Exploring MFA: Looking at authentication from a product perspective
Deconstructing Multi-Factor Authentication (MFA) through an analysis of its core components, user processes, and essential guiding principles.
In the digital landscape, if every app is used the same way to sign in, could we save time and resources by simplifying how we prove who we are? Sounds possible, right? Like when you use "Continue with Google" for everything, or just one email and password combo for all your stuff.
But the real story is more interesting. Each app has its unique way to make sure it's really you signing in. We put effort into this verification process to keep things secure, balance user experiences, and respect privacy preferences per user.
Since there's no magic formula for everyone, let's break down how verification works and create designs that match the service.
The basics: two parts of the authentication
Authentication, the fancy word for verifying who you are, is made up of two things: an Identifier and a Verification Factor.
Think of the Identifier as saying "Hi, I'm Sarah." You might think, "Oh, that's Sarah, cool." But the security folks ask, "Is this truly Sarah? Does Sarah possess the necessary credentials to gain access?" That's where the Verification Factor comes in. Let's put this into tech terms.
Identifiers: your digital ID
Identifiers determine what a user can access. Since resources are always scarce, your identity is your unique pass. Step one: input your identifier on the sign-in page. But we're not going with Nickname or Full name – that's a search overload waiting to happen. Identifiers that can be used are:
-
User ID: Technically unchanging and unique. It's like for admin management, but users won't remember these for each product.
-
Username: A user-friendly iteration of the User ID. It's unique and can't repeat in an account system. Social platforms personalize profiles, but to keep recognition stable, it's got to be the Username. Limited changes, maybe even paid ones.
-
ID Number: Like ID cards, student IDs, or bank card numbers, are solid and unique identifiers. Although not easily remembered, they can be retrieved as a reliable backup mechanism if you forget your main ID.
-
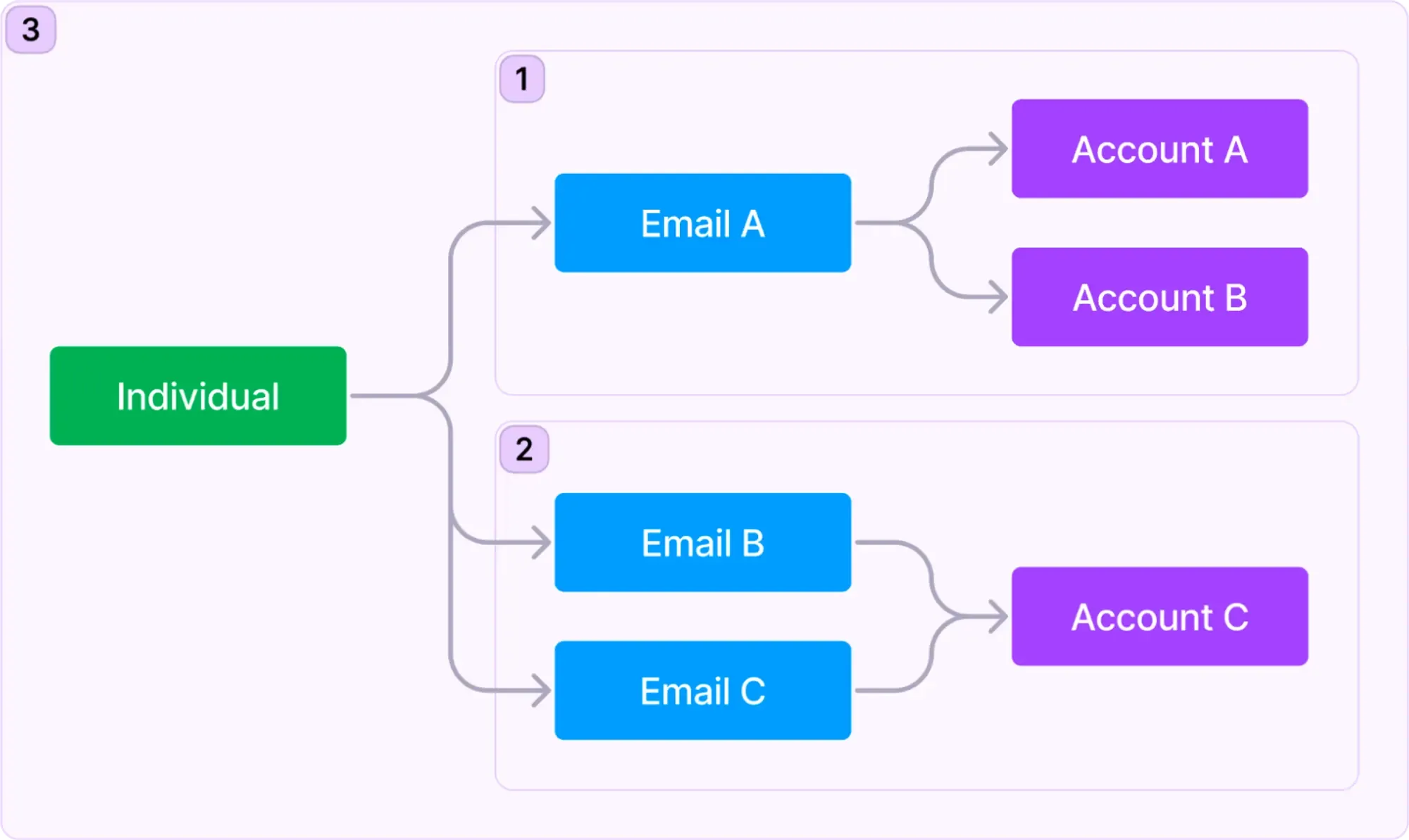
Email or Phone Number: Unlike the username can often slip from memory, contact info is more memorable. Employing an Email or Phone Number as an identifier prevents users who have been inactive or recalled over the long term from forgetting their identity, reducing the risk of potential churn. While this convenience is user-friendly, managing the interaction among "individuals, emails, and accounts" can complicate your product structure. Consider Instagram: (1) It enables multiple accounts using a single Email; (2) Multiple email addresses can be added to an Instagram profile for login or recovery; (3) Instagram permits simultaneous logins across accounts, regardless of email matching. While accounts usually have segregated resources, Instagram allows the merging of account information, fostering cohesive validation, targeted ads, and personalized recommendations.
Verification factors
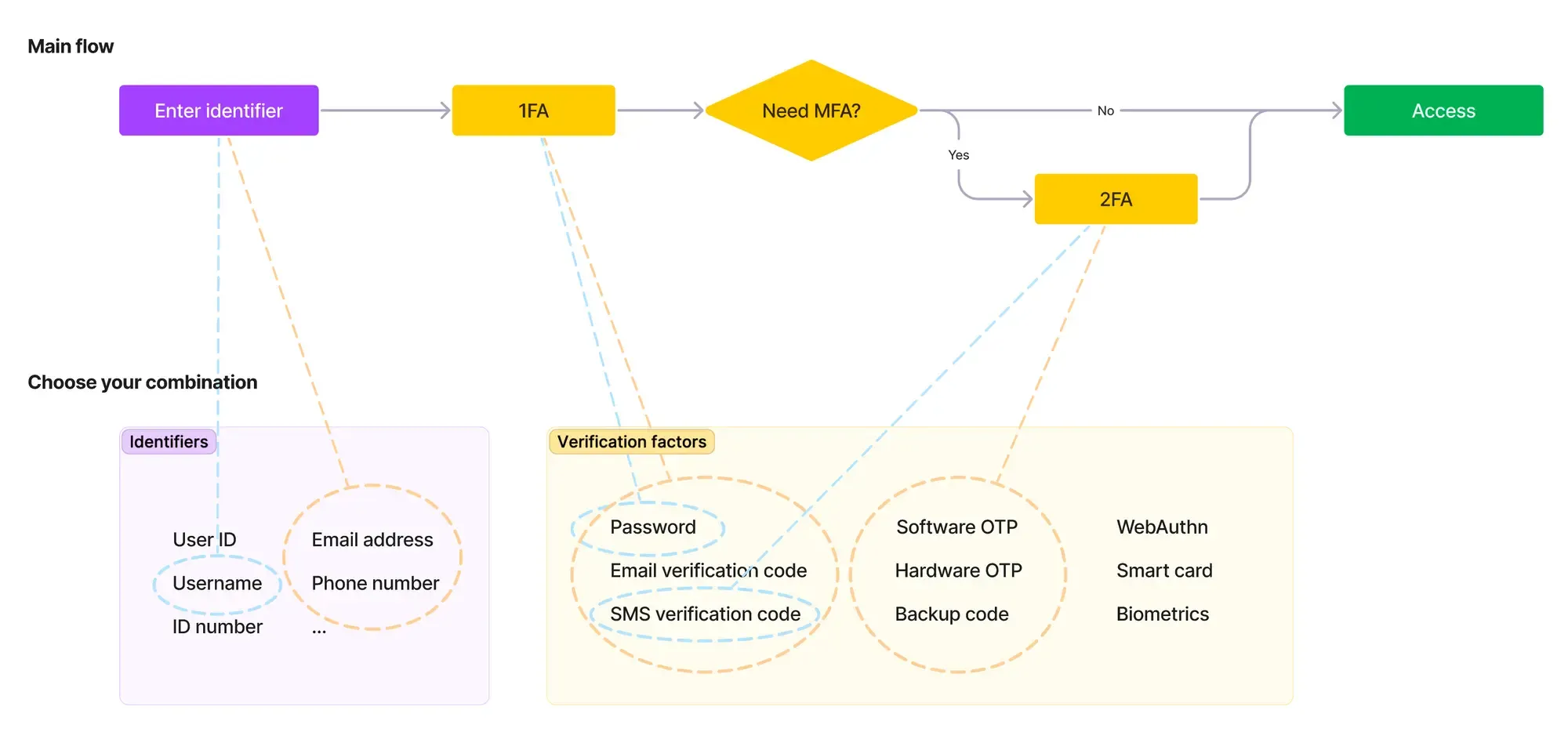
Authentication factors are the moves that prove you're really you. There are lots of factors divided by attributes to choose from:
| What it means | Verification factors | |
|---|---|---|
| Knowledge | Something you know | Password, Email verification code, Backup code |
| Possession | Something you have | SMS verification code, Authenticator app OTP, Hardware OTP (Security key), Smart card |
| Inherence | Something you are | Biometrics like fingerprints, face ID |
Theoretically, you can mix these Verification factors with any Identifier to prove it's you. Common: Email address(ID) and Email verification code(Factor). But you can mix it up: Email address (ID) and SMS verification code(Factor).
Because evil's lurking, a single factor isn't enough. That's where Multi-factor Authentication (MFA) comes in. When you sign in, the first step authentication(1FA) is a must, but there can be more steps, a second (2FA), and even a third. Additionally, when you request access to critical resources in-app, you’re required to reverify your identity. These additional layers offer heightened security against malicious actors. This whole range is MFA.
Design your authentication flow
Back to the start – why each app has different Identifiers and Authentication factors combo? It’s about user experience.
Being too strict with verification can make users annoyed, thinking, "Why is this so hard?" Being too relaxed can lead to hacked accounts and chaos. So, whose trouble is it?
Three choreography principles:
Ensure your real users can get in
People sometimes forget IDs or lose verification steps. To alleviate potential support burdens, we need ways to help:
- Offer various factors to verify – usually at least two for MFA. Because biometrics are cool, but they don't work when not recognized; sometime users may lose devices.
- Have options to recover verification – like "Forgot password" or finding your ID again. However, before recovery, preliminary identity verification is also required, which usually differs from the sign-in process.
- Provide contact information for recovery through customer service or admins as a backup.
Verification without loopholes
Verifying isn't perfect, and two-step authentication isn't always more secure. Remember:
- In the MFA flow, the second step of authentication should possess different attributes (Knowledge/Possession/Inherence) from the first. For example, using "Password (Knowledge)" as 1FA and "Authenticator app OTP (Possession)" as 2FA can stop various attack vectors.
- Recovery methods can't skip MFA. For instance, if you can “forgot password” through SMS, you can't also use SMS as the second authentication factor. Another option is adding 2FA to the "forgot password" process, although this might seem intricate.
- Consider code-down time or rate-limiting. After multiple incorrect verification attempts, restrict the rate of subsequent verification. And disallow extended intervals between steps in multi-step verification.
Balance user experience
Not every action needs 1FA or 2FA. It's about the situation, not always following the same steps.
- Give custom capacity to different roles: Ensuring the security of resources is primarily the product's responsibility, but it is also an individual's duty. Strategies for mandating MFA can be tailored based on the nature of the service: universal user MFA in-app, organization-driven MFA, and user-decision-driven MFA.
- Take advantage of adaptive MFA: For scenarios involving potential risks or high-stakes operations, mandating verification is pragmatic. In contrast, secure environments or low-risk operations may warrant streamlined access through retained sessions, minimized verification steps, or even guest access. Notably, this hinges on considering the user's context.
- Unsafe environments: Such as new devices, uncharacteristic travel locations, or untrusted IPs.
- Sensitive Actions: Such as involving encrypted data access, big financial transactions, or changing verification methods.
For details, check NIST's Authentication Assurance Levels (AAL) guidelines.
Closing notes
As we wrap up our exploration of authentication and multi-factor verification (MFA), we hope you've gained insights into the vital role they play in our digital lives. MFA, blending identifiers and verification factors, creates a robust shield that maintains secure access while delivering user-friendly interactions.
The exciting news is that Logto's MFA is on the horizon. For individuals and businesses, Logto ensures safe online interactions.

