Design your password policy
Gain insights into crafting product password policies that are compliant, secure, and user-friendly, with Logto ensuring the security of your authentication process.
Does your password truly protect you?
In your product, it's likely that you'll need to rely on the classic authentication method – passwords. While passwords won't be replaced entirely, they are more vulnerable to attacks compared to alternative authentication methods. Are your password policies genuinely secure and compliant? Even if you're familiar with various password policy techniques, is layering them really effective?
We address the complexity of password policy design and configuration by conducting in-depth research on NIST specifications, examining leading product password policies, and ensuring a balanced user experience. Emphasizing the importance of password compliance, we aim to relieve you of the challenges associated with password strategy and provide a comprehensive process for ensuring account security through the seamless integration of passwords with other Multi-Factor Authentication (MFA) verification factors.
What kind of passwords do users need?
Product designers often grapple with the question of whether their products are secure enough, leading to the implementation of strict and complex password policies. For instance, requiring a combination of uppercase and lowercase letters, numbers, and even special characters, or mandating regular password changes for employees.
When faced with such password requirements, users are quick to voice their complaints: "Why does it have to be so complicated? Remembering my passwords feels like a full-time job!” This leaves product managers scratching their heads, wondering if a more complex password policy is necessarily better. Let's break down the components of a comprehensive password policy to find out.
In the next section, we'll delve deeper into the nuances of password policies, striking a balance between security and user convenience. We'll explore how to define the right password requirements and provide data-backed insights to support our approach.
A checklist of all password factors
First, after analyzing numerous products and NIST specifications, we've compiled a comprehensive list of password factors and design recommendations.
We've roughly categorized them into three groups:
- Password Setting Requirements: Minimum requirements for user-set passwords.
- Password Security Monitoring: Prompt action and feedback when password risks are detected.
- Password User Experience: Enhancing user input experience during password creation and validation.
| Catalog | Factors | Analysis |
|---|---|---|
| Setting password requirements | Length | Increasing password length is more effective in deterring password cracking than complexity. NIST suggests at least 8 characters in length, but longer passwords should be allowed. |
| Character types | Passwords can support various character types, including Uppercase letters, Lowercase letters, Numbers, Symbols, and Unicode (Space characters should also be allowed). | |
| Password policies SHALL NOT prompt users to recall specific types of information, as this has been shown to increase complexity without effectively enhancing security. | ||
| Low-security phrases | It is advisable to prompt users to change their passwords when they use easily guessable or crackable patterns such as repetitive or sequential characters, common words, user information, or product context information. | |
| Breached password | New user passwords should be checked against a list of leaked passwords to ensure they are not compromised. | |
| Password security monitoring | Password verification rate-limiting | Limit the number of consecutive incorrect password attempts. When this limit is reached, implement security measures such as requiring Multi-Factor Authentication (MFA), sending push notifications, imposing cooldown times, or even temporarily suspending the account. |
| Force to change password | Passwords SHOULD NOT be required to be changed arbitrarily. However, verifiers SHALL force a password change if there is evidence of a compromised authenticator. | |
| Password history | Maintain a record of past passwords that cannot be reused. Excessive restrictions on password reuse are not recommended, as users may bypass this rule through minor modifications. | |
| Clear session after changing password | Allow users to choose whether to sign out of other devices after changing their password. | |
| Password entry experience | Password strength meters | Offer guidance to users to help them select strong memorized secrets. |
| Password prompt | Avoid displaying password hints, as they increase the likelihood of unauthorized access. | |
| Copy and paste the password | Permit the use of the "paste" functionality, which facilitates the use of password managers. | |
| View password | Provide an option to display the password as entered, rather than displaying a series of dots or asterisks, until it is submitted. |
A tool to configure your password experience
Perhaps you don't have the patience to go through every item on the checklist. If we were to design a powerful password tool that encompasses all these configuration options, it might become a headache for developers, even more complex than the complex password policies themselves. Therefore, let's further simplify the password factors into three steps.
Step 1: Discard unnecessary rules
As mentioned in the table, some outdated password rules may seem to enhance security but offer little in return, often causing frustration and confusion among users.
- Avoid limiting the combination of characters users must use; restricting the number of character types is sufficient. For example, Facebook, Discord, and Stripe do not require a specific combination of character types, and Google's password policy merely asks for "At least two types of letters, numbers, symbols."
- Do not mandate regular password changes periodically, as this places an unnecessary burden on users' memory. Instead, require a password change only when there's a risk of credential compromise.
- Only choosing one of the password limits, between clear minimum password requirements and password-strength meters to prevent user misunderstandings.
- Avoid displaying overly complex rules upfront, preventing users from focusing on reading about mistakes that don't necessarily happen.
- Refrain from using password hints to avoid giving potential attackers an advantage.
Step 2: Provide customization for different products
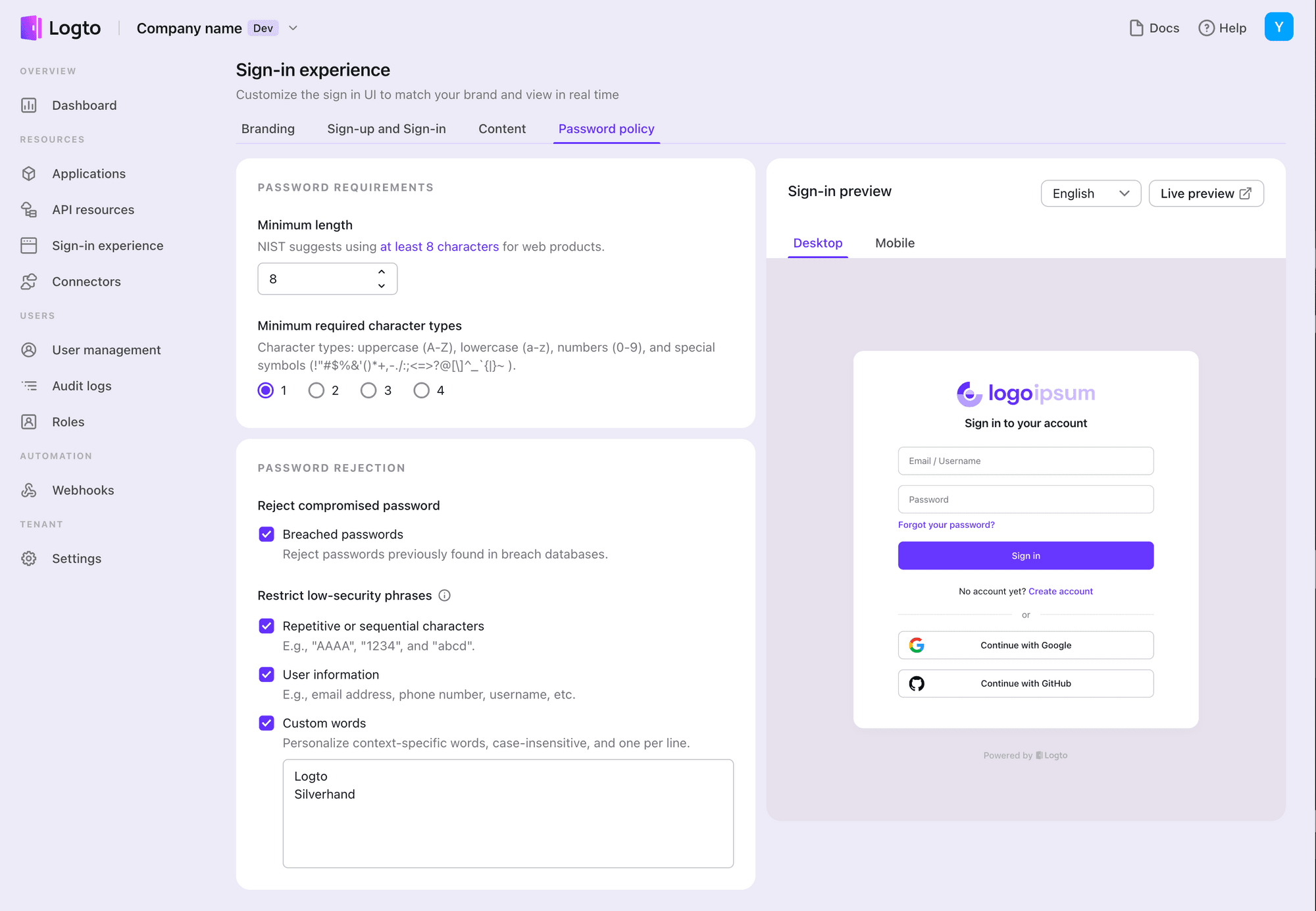
We offer flexible configuration options for minimum password policies, with recommended values to reduce the learning curve for developers and provide out-of-box Sign-in Experience. These options include:
- Minimum length: Default value of 8 characters, minimum 1.
- Minimum required character types: No restriction recommended, i.e., set it to 1 out of 4.
- Password restriction vocabulary: Suggested to enable all restrictions. Users cannot avoid triggering the same vocabulary, but adding three or more non-consecutive characters is allowed to increase password complexity. This addition increases the disorderliness of passwords.
- Prohibit compromised password: Use a reliable breached password database for support, preventing users from using identical passwords to avoid direct directory attacks.
Step 3: Ensure security with fixed values
For parameters that cannot be customized, we have implemented backup logic to ensure password security. If you have specific customization requirements, please feel free to inform us.
- Password Verification Rate-Limiting: We have restricted the number of consecutive incorrect password verifications and the cooldown time for suspending sign-in. This safeguards against continuous password attacks. Additionally, we provide a webhook for consecutive failed password verifications and you can use it to send email notifications or suspend accounts at high risk of compromise.
- By default, we clear sessions on other devices after resetting the password and refreshing the token. This extra layer of security helps prevent unauthorized access to your account, ensuring that your data remains confidential and protected.
Conclusion
With these three straightforward steps, you can streamline the process of configuring your password experience, striking the right balance between security and user convenience. Logto makes it easy to set up a secure and user-friendly authentication system for your product. Stay tuned for our upcoming MFA feature, and take control of your product's security like never before.

