Logto in action: Integrate Apache Answer to launch a community for your users
Demonstrates how to leverage Logto's 3rd-party app feature to integrate Apache Answer, creating a unified community platform where users can seamlessly access support using their existing accounts.
Building a great software product is a significant achievement, but it's really just the beginning of the journey.
The long-term success and evolution of any application depend heavily on understanding and engaging with its users, which involves gathering feedback, identifying pain points, answering questions, and resolving issues —— a key cycle that drives iteration and improvement.
In this article, I will:
- Explain how Logto's Third-Party Application (OIDC) feature works.
- Show you how to use Logto to integrate Apache Answer to build a community for your users, allowing them to ask questions, share ideas, and get help from your team and other users.
The highlight of using Logto is that users sign in to the community with the same account as in your own system. This allows you to easily know the current state of users asking questions, eliminating the need for multiple back-and-forth exchanges to inquire about their situation in your software.
What is Apache Answer

Apache Answer is an open-source Q&A platform that connects users and teams. It creates a space for sharing knowledge and solving problems together. The platform features real-time Markdown preview, advanced search, and a voting system for content.
The platform supports OAuth 2.0 login out of the box. This makes it naturally compatible with existing identity providers like Logto. Users can sign in with their existing accounts without creating new credentials specifically for the community platform.
Understanding Logto's third-party application feature
When we want users to log into third-party applications using their Logto accounts, Logto acts as your application's Identity Provider (IdP).
Think of it as a central authority responsible for verifying who your users are. When a user logs into your main application, it likely redirects them to Logto to handle the authentication process (username/password, social login, etc.). Once Logto successfully verifies the user, it tells your application, "Yes, this user is legitimate," and provides some basic information about them.
This concept extends beyond just your primary application. Logto includes a powerful feature —— Third-party Application. This feature allows Logto to perform its IdP role not just for your own application, but for other external applications that you want your users to access.
It achieves this using OpenID Connect (OIDC), which is a standard identity layer built on top of the OAuth 2.0 protocol. In simple terms, OIDC allows an application (like Apache Answer, known as the Relying Party or Client) to request and receive information about a user's identity from an IdP (Logto).
When you configure an OIDC application within Logto for Apache Answer, you're essentially telling Logto: "Be prepared to authenticate users on behalf of Apache Answer if it asks, and if the user approves, securely send Answer some basic user identity details." This capability is the key to unlocking seamless single sign-on (SSO) between your Logto-authenticated application and third-party tools like Apache Answer.
Setting the scene: YourApp + Logto + Apache Answer
Before diving into the configuration, let's clarify the components involved in our scenario:
- YourApp: This is your primary web or mobile application where users already register and log in. Crucially, YourApp is integrated with Logto for authentication.
- Logto: Your central IAM platform, acting as the IdP. Your users have accounts managed by Logto.
- Apache Answer: The open-source Q&A platform you want to deploy as a community hub for YourApp's users. Our goal is to configure Answer to use Logto for login, instead of its own local username/password system.
Hands-On steps: Configuring Logto and Apache Answer
Now, let's get practical. The process involves configuration in both Logto and Apache Answer.
Install Apache Answer
Follow the official installation guide to install Apache Answer. And finally you can access it at http://localhost:9080 by default.
Create an OIDC Application in Logto
- Sign in to your Logto Console.
- Navigate to the applications page.
- Click on the "Create application" button in the upper right corner of the page (if you don't see this button, click "view all" at the bottom of the framework list).
- Select "Third party application" category, then choose "OIDC".
- Enter the application name (e.g., "Apache Answer Community") and description (optional).
- Click "Create" to complete the creation. After creating the application, you'll be redirected to the application details page.
- In the details page, add
http://localhost:9080/answer/api/v1/connector/redirect/basicto the Redirect URI field. - Click "Save" to save the application.
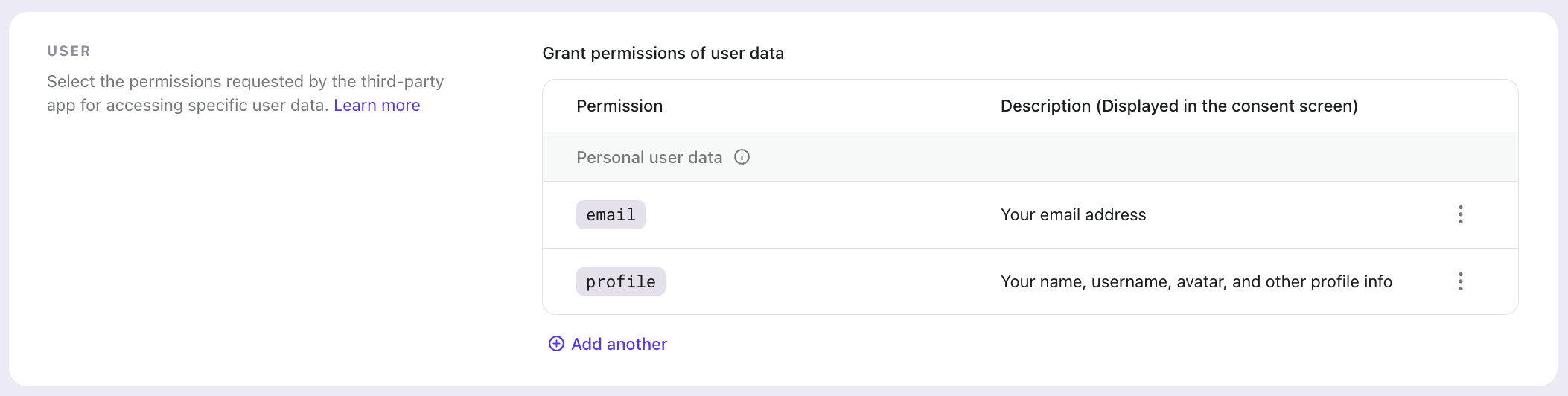
Configure permissions for Apache Answer
- In the application details page, navigate to the Permissions tab.
- Under Grant permissions of user data, you'll see a message saying "You don't have any grant permissions of user data set up yet."
- Click the Add button to configure what user information Apache Answer can access.
- Select the necessary scopes (
profileandemail) to allow Apache Answer to receive basic user information upon login. - Save your permission settings.
Configure OAuth Login in Apache Answer
- Log in to your Apache Answer using the admin account.
- Visit the Admin dashboard at
http://localhost:9080/admin. - Navigate to Plugins -> Installed Plugins and active OAuth2 Basic plugin.
- Navigate to the OAuth2 Basic plugin page.
- Fill in the following information according to the Logto 3rd-party application you just created:
- Name: Name of your connector which will be shown in the login page
- Client ID: The "App ID" from the application details page.
- Client Secret: The "App Secret" from the "Endpoints & Credentials" section of the details page.
- Authorize URL: The "Authorization endpoint" from the "Endpoints & Credentials" section of the details page.
- Token URL: The "Token endpoint" from the "Endpoints & Credentials" section of the details page.
- User JSON URL: The "Userinfo endpoint" from the "Endpoints & Credentials" section of the details page.
- User ID JSON Path:
sub. - User Display Name JSON Path:
name. - User Username JSON Path:
username. - User Email JSON Path:
email. - User Avatar JSON Path:
picture. - User Email Verified JSON Path:
email_verified. - Scopes:
openid,profile,email.
- Save the Plugin configuration in Apache Answer.
Note: Be sure to include the openid scope, which is required by the OIDC standard to fetch user information from the User JSON URL. Since Logto's third-party application is implemented based on OIDC, while Apache Answer's plugin uses OAuth 2.0, this scope is essential to ensure proper authentication flow between the two systems.
Check point: Test the integration
With both Logto and Apache Answer configured, let's see the seamless user experience:
- Visit your Apache Answer, you will see there is a "Connect with Logto" button on the login page.
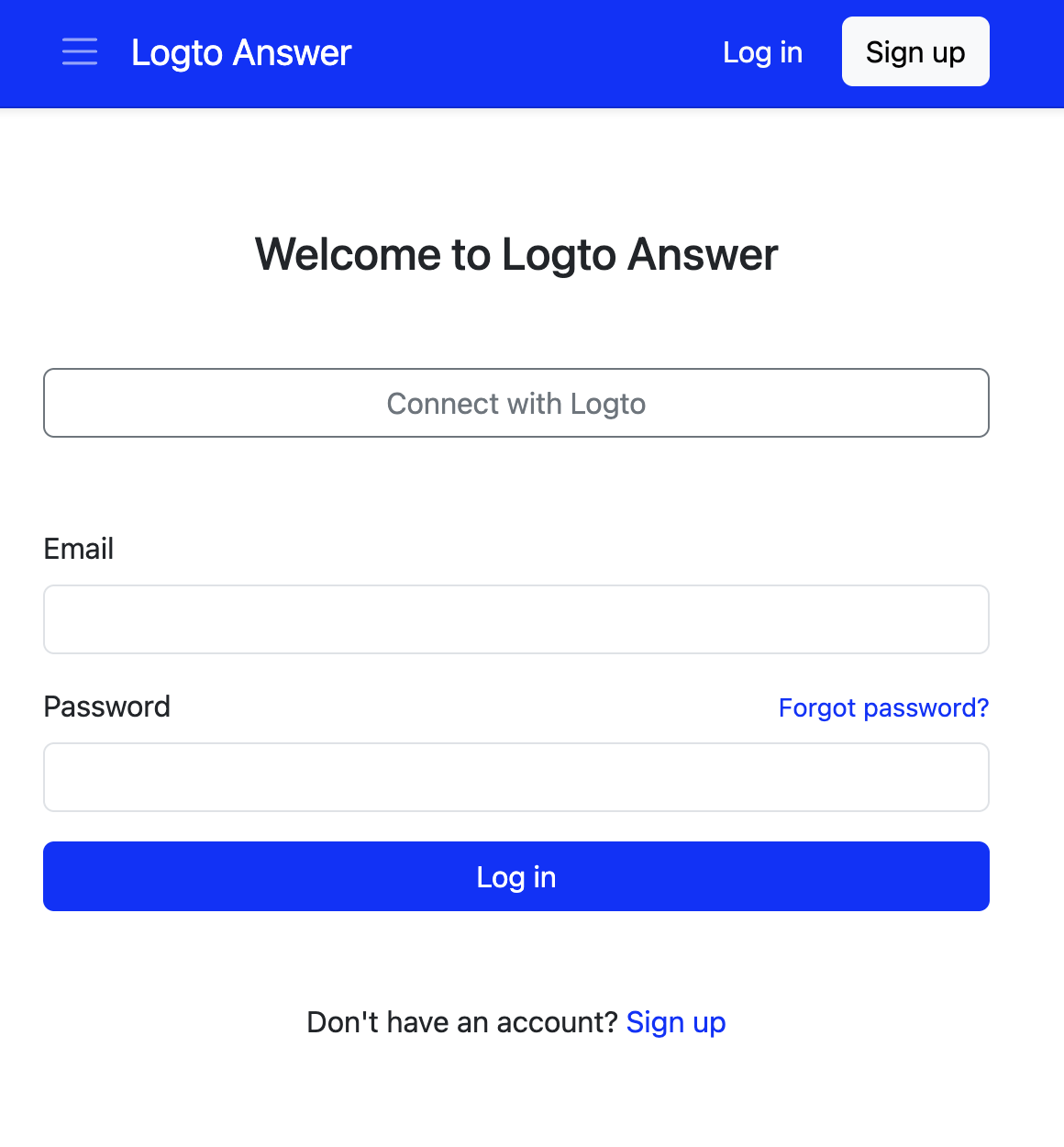
-
Click the button, you will be redirected to Logto's login page.
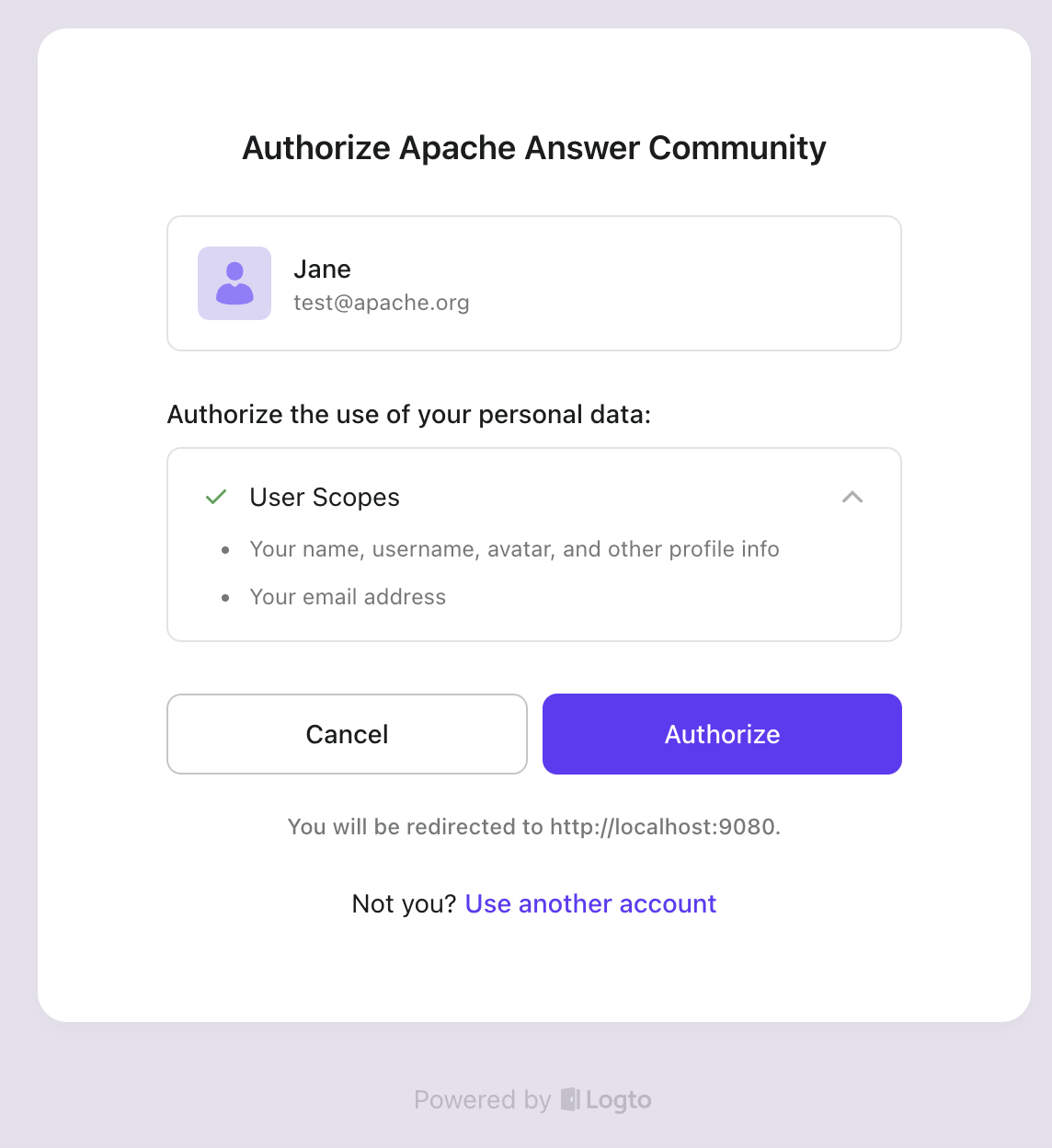
-
After clicking the "Connect with Logto" button, you'll be redirected to Logto where you can login with your existing account. You'll then see a consent page asking permission to share your information with Apache Answer.
- After you approve the permission, you will be redirected back to Apache Answer, and you will see you are logged in!
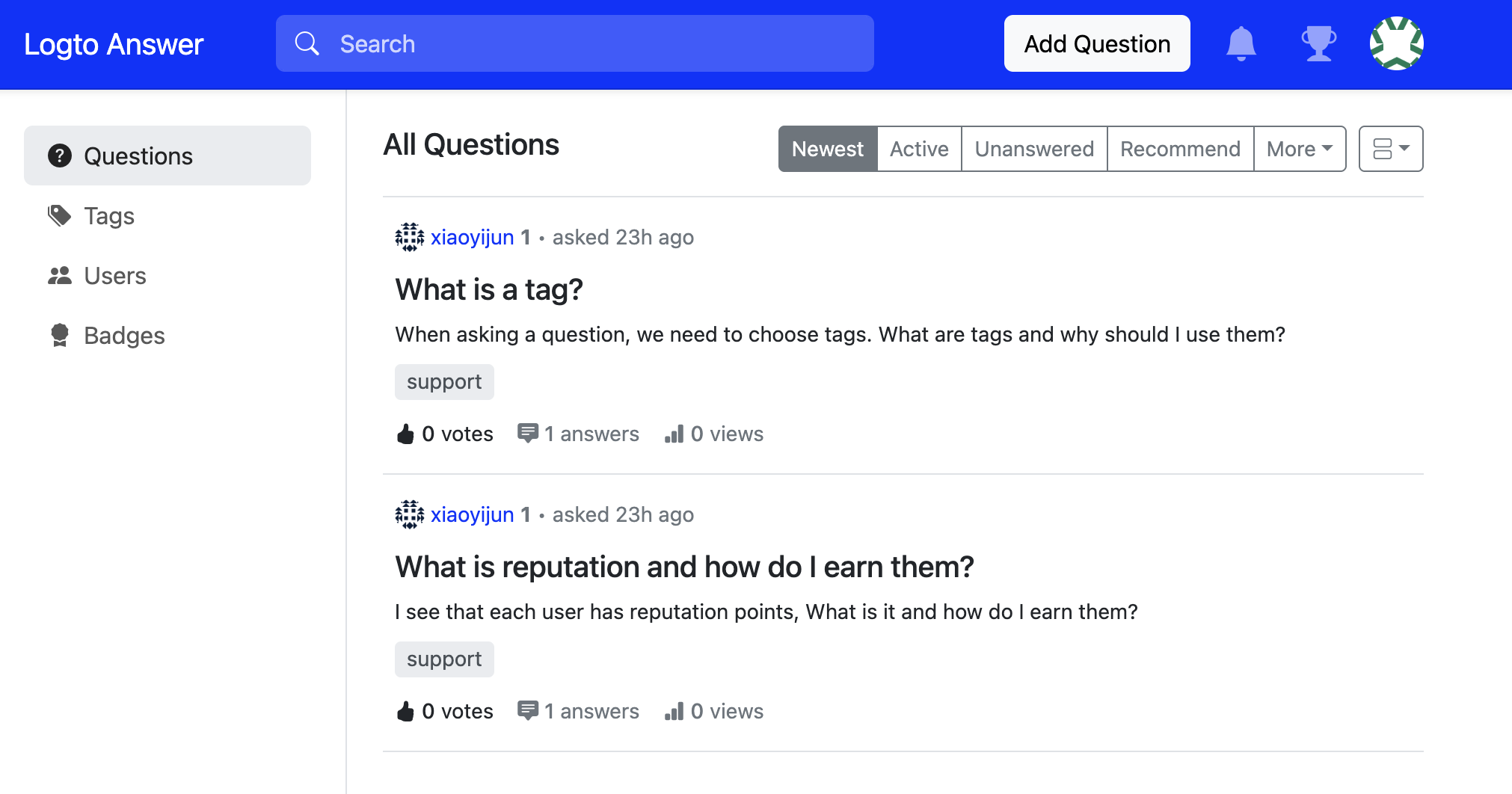
Note: Apache Answer checks if the logged-in user has a verified email. When your user does not have email information, Apache Answer will ask them to provide an email for verification.
Benefits of integration summarized
Why go through these steps? The advantages are significant:
- User Experience: This is the most obvious win. Users don't need to create or remember another set of credentials. They use the login they already trust, providing a smooth, frictionless entry into the community. This drastically lowers the barrier to participation.
- Development Efficiency: You completely bypass the need to build and maintain separate user authentication, registration, password reset flows, etc., within Apache Answer. You leverage your existing Logto user base instantly, allowing you to launch the community much faster.
- Security: Authentication is delegated to Logto, your specialized IAM provider, which likely handles security aspects like multi-factor authentication (MFA), password policies, and brute-force protection more robustly than a custom implementation within Answer might. You rely on the mature and well-vetted OIDC standard.
- Product Value & Support Efficiency: You instantly add a valuable community feature without fragmenting your user identity. As highlighted earlier, knowing that the community user is the same as the product user empowers your support team to provide much more contextual and efficient help, boosting user satisfaction and engagement.
Conclusion
Integrating third-party tools is essential for building a rich application ecosystem, but managing user identities across these tools can be a major headache. As we've demonstrated with Apache Answer, Logto's third-party application (OIDC) feature provides a powerful and standardized way to bridge this gap.
By configuring Logto as the central Identity Provider for Apache Answer, you can effectively "one-click" enable a dedicated community space for your existing users, offering them a seamless login experience and providing your team with the benefits of a unified user identity.
What's even more exciting is that this pattern isn't limited to Q&A platforms; it can be applied to analytics dashboards, project management tools, internal utilities, and countless other applications, allowing you to build a cohesive and user-friendly software ecosystem.
Stay tuned for future articles where we might explore integrating other useful tools using Logto!

