What is AuthZ (Authorization)?
Explore the definition of AuthZ, AuthN vs AuthZ, how the AuthZ works, and authorization best practices.
What is AuthZ?
AuthZ is short for authorization. Authorization is a separate mechanism from authentication. While authentication identifies who you are, authorization determines whether you can access specific resources and what actions you can perform on them.
In real-world examples, resources can include software, systems, documents, orders, and assets. Authorization adds an extra layer of control, specifying who can access these resources and under what conditions.
How does AuthZ work?
Authorization is separate from authentication but often connects with it. For example, standard protocols like OAuth 2.0, OIDC, and SAML incorporate token-based authorization mechanisms.
In a token-based authorization system, an authorization server grants an access token to users. This token, which includes permissions, determines whether the user can access certain resources.
Assigning permissions directly to users can be inefficient, especially when more detailed conditions are required. For instance, access might depend on specific circumstances, like the user’s location, making access control policies necessary for better permission management.
Here’s a step-by-step high-level flow to how authorization works:
- Initiate authentication: The user signs in by selecting an identifier and method, like using an email and password.
- Authorization request: After signing in, the user requests access to a resource, including details like their user ID and roles.
- Access control validation: The system checks the request against predefined authorization policies, such as role-based or attribute-based rules.
- Authorization decision: The system determines whether to grant or deny access based on the policies and permissions.
To understand the OAuth 2.0 authorization request flow in detail, check out the authorization request
What are the authorization types?
Role-based access control and how it works
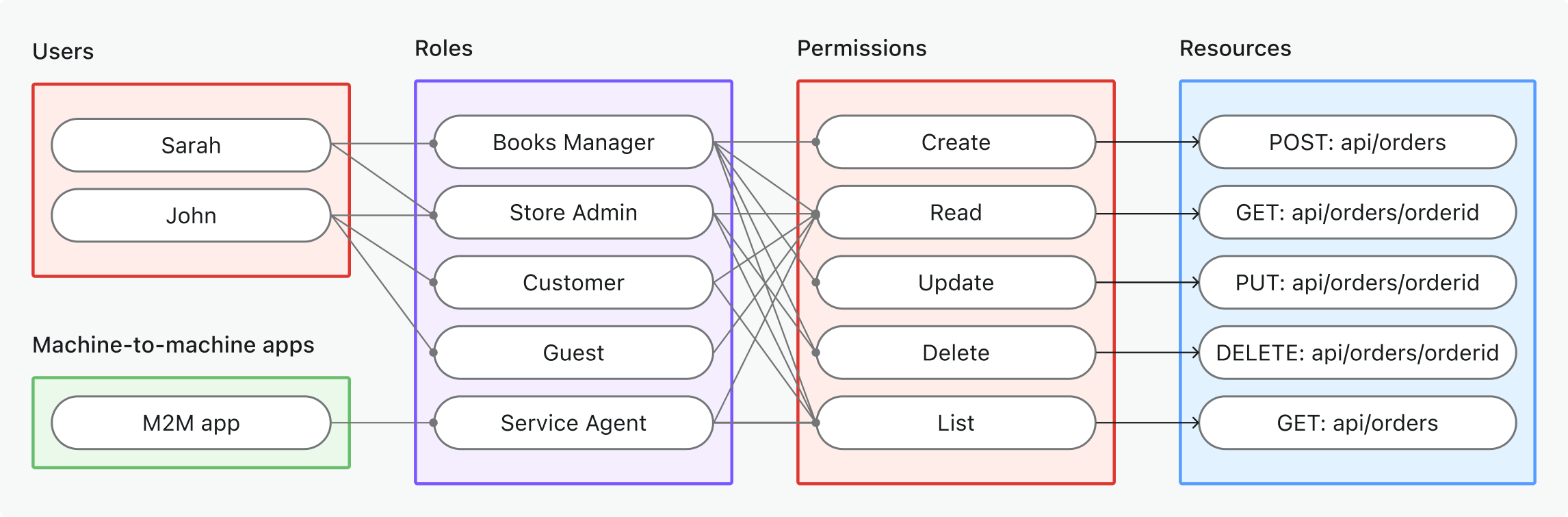
Role-Based Access Control (RBAC) uses roles to manage access. Each user is assigned one or more predefined roles, and every role includes a set of permissions. The key to RBAC is understanding the relationship between subjects (or users), roles, and permissions.
To understand how Role-Based Access Control (RBAC) works, you need to know about:
- Subjects: These can be users or non-human entities, such as
userormachine-to-machine application. - Roles: Represent job functions or responsibilities. e.g.,
adminmember - Permissions: Specify what actions are allowed on specific resources, e.g.,
read: order.
Attribute-based access control and how it works
Attribute-Based Access Control (ABAC) is widely used in authorization and supports more complex scenarios by using specific attributes of an entity, beyond just roles.
For example, A company manages a global document-sharing platform where employees need controlled access to sensitive files based on their job role, location, and the document’s classification level.
The attributes can be designed in the following ways:
- User attributes: Role (e.g., “Manager,” “Engineer”), location (e.g., “US,” “Europe”).
- Resource attributes: Document type (e.g., “Financial Report,” “Design File”), classification level (e.g., “Confidential”).
- Environment attributes: Access time (e.g., “During Work Hours”), device type (e.g., “Company Laptop”).
There are also other access control models such as policy-based access control (PBAC) . Each model has its strengths and weaknesses, and the choice of model depends on your use case and requirements.
AuthZ uses cases and examples
B2C software
B2C software often requires specific roles based on the business needs. For example, a bookstore management app might include roles with different responsibilities, like managing resources and services.
B2B multi-tenant app
B2B apps often use a multi-tenant architecture, where each tenant represents an organization. Within the organization, roles like admin and member are needed. This is where Authorization (AuthZ) plays a key role in managing users at the organization level, often using Role-Based Access Control (RBAC).
Machine-to-machine authorization
Machine-to-machine communication directly happens between services without human interaction. For example, calling API services by. It often involves tokens (e.g., OAuth 2.0 access tokens) to ensure secure, dynamic, and granular access.
What are the best practices for AuthZ?
Here are some best practices for authorization (authZ) to ensure secure and effective access control:
-
Principle of least privilege
This ensures the risk of unauthorized access or damage from compromised accounts is minimized. Users and systems should only access the resources and actions needed for their role.
-
Employ token-based authorization
Token-based access control offers more flexibility and fine-grained control while adhering to open standards. Use secure tokens (e.g., OAuth 2.0, JWTs) to grant time-sensitive and scoped access.
-
Regularly audit and monitor
Regularly reviewing access logs and authorization policies is necessary to spot anomalies or outdated permissions.
-
Apply separation of duties
Start by implementing fine-grained permissions, such as defining specific actions and resources (e.g., read, write, delete). When creating roles, use clear role names and enforce separation of duties to minimize the risk of fraud or mistakes by a single user.
-
Support multi-tenancy (if applicable)
For multi-tenant systems, tenant isolation is important. By combining it with role-based access control, you can achieve separation of data resources, ensuring that the appropriate roles can access resources only within their tenant. This prevents accidental or malicious access to other tenants’ resources.
-
Revoke access dynamically
When designing your AuthZ system, ensure permissions can be updated or revoked immediately if conditions change (e.g., role updates, or employment termination). This can be achieved through dynamic API checks, webhooks, or other methods. The goal is to prevent unauthorized access in real-time.
What are the difference between AuthZ(Authorization) vs Auth(Authentication)?
The difference between authentication and authorization lies in their purpose and process within identity and access management.
AuthN (Authentication) answers the question, “Who are you and which identity you own” It is the process of verifying the identity of a user, service, or device. Authentication ensures that the entity attempting to access a system or resource is genuine. Common methods include passwords, biometrics, and two-factor authentication (2FA). For example, when you log in to an account using your email and password, the system confirms your identity through authentication.
AuthZ (Authorization) answers the question, “What are you allowed to do?” It is the process of granting or denying access to resources based on the user’s permissions or roles. Authorization occurs after authentication and determines what actions the authenticated user can perform. For instance, after logging in, an admin user may have access to modify settings, while a regular user can only view them.
In summary, AuthN (authentication) confirms identity, while AuthZ (authorization) defines access. Authentication happens first, followed by authorization to ensure secure and appropriate use of resources.
Build AuthZ (Authorization) with Logto
Logto Cloud offers key authorization services based on open-standard protocols like OIDC, OAuth 2.0, and SAML. Features include Role-Based Access Control, Organizations (Multi-Tenancy), and Custom Token Claims to meet your authorization needs from various perspectives.

