What is personal access token (PAT)? A more secure API token
Explain how personal access tokens (PATs) work, when to use them, how to support API authentication in your services, and how they differ from API keys, API tokens, bearer tokens, OAuth tokens, and passwords.
Personal Access Tokens (PATs) are user-generated tokens that replace passwords for API calls. Designed for specific users, PATs provide secure and controlled access to resources.
Effortless authentication. Granular access control. Streamlined workflows. These are just a few reasons developers and product teams worldwide rely on personal access tokens to supercharge productivity, whether managing CI/CD pipelines, integrating APIs, or accessing tools.
Curious about how PATs work, their benefits, or when to use them? This guide has you covered.
What is a personal access token?
A personal access token is a temporary, secure authentication way to access your personal resources and services through APIs. It’s mainly used by developers to make tasks like accessing APIs or automating workflows simpler and more efficient.
Think of a personal access token as a "key" for API access, replacing the need for a password. Unlike password, PATs have specific permissions and expiration dates, ensuring they’re used only for their intended purpose, like accessing user profiles or billing systems, but not admin controls.
Key features of personal access tokens:
- Developer-friendly: Personal access tokens are easier to manage than full OAuth workflows, making them ideal for scripts, automation, or CI/CD pipelines.
- Multiple tokens: Users can generate and manage multiple personal access tokens, each dedicated to a specific service or purpose.
- User-specific access: Unlike global API keys, personal access tokens are tied to individual user accounts. This means team members may need to create separate tokens for shared access.
- Granular permissions: With personal access tokens, you can define specific scopes, granting access only to the resources and actions required.
- Time-limited access: Personal access tokens can be configured with expiration dates, reducing the risk window in case of exposure.
- Easy revocation: Unlike passwords, personal access tokens can be revoked or regenerated without compromising an account’s primary credentials.
Personal access token vs. Bearer token vs. API token
- Personal access token is a type of API token: A personal access token is a type of user-level API token linked to a user account. It gives permission to access system resources on behalf of the user. PATs are more secure than traditional API keys because they allow fine-grained control over permissions—like restricting access to specific repositories or organizations—and can include expiration dates for added security.
- Personal access token can be used as a Bearer token: A bearer token is a way to authorize API requests, often created dynamically using protocols like OAuth or JWT. A personal access token is a static version of a bearer token, manually generated by a user (e.g., on GitHub). For example, when using a GitHub PAT for API calls, you include it in the request header as
authorization: bearer <your-pat>. In this case, the PAT acts as a bearer token. - API token is a broad term: An API token is a general term for any token used to authenticate API requests. It includes different types, like bearer tokens, OAuth tokens, and personal access tokens. PATs and bearer tokens are simply specific types of API tokens.
Choose your AuthN and AuthZ mechanisms
Before adopting a personal access token, it’s crucial to understand its role within the broader landscape of authentication methods. With several mechanisms to choose from, it’s important to know how they compare. Below is a comprehensive table outlining the key differences between Personal access tokens (PATs), Passwords, API Keys, and OAuth tokens to help you make an informed decision.
- Personal access token: A lightweight authentication method ideal for automated tasks or API access. It provides precise, fine-grained control over permissions, ensuring secure and tailored access.
- Password: A traditional authentication approach used for accessing personal accounts via a user interface. It grants the same permissions as the account owner, offering no additional granularity.
- OAuth token: The most secure method for granting third-party services limited access. It allows users to define specific access scopes without exposing their credentials, ensuring both security and flexibility.
- API key: Typically used for automating API access, API keys are linked to service accounts rather than personal accounts. However, they lack the detailed permission controls available with PATs or OAuth.
| Feature | Password | Personal access token | OAuth token | API key |
|---|---|---|---|---|
| Definition | Users authenticate with a identifier and password. | A token for accessing specific resources or APIs, often with limited permissions. | A system where users grant third-party apps access to their data without sharing credentials. E.g., Google login | A unique string used by clients to authenticate API requests. |
| Scope limitation | Typically grants full access to the user’s account once logged in. | Allows fine-grained control over permissions. | Allows the user to define what the third-party app can access. | Typically grants access to specific API resources. No granular control. |
| Revocation | Difficult to revoke without changing the password, affecting multiple services. | Easily revoked by the user or admin. | Can be revoked without affecting user credentials. | Can be revoked or regenerated at the API service level. |
| Expiration | Does not expire unless changed by the user. | Often long-lived, but configurable to expire. | Access tokens expire after a set time; refresh tokens can extend access. | Often long-lived, but can be rotated or limited by the API provider. |
| Ease of use | Easy to remember but risky if mishandled. | Simple to generate and use for automated tasks. | Requires initial user interaction but offers secure access delegation. | Easy to use in requests but not ideal for user-facing authentication. |
| Best for | Customer-side users’ basic sign-in and verification. | Automation, restricted API resource access, and development in CI/CD Pipelines. | Third-party apps needing limited access to user data without storing passwords. | Backend services, server-to-server communication, and public APIs. |
| Security risk | If stolen, grants full access to the account. | If leaked, only grants access to specified resources. Can be revoked easily. | If leaked, third-party apps can perform actions within granted scope. | If stolen, it’s typically used for server-to-server access. |
How does a personal access token work?
Personal access tokens work much like OAuth access tokens, but are typically strings without user-readable data about its content. When you authenticate with a service like GitHub, you can generate a PAT tied to your user account and assign it specific permissions. This token serves as a secure alternative to using a password when making requests—such as accessing a private repository via an API.
Typically, a PAT is included in the request headers, as shown in this example:
By sending your PAT in this way, the service can verify your identity, assess the permissions linked to your token, and either provide the requested data or carry out the specified action.
How to use personal access token?
- Generate a personal access token: Start by creating a personal access token through the platform you’re using. And selecting specific scopes to define its access permissions (scopes).
- Authenticate API requests: With your personal access token ready, use it to authenticate requests to services requiring secure access. Include the token as a bearer token in the authorization header of your API requests.
- Revoke a personal access token: If you need to deactivate your token, simply revoke it through the platform’s authentication settings. Once revoked, any API requests made with that token will automatically be denied.
When should I use personal access tokens?
Personal access tokens excel in scenarios where you need to provide secure, developer-friendly, and scoped access to your APIs. Here are some ideal use cases:
- Automated tasks: Perfect for scripts or tools that need to fetch data from APIs without requiring developers to embed sensitive credentials.
- Granular permission control: Enable precise access by granting scripts or tools limited permissions, such as access to specific repositories, without exposing full account privileges.
- Temporary access: Ideal for time-sensitive situations, where restricting access duration minimizes security risks.
- Simplified developer access: A convenient way to grant access to individual developers without the complexity of configuring a full OAuth authorization flow.
- Third-party integration: Optimize functionality with external tools by limiting access to specific predefined actions. For example, when a company uses a project management tool, third-party integration can allow team members to create tasks or update statuses directly from a Slack chat without needing full access to the project management tool.
GitHub is driving the use of personal access tokens from 2013, which are becoming popular for being simple and flexible. Many developer tools and SaaS platforms support PATs, making them easy to use and a favorite choice for developers:
-
GitHub/GitLab/Azure DevOps (Development tools): Helps with automating CI/CD, connecting to other tools, and managing code repositories.
-
Figma (Design tools): Makes it easier to collaborate on designs using API integrations.
-
Atlassian Jira / Asana (Project management): Makes it easy to create, update, or delete tasks, manage sprints, and organize projects using APIs.
Can I share a personal access token with other users?
Short answer—No, you shouldn’t.
Tokens are meant to be tied to an individual account and should never be shared. If others require access, it's better to generate unique tokens with their permissions or set up user roles to avoid security risks. Misusing tokens can lead to unintended access, compromised data, or privacy violations. Keep tokens private and revoke any you suspect are compromised.
Enable your application to generate personal access tokens with Logto
Whether you're offering B2B services or developing cutting-edge AI products, implementing developer-friendly authentication and authorization is essential. A personal access token can unlock new opportunities of your business.
Logto, a comprehensive Customer Identity and Access Management (CIAM) solution, allows you to easily create, manage, and revoke personal access tokens. Here's how you can get started:
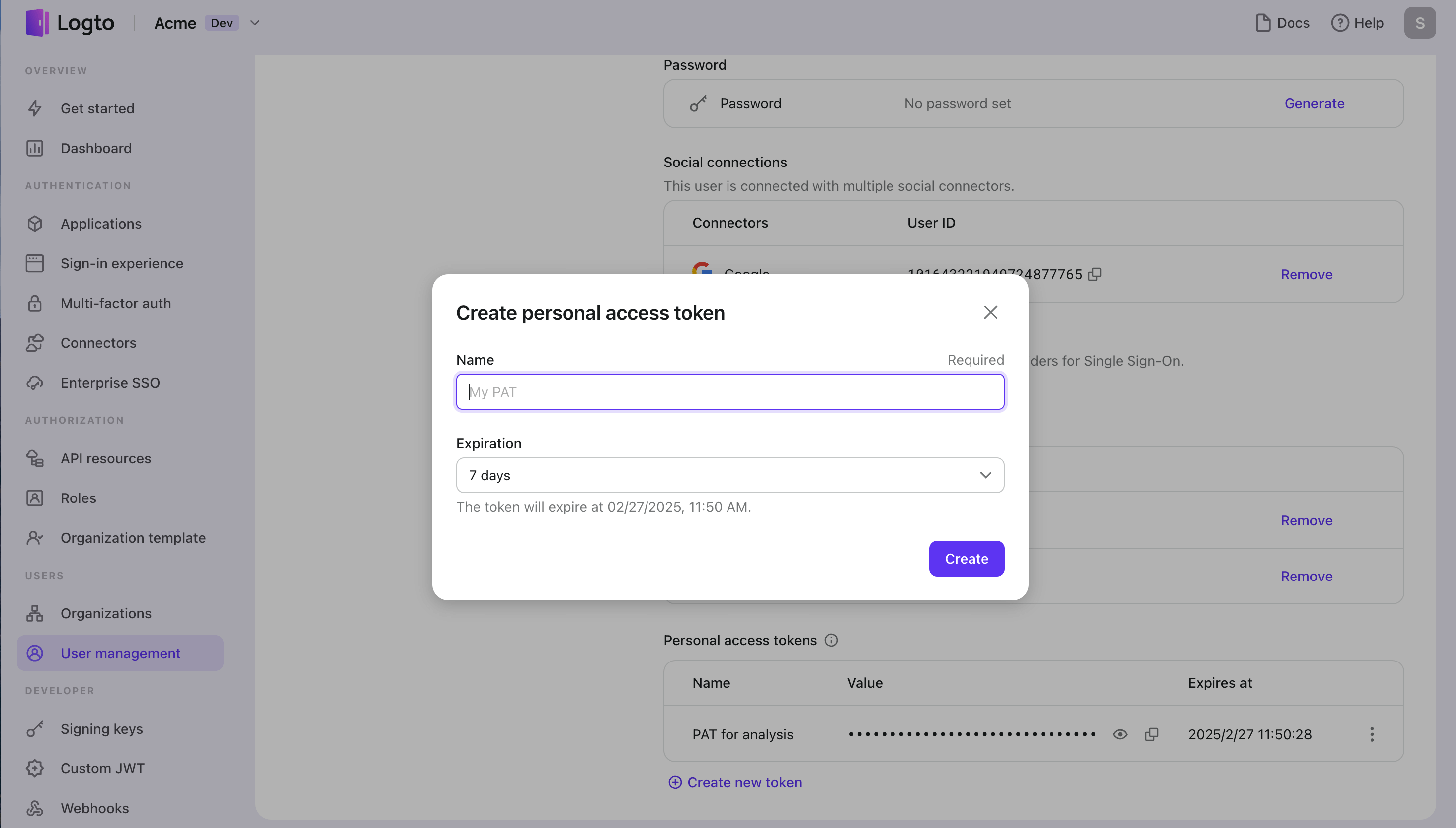
- Navigate to Logto Console > User Management.
- Access the profile of a specific user to manage their personal access tokens.
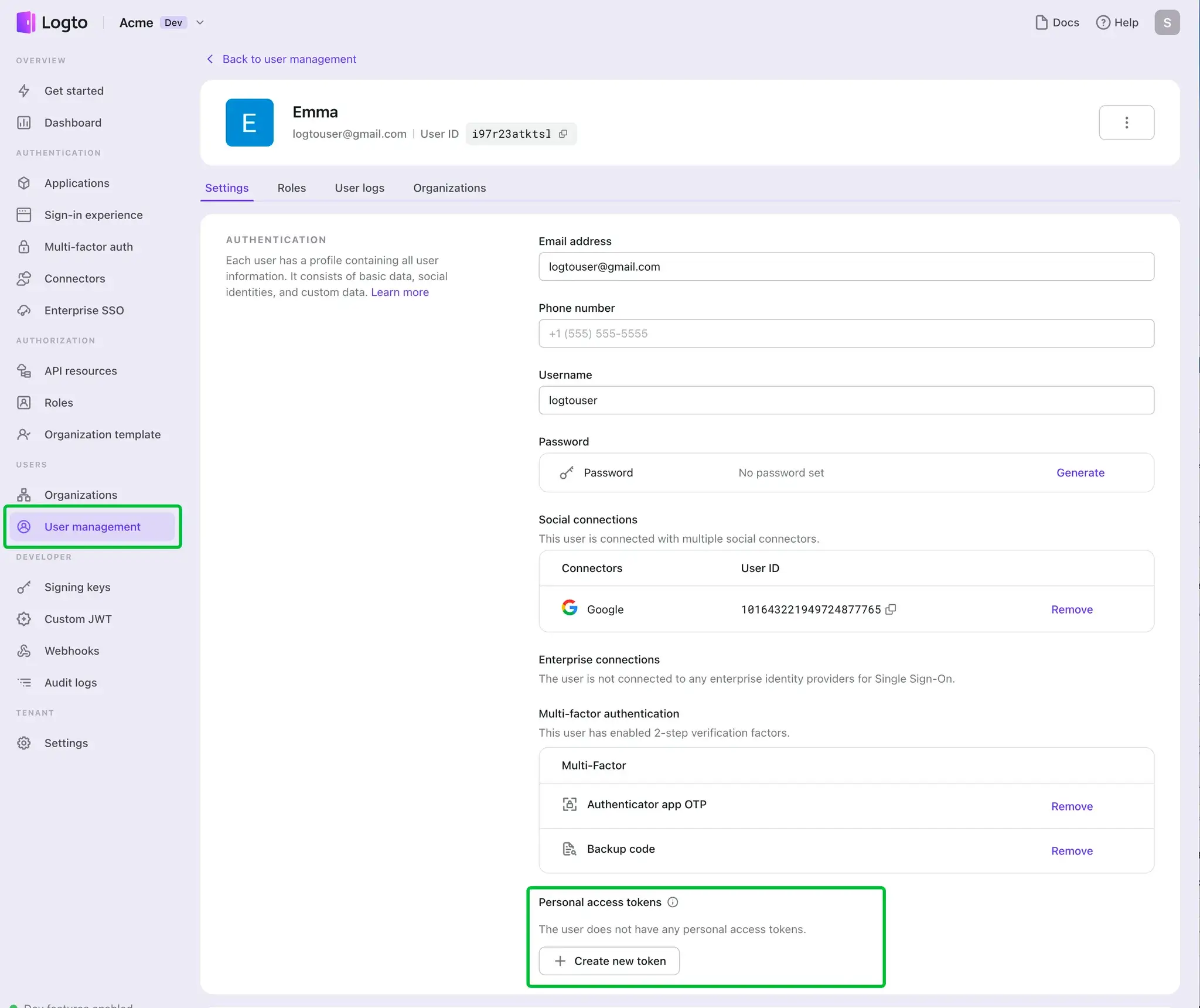
With Logto, you can:
- Generate new personal access tokens.
- Manage multiple tokens for a single user.
- Set custom expiration dates for tokens.
- Rename tokens for better organization.
- Revoke tokens when no longer needed.
Additionally, you can enable users to self-manage their personal access tokens in their profile setting pages through Logto Management APIs.

