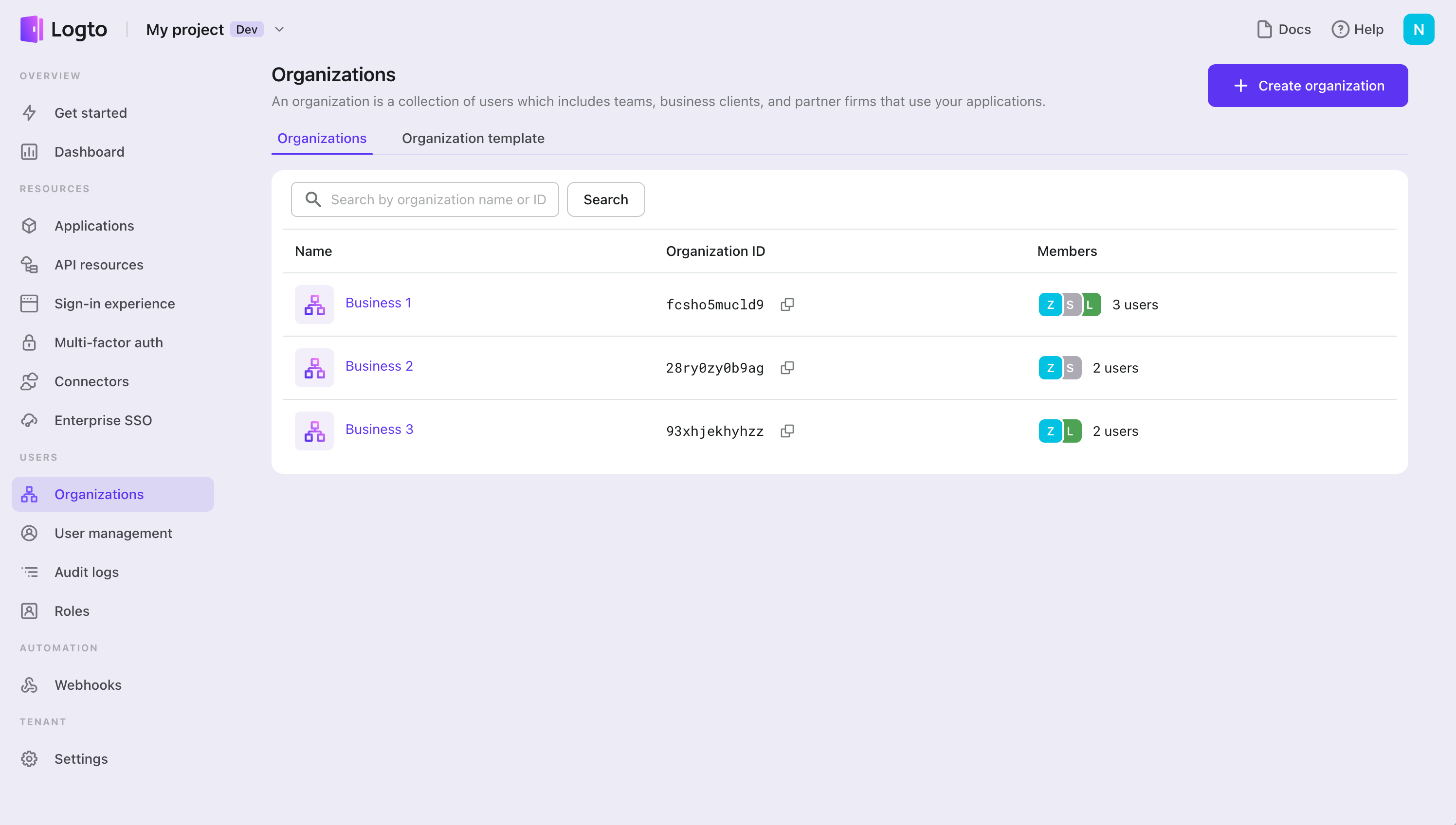
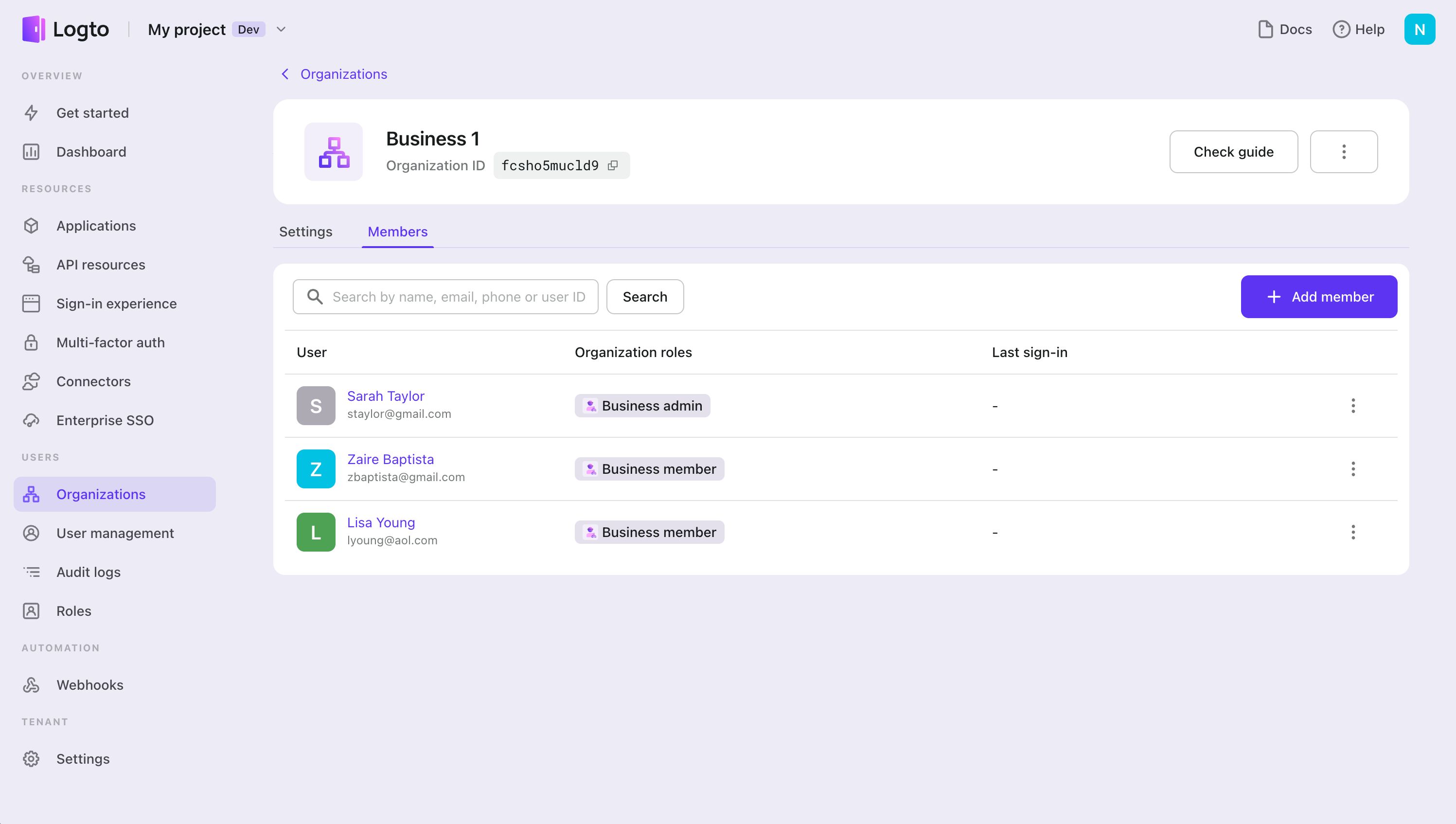
Sarah’s profile
Build your authorization today.
Logto offers both Role-Based Access Control (RBAC) and Organization features to meet your authorization requirements. These features are designed to be easily integrated into various parts of your product. For more information, take a look at our sections on organizations and RBAC, or you can try out Logto right now.