Logto product updates
Time for a new Logto release! This month, we are bringing new features such as Arabic Language translation and full RTL support, personal access token (PAT), configurable first-screen, as well as various improvements and bug fixes.
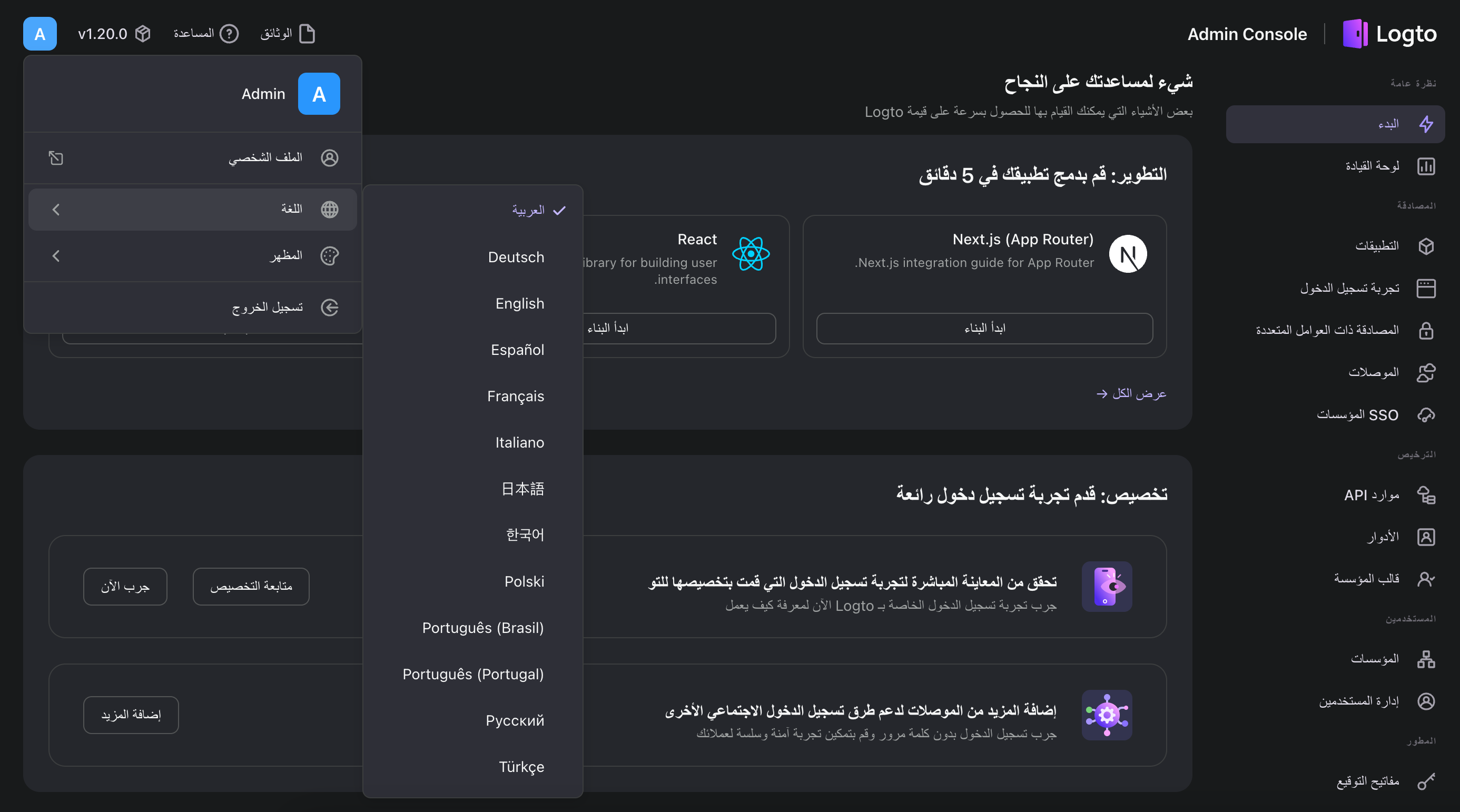
Arabic translation and RTL support
- Added new Arabic language translation to both Console and Experience UI (credit @zaaakher).
- Improved UI layout and details to better support RTL languages.
Personal access token (PAT)
Personal access tokens (PATs) provide a secure way for users to grant access tokens without using their credentials and interactive sign-in.
You can create a PAT by going to the user's detail page in Console or using the Management API POST /users/:userId/personal-access-tokens.
Refer to documentation for more details.
Support additional first-screen options
In addition to sign-in and register, we now enabled more options that allowing developers to customize the initial screen presented to users. These new first-screen options are:
identifier:sign_in: Only display specific identifier-based sign-in methods to users.identifier:register: Only display specific identifier-based registration methods to users.reset_password: Allow users to directly access the password reset page.single_sign_on: Allow users to directly access the single sign-on (SSO) page.
Refer to documentation for more details.
New connectors
- Added Kook connector (credit @Misaka-L).
- Added Patreon connector (credit @devtekve).
- Added GitLab connector (credit @devtekve).
Improvements
- Supported
login_hintas additional sign-in parameter. - Implemented well-known swagger endpoints.
- Split
translatecommand from@logto/clito make the CLI small and simple. - Added a dedicated
@logto/translatepackage to translate i18n phrases in Console and Experience. - Supported entering name while creating a user in Console.
- Added new query parameter
parse_errorand explicitly set it tofalseto return raw OIDC error message only. - Added
denyAccess()api to custom JWT context in order to conditionally block user token request. - Supported nested attribute profile mapping in OAuth connector (credit @devtekve).
- Added
hasPasswordproperty to/usersManagement API response. - Added user password information in user details. Admin can easily check if a user has set password or not, and can then perform set/reset action accordingly.
- Added new management API to check password against current password policy settings.
Bug fixes
- Prevented potential error caused by cached identifiers across Experience pages.
- Fixed the issue that blocked users from creating Custom JWT.
- Fixed wecom connector platform. Use
Universalinstead ofnull. - Set
langattribute correctly to<html>in Console, preventing unexpected browser translator prompt. - Allowed linking new social identity to an existing user account when registration is disabled.
- Prevented user registration and profile fulfillment with SSO-only email domains.

