WebAuthn and Passkey 101
Gain a comprehensive understanding of WebAuthn, including its concept, workflow, reasons for its popularity, and associated challenges.
WebAuthn ranks among the most secure authenticators in NIST AAL standards. Introduced in 2013, it's the favored choice of businesses for authentication now. However, its adoption isn't widespread yet, leading to many inquiries about WebAuthn and Passkeys. Let's dive into what you should know.
Concept: What’s the relationship between WebAuthn, Passkey, and FIDO?
| FIDO Alliance | FIDO Alliance is an organization for providing open-source and secure passwordless authentication standards, including UAF, U2F, and FIDO2. |
| FIDO2 | FIDO2 is a set of standards for secure online authentication developed by FIDO Alliance. FIDO2 comprises two main components: WebAuthn for passwordless logins and CTAP for secure device communication. |
| Passkey | A passkey is a FIDO-based, phishing-resistant credential to replace passwords.
|
| WebAuthn | WebAuthn, a JavaScript API developed by the W3C and FIDO Alliance, empowers web applications authentication with FIDO2 standards. Passkey is one of the authentication methods WebAuthn supports. |
Flow: How does WebAuthn work?
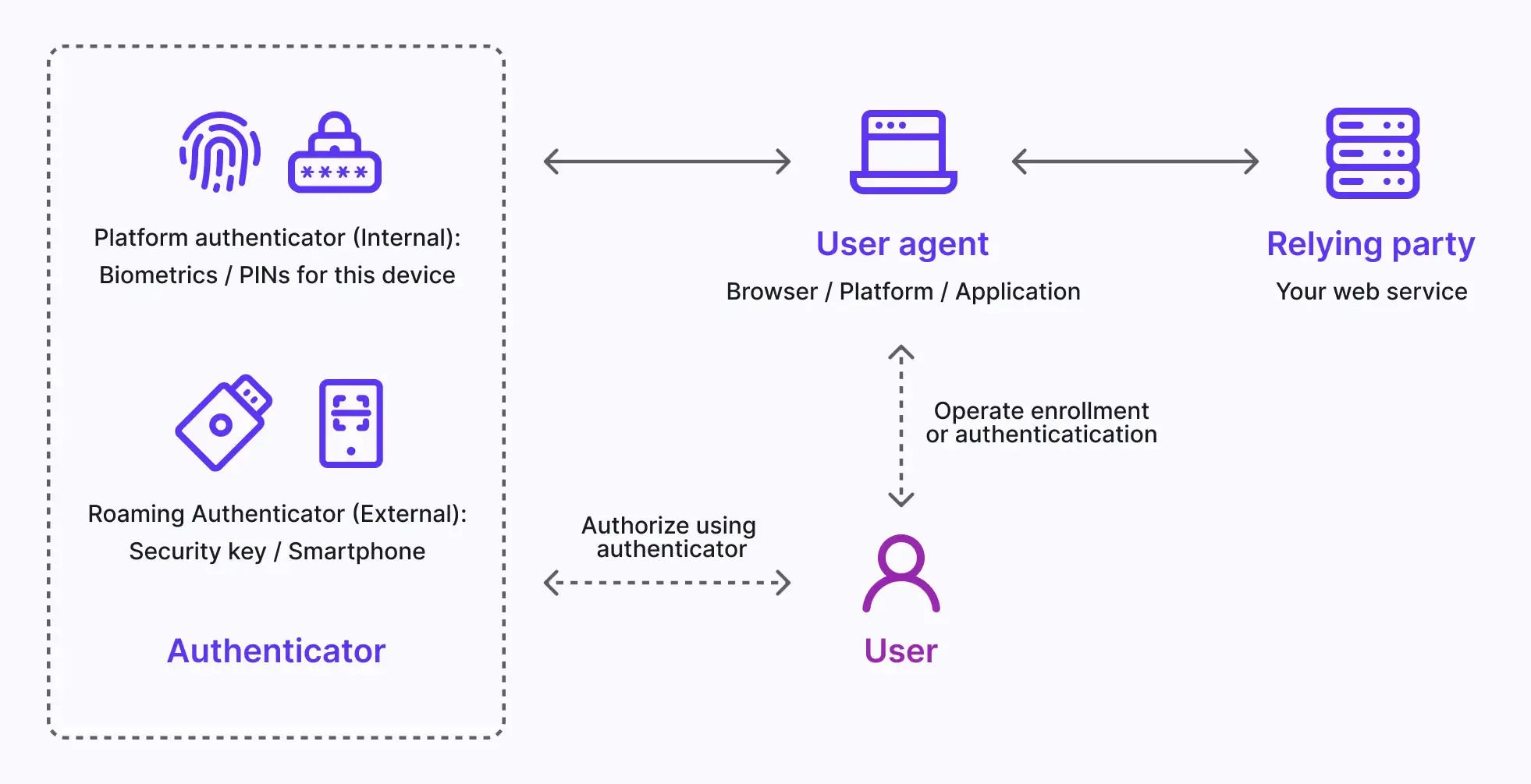
4 main entities of WebAuthn
Basically, you may know the 4 main entities involved in WebAuthn flow.
-
User: The person that enrolls or authenticates to the web application using WebAuthn.
-
User Agent: The web browser that handles the WebAuthn API calls, and manages the authentication process between all different relying parties and authenticators.
-
Relying Party: Your web service or application that the user is trying to access. The user interacts with the Rely party through the User Agent.
-
Authenticator: The hardware component the user possessed for verifying the user’s identity. It can take various forms based on the platform or browser capability, such as security keys (like Yubikeys), phones or tablets (connected by Bluetooth, NFC, or USB), device-based biometrics or PINs, etc.
Workflows of WebAuthn
Asymmetric public-key cryptography is the core process.
- Key pair generation: The User Agent generates a public-private key pair. The public key is shared with the Relying Party, while the private key remains securely stored in the user's Authenticator.
- Authentication Challenge: When the user attempts to log in, the Relying Party sends an authentication challenge to the User Agent.
- User Verification: The User Agent sends the challenge to the Authenticator, which interacts with the user for verification (e.g., biometrics or a button press).
- Cryptographic Signature: The Authenticator uses its private key to sign the challenge, creating a cryptographic signature.
- Verification and Access: The User Agent verifies the signature using the public key and informs the Relying Party of a successful authentication. Access is granted.
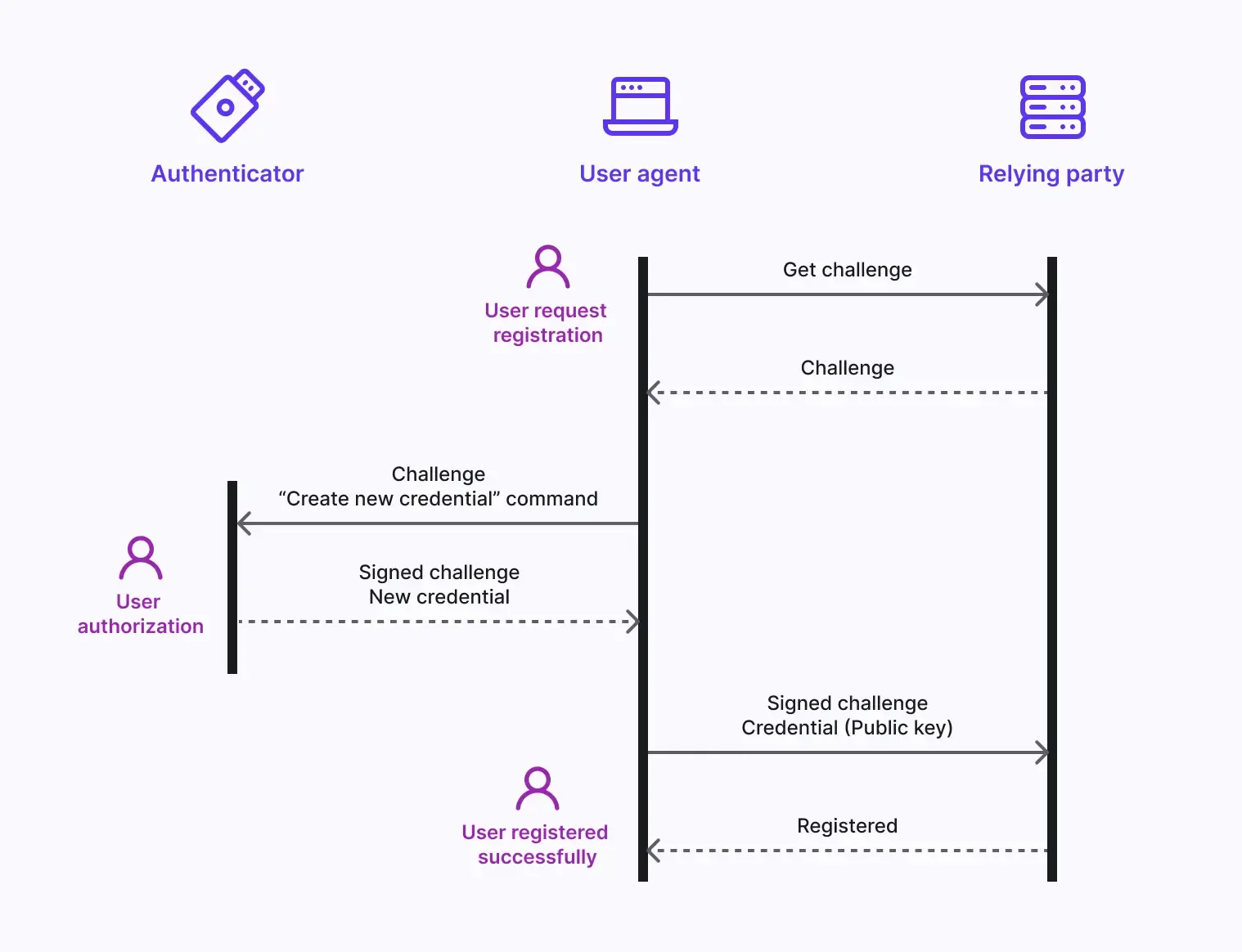
To elaborate, divide it into the enrollment and authentication phases.
The WebAuthn enrollment flow:
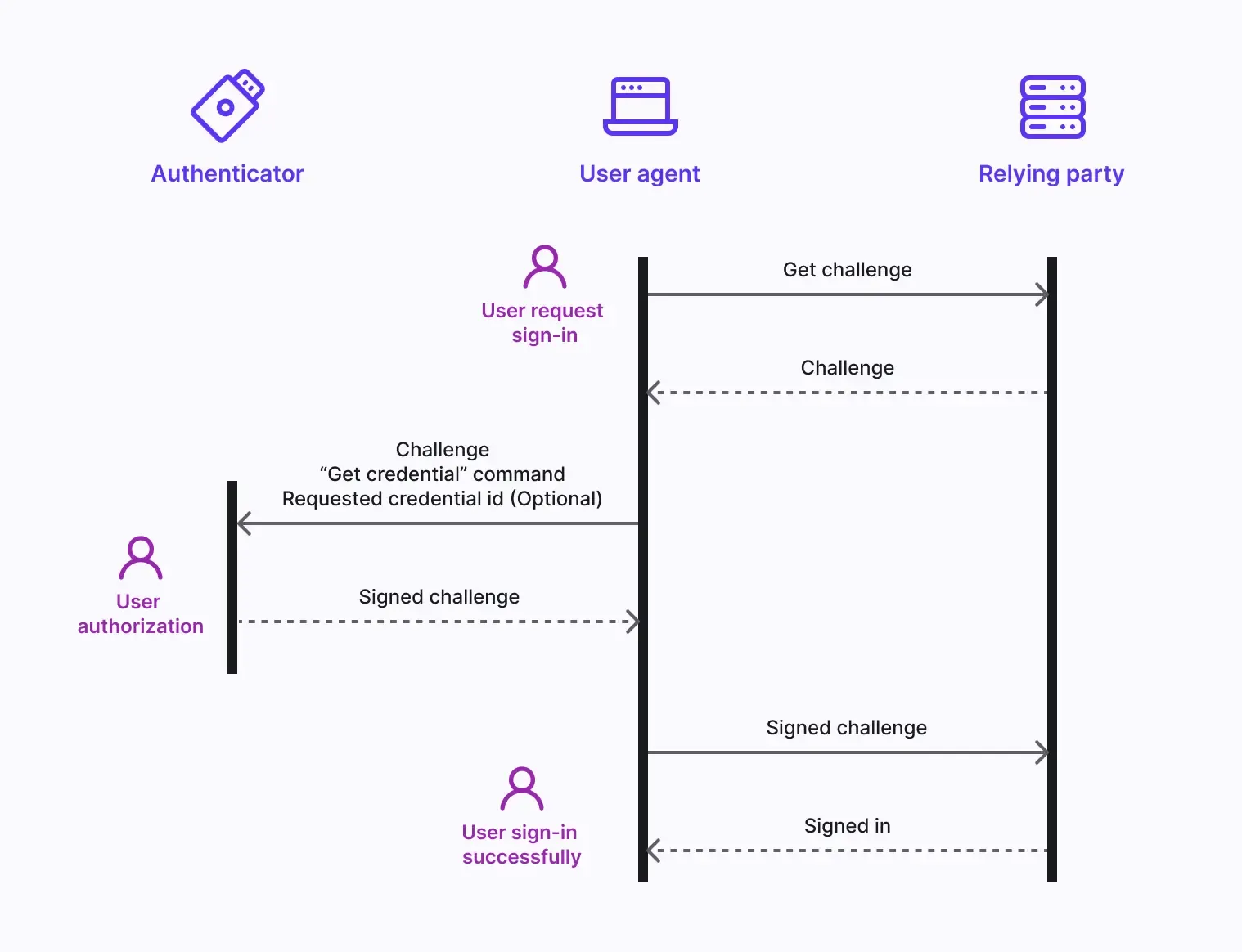
The WebAuthn authentication flow:
Advantages: Why is WebAuthn becoming a trend?
Multiple authenticators
You have the option to choose from multiple authenticators for added flexibility. These authenticators come in two types, for both local and cloud use, and you can enable one or both for your service.
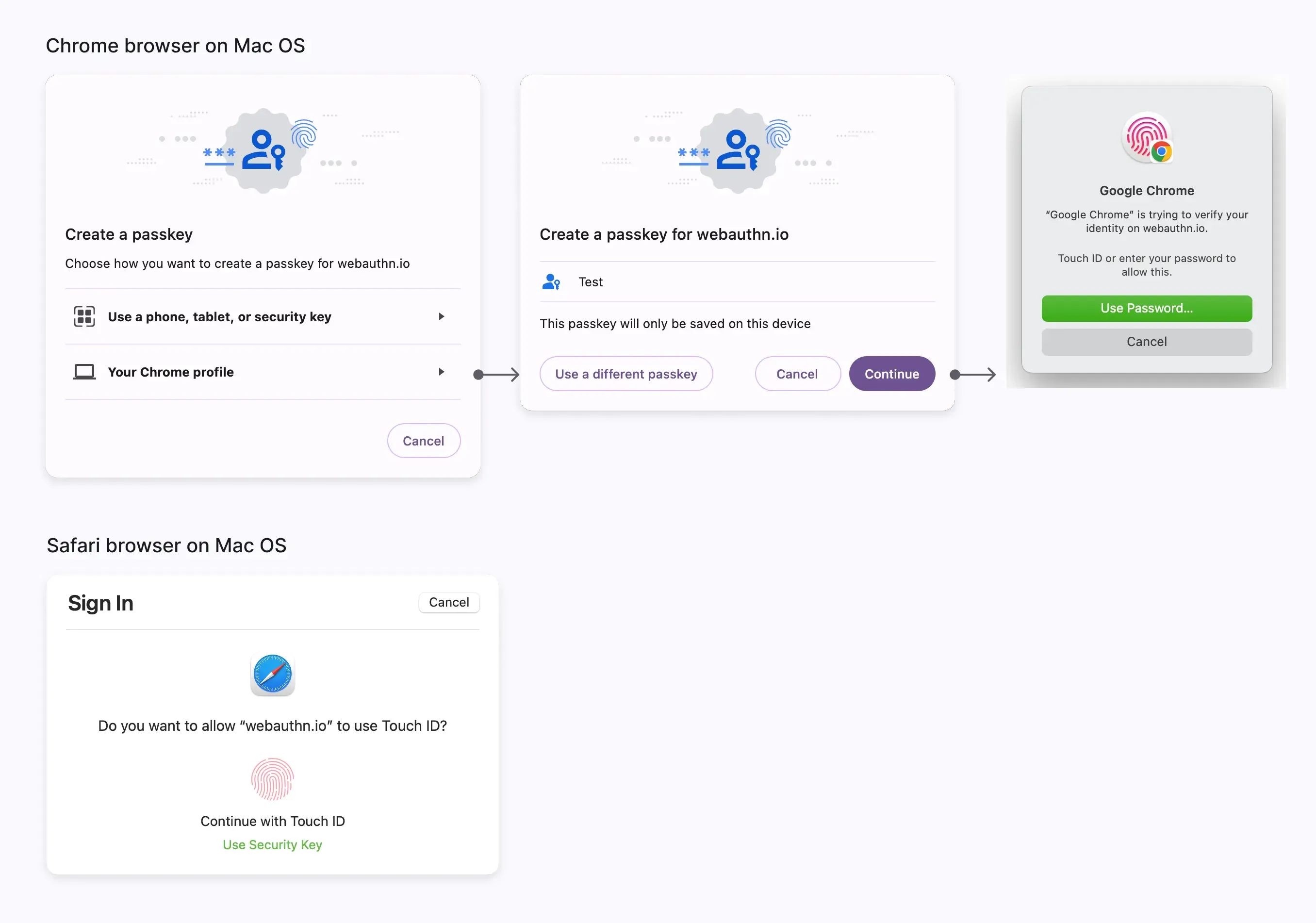
Platform authenticator (Internal authenticator)
The platform authenticator is tied to a single and specific device OS, such as a computer, laptop, phone, or tablet, which the user signs in with. It works exclusively on the device for authorization using methods like biometrics or a device passcode. It's a quick way to authenticate, especially with biometrics, and can replace the need for manual password entry. However, if the user loses the device, it can become a barrier to access. For example:
- MacOS and iOS: iCloud Keychain verified by Touch ID, Face ID, or device passcode.
- Windows: Windows Hello verified by facial recognition, fingerprint, or friendly PIN.
- Android: Google Password Manager also supports facial recognition or fingerprint to autofill passwords to authorize devices.
Roaming authenticator (External authenticator, Cross-platform authenticator)
The roaming authenticator is a separate, portable device or software application, such as a hardware security key or a smartphone. It should link the device using USB or keeping NFC or Bluetooth on. The roaming authenticator is not limited to a single device or browser, providing greater flexibility. For example:
- Security keys: also called Hardware tokens, like Yubikey.
- Mobile smartphone: like using a cloud-based Google account on Android, or an iCloud account on iPhone. Importantly, cross-device authentication also needs to connect with Bluetooth, NFC, or USB to ensure the user's authenticator is nearby. Mobile authenticators often require QR code scanning to link them with desktop devices. (Android phones, in particular, can use Persistent Linking to seamlessly link with the Chrome browser for one-click authorization without the need for QR code scanning.)
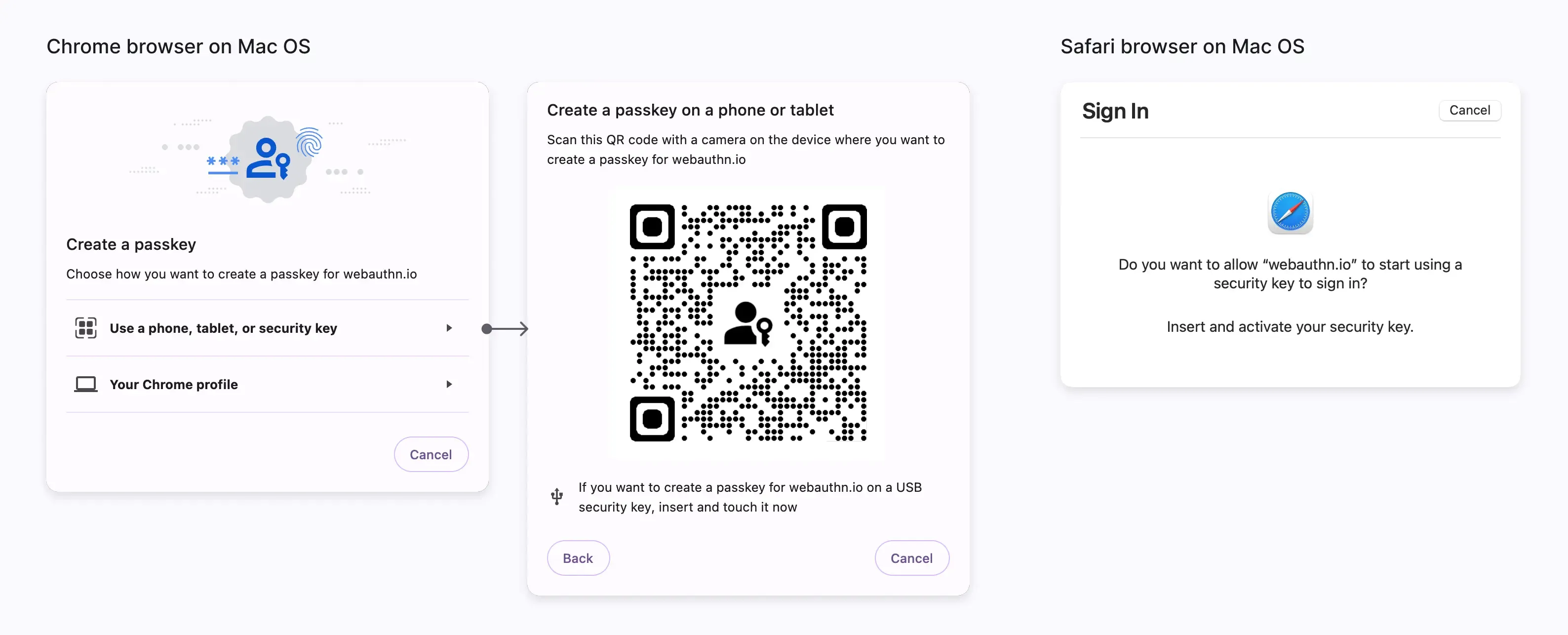
High assurance security
High assurance security is essential for safeguarding business resources. This is achieved through the following measures:
- Protection of privacy keys: Privacy keys are never shared with third-party websites (Rely Party), which helps guard against password breaches and phishing attempts.
- Device proximity requirement: Devices require either "Platform authentication for a single device" or "Roaming authenticator limited by USB, Bluetooth, or NFC" to be in close proximity to the user, preventing remote attacks.
- Domain Binding: WebAuthn is tightly bound to the specific domain of the user-enrolled website, providing protection against phishing attacks from unauthorized websites.
Frictionless user experience for MFA&1FA
WebAuthn enhances security while elevating the user's passwordless verification experience:
- Native experience and biometrics efficiency: WebAuthn adopts specific authentication methods tailored to various platforms and devices, aligning with user habits. Biometric authentication eliminates the need for manual input, significantly speeding up the verification process.
- Direct MFA skipping 1FA: WebAuthn is commonly used for MFA (Multi-Factor Authentication). Due to its robust security, if the relying party has previously recorded the use of WebAuthn in the browser, users can skip the 1FA (Single-Factor Authentication) step and sign in directly through passkey verification.
- Passkey replacing password: Passkeys can also serve as an alternative to traditional passwords for the 1FA. Users can provide their passkey either before or after entering their account, with password verification only required when passkey authentication is unavailable.
Challenge: Why WebAuthn is not widely adopted by users?
Browser or platform limitations
Some browsers or platforms either do not support WebAuthn at all or lack support for roaming authenticators. While current statistics of Caniuse show decent support, with 97.37% desktop and 96.3% mobile platform coverage, variations still exist across different browser versions and operating systems. For instance, Desktop Linux lacks support for platform authenticators, Android only fully supports WebAuthn on Chrome, and Internet Explorer on MacOS does not support WebAuthn. This necessitates admins to ask members to enforce specific browser or OS choices, or configure other alternative MFA methods.
Device loss risk
Particularly for users relying on "This device" platform authenticators, losing the device can result in a loss of access to their accounts. Account recovery can be a cumbersome process. To mitigate this risk, it's advisable for users to simultaneously bind other backup authentication methods when setting up WebAuthn.
Limited website and app support
Many services and applications do not yet offer support for passkeys. Users often lack familiarity with various authentication methods and may not fully understand the distinctions and limitations between Platform authenticators and Roaming authenticators. However, major systems, browsers, and SaaS services are increasingly adopting WebAuthn, making it a growing trend that both businesses and users are beginning to embrace.
Conclusion
Logto is gearing up to launch the MFA (Multi-Factor Authentication) in November. The initial phase will support three verification methods: Authenticator app TOTP, WebAuthn(Passkey), and Backup codes, offering a comprehensive sign-in and sign-up solution. We'll continue to develop advanced features related to WebAuthn. We look forward to your experience and invite you to stay tuned on Product Hunt for the upcoming MFA release.

