Public key, private key and asymmetric cryptography
In this article, we have introduced the concepts of public keys, private keys, and the principles of asymmetric encryption. We have compared their pros and cons against symmetric encryption, as well as the differences in their usage scenarios.
You may have heard about private keys and public keys in many contexts, but do you really know what they are?
Asymmetric cryptography vs symmetric cryptography
Private keys and public keys are concepts in asymmetric cryptography (also known as public-key cryptography, PKC).
Asymmetric cryptography refers to a method of encrypting or signing data using two different keys (private key + public key), which corresponds to the need for decryption or signature verification. The public key is visible to anyone, while private key is only available to the key owner. You can easily tell from the keys’ name.
Similarly, you can probably guess that symmetric cryptography refers to the method of encrypting and decrypting data using the same key.
We hence use simple annotation to show the encryption/decryption process of both symmetric and asymmetric cryptography.

It is important to note that the encryption/decryption functions in symmetric and asymmetric encryption algorithms are different and often use different algorithms. Common symmetric encryption algorithms include DES, AES, RC2, RC4, and others, while common asymmetric encryption algorithms include RSA and EC.
Logto uses EC algorithm for data transmission encryption and decryption since it is more efficient and secure than RSA, you can read this post for more details. Logto will going to support RSA in the next release as well for better compatibility with some legacy systems.
Why using asymmetric cryptography?
Asymmetric cryptography addresses the issue of key distribution in symmetric cryptography.
Since symmetric encryption use the same key, distributing the key over an insecure network connection may risk exposing the key to malicious third parties. A malicious third party could use the stolen key to access any information encrypted with that key, posing a significant security risk.
Two common use cases of asymmetric cryptography
Sending encrypted data
The sender can use the recipient's public key to encrypt information, and the recipient uses their private key to decrypt the information.
Since public keys are theoretically available to many people, in an ideal scenario, the recipient can receive encrypted information from many senders. Moreover, multiple senders cannot know what kind of information other senders have sent to the recipient, as only the recipient (the holder of the private key) can decrypt and recover the information.
Public keys and private keys are often generated simultaneously. What we mentioned above is generation of private keys and public keys on one party, and then distributing the public key to its users. If you need to ensure secure communication between both parties, then both parties need to generate their own private keys and public keys, and then exchange their respective public keys. This way, both parties have each other's public keys, and they can use their own private keys and the other party's public key for encryption and decryption.
Using a signature to ensure data fidelity
In asymmetric cryptography, the party holding the private key can sign the data they send. Subsequently, the recipient with the public key can verify the consistency of the data and the signature upon receiving the data, ensuring that the data has not been tampered with during transmission.
Using the annotation we defined in previous section, the sign and signature verification can be represented as following:
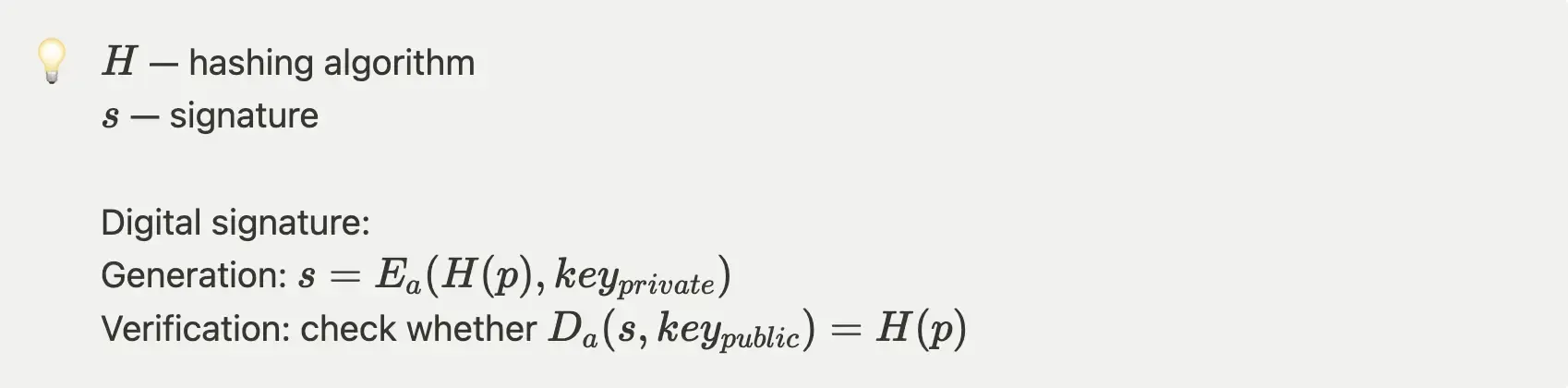
The verification of digital signature proves the party which generate the signature knows the corresponding private key.
You probably find these two use cases mentioned above very familiar. In our daily lives, almost all services with server-client architecture use asymmetric cryptography to ensure data security.
As a rapidly growing user identity framework, Logto also extensively uses PKC to ensure the security of user data. After users complete the login process, Logto issues an access token to users to grant them specific permissions to access the required resources. Logto's published public key is used to verify that the access token is indeed issued by Logto and has not been tampered with by malicious attackers.
Fallbacks of asymmetric cryptography
In general, the key length for symmetric encryption is 128 or 256 bits, while the key length for asymmetric encryption can reach 4,096 bits. This is because the private key and public key are mathematically related and unique key pairs. In theory, knowing the public key allows the calculation of the private key's value, but due to the complexity of the algorithms involved, it often takes a considerable amount of time. To make the task of "cracking" the private key "impossible," using longer key lengths is a straightforward approach.
Takeaways
Asymmetric encryption consumes more computational resources and time compared to symmetric encryption during calculations per discussion in previous section. In applications where communication is frequent, the widespread use of asymmetric encryption may impact performance and user experience.
In business scenarios, symmetric and asymmetric encryption are often used together to balance performance and data security. When building your own service, you can consider the data security requirements at each stage and select the appropriate encryption algorithms accordingly.

