How does one-time-password (OTP) work?
In this article, we will introduced two different one-time password methods: email/phone + verification code and dynamic code.
As the internet has evolved, we've been using a wide range of online services to meet almost all of our needs. The first step in using these services is often registration and login. When it comes to registration and sign-in, user ID and password authentication is still widely used, even though over three decades have passed since the days of using standalone desktop computers that couldn't connect to the internet.
In the past, we may have only needed to remember the password for our email account, but now we often use dozens or even hundreds of online services, and we can't use the same password for all of them (if the password for one account is compromised, all the accounts using the same password will be at risk). As a result, passwordless sign-in is becoming increasingly popular and is gradually becoming the mainstream approach.
There are many different methods for passwordless authentication, including but not limited to social sign-in, email/phone + verification code, and the use of authenticator apps with dynamic passwords. The latter two methods can be classified as one-time passwords (OTPs).
What is one-time-password (OTP)?
An OTP is an automatically generated sequence of characters that is only valid for a single login session or a short period of time. Because an OTP can only be used once, it can prevent the risk of credential leakage, such as a lost or stolen password.
In theory, an OTP can be a random string of characters of a certain length, including uppercase and lowercase letters, and even special symbols. But for the sake of user experience, most services use pure numbers when using OTPs.
Email / phone + verification code
Many websites require you to verify your identity by sending a verification code (or passcode) to the email or phone number you've registered.
Imagine that Jack and Joe are playing a guessing game, where Jack thinks of a number between 0 and 999, and gives Joe three chances to guess the number within one minute. Aside from knowing the range of the number, Joe has no other information.
We all know that it's almost impossible for Joe to guess the number correctly within one minute using only three attempts.
Email / phone + verification code works on the same principle: the verification code is generally valid for a very short period, usually not more than 10 minutes (similar to Jack giving Joe "one minute" to guess the number). Additionally, the API or method for verifying the verification code typically has a rate limit to prevent brute-force attacks on the passcode (like Jack only giving Joe "three chances").
For potential attackers, it's almost impossible to crack this method. However, the system tells the user the verification code through a trusted channel (email or phone), allowing the user to verify it directly.
Dynamic code
Dynamic code, also known as time-based OTP (TOTP), is "dynamic" in the sense that it changes over time. Generally, if a web app uses TOTP, it will follow RFC6238 - TOTP: Time-Based One-Time Password Algorithm.
Hash-based one-time password
Before introducing TOTP, we need to briefly explain RFC4226 - HOTP: An HMAC-Based One-Time Password Algorithm (HMAC is a hashing algorithm). The HOTP algorithm works as follows:
-
Secret: HOTP requires a shared secret key K, which is the same between the server and the client.
-
Counter: The core of HOTP is a counter C, which is incremented each time a new password is generated.
-
HMAC Calculation:
-
Use HMAC-SHA-1 (or other hash functions) to calculate the authentication code:
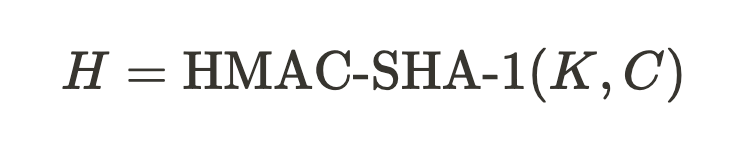
-
Here, H is a 160-bit hash value.
-
-
Truncation: Extract a part of the hash value H to generate the OTP. Assuming we want a 6-digit OTP, the process is as follows:
- Extract the last byte of H as the truncation offset O.
- Extract the 4 bytes starting from O, convert them to an integer T.
- Take the last d digits of T, i.e., OTP = T mod 10^d.
In summary, the HOTP formula is:

where d is the desired OTP length (usually 6-8 digits).
Time-based one-time password
TOTP is an extension of HOTP, where the counter is replaced with a time step. It uses the current time to generate a dynamic verification code, so the OTP will automatically expire over time. The working principle is as follows:
-
Time step: TOTP uses the current time T instead of the HOTP counter C. The time step is a set fixed time interval (usually 30 seconds).
- For example, assuming the time step is 30 seconds, and the current Unix timestamp is T. The TOTP counter is calculated as: T' = T / time_step
- Where T′ is the time step counter, in units of 30 seconds.
-
Generating OTP: Substitute T′ into the HOTP algorithm to generate the OTP:

-
Dynamic update: Since TOTP is based on the time step, the OTP changes over time, so the server can verify its validity as long as the OTP is within the valid time window.
In summary, the TOTP formula is:
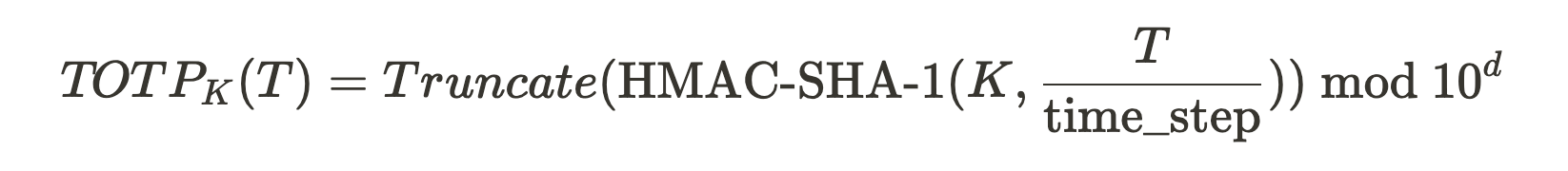
Based on our experience using authenticator apps, we can sync the secret value between the device and the server by scanning a QR code or directly copying and pasting, and then we need to enter the current dynamic code once to ensure that the secret value is the same.
In the early days of using mobile devices, we might find that the time on different devices was not the same, and we would have to manually adjust the time on the devices periodically. In recent years, almost all devices use the network time service (NTP) to regularly synchronize and update the device time. Even if the device's clock is not entirely accurate, the frequent updates can ensure that the time is reasonably consistent across different devices. Based on this assumption, the dynamic code can still be used even if the device is offline, whereas it would be difficult to receive a verification code in an offline state.
Closing notes
In this article, we've introduced two different one-time password methods: email/phone + verification code and dynamic code.
Email/phone + verification code relies on communication infrastructure and third-party email or short-message service (SMS) to implement; dynamic code does not depend on external services and communication facilities, and can be used offline.
Logto, as a popular, powerful, and highly extensible IAM (Identity and Access Management) service, supports both OTP methods, allowing users to choose the solution that best fits their needs from a business perspective.

