GitHub Apps vs. OAuth Apps: Choose the right GitHub connection
Compare GitHub Apps vs OAuth Apps for Logto integration. Learn key differences in security, permissions, token management, and choose the right GitHub authentication method for your application.
When integrating GitHub authentication into your Logto application, you have two options: GitHub Apps and GitHub OAuth Apps. While both enable "Sign in with GitHub" functionality, they offer fundamentally different experiences in terms of security, token management, and API access. This guide will help you understand the key differences and choose the right approach for your use case.
Background: Two paths to GitHub integration
Logto's current documentation walks you through setting up a GitHub OAuth App for social sign-in. This is the simpler, more straightforward option that works great for basic authentication needs. However, GitHub Apps represent the modern, recommended approach by GitHub itself, offering enhanced security features and more granular control.
Think of it this way: OAuth Apps are like giving someone a master key to your house—they get broad access once authorized. GitHub Apps, on the other hand, are like a smart lock system with specific access codes for different rooms—users can grant precise permissions for exactly what your app needs.
Key differences at a glance
Permissions: Broad vs. fine-grained
- OAuth Apps use broad scopes—requesting
repogrants full repository control. - GitHub Apps use fine-grained permissions—you can request just "Issues: Read" without touching code. Users can also select specific repositories during installation, not grant blanket access.
Token security: Permanent vs. expiring
- OAuth Apps issue tokens that never expire (until manually revoked), with no refresh mechanism.
- GitHub Apps use short-lived tokens (1-hour expiration) with automatic refresh support—significantly more secure for long-running applications.
Identity: User vs. bot
- OAuth Apps always act as the authorizing user (e.g.,
@octocat) and share their rate limit (5,000 requests/hour). - GitHub Apps can act independently with their own bot identity (e.g.,
@my-app[bot]) and enjoy scalable rate limits that grow with usage—perfect for automation.
Access control: All-or-nothing vs. selective
- OAuth Apps require one-time authorization for all accessible resources.
- GitHub Apps let users install the app, choose specific repositories, and receive webhook notifications about permission changes—providing better transparency and control.
Persistence: User-dependent vs. independent
- OAuth Apps are tied to the authorizing user—if that developer loses access or leaves an organization, the app stops working.
- GitHub Apps continue to function even if the developer who installed the app leaves your organization—ensuring uninterrupted service for automation and integrations.
Which one to choose?
Both GitHub Apps and OAuth Apps work seamlessly with Logto's social connector. Logto's Secret Vault securely stores tokens from either integration, but each delivers a distinct experience:
Basic social sign-in with OAuth Apps
If you only need to authenticate users (Sign in with GitHub) and don't call GitHub APIs later, the OAuth App path is the quickest:
- Simple setup: users authorize your OAuth App and sign in via GitHub.
- Tokens are long-lived (no refresh): Logto can store the access token in Secret Vault, but there is no refresh flow — tokens remain valid until revoked.
- Best when you only need user identity (email, name, avatar) and don't perform automated API work.
Why choose this: fastest to implement for prototypes or apps that only require login and occasional profile sync.
Enhanced integration with GitHub Apps
Choose a GitHub App when your application needs ongoing access to GitHub APIs, background automation, or stricter security:
- Fine-grained permissions and per-installation repo selection keep access minimal and auditable.
- Tokens are short-lived (typically 1 hour) and GitHub Apps can provide refresh tokens; when enabled, Logto stores both access and refresh tokens in Secret Vault and handles rotation so your backend keeps working without user re-login.
- App identity (bot) improves attribution and scalable rate limits make it more reliable for heavy automation.
Best for:
- SaaS platforms that manage GitHub repositories on behalf of users
- AI agents that interact with code, issues, or pull requests
- Applications requiring sustained API access
- Tools that perform background automation tasks
Setting up a GitHub App with Logto
Setting up a GitHub App follows a similar pattern to OAuth Apps with a few key differences. Migration from OAuth App to GitHub App requires minimal effort.
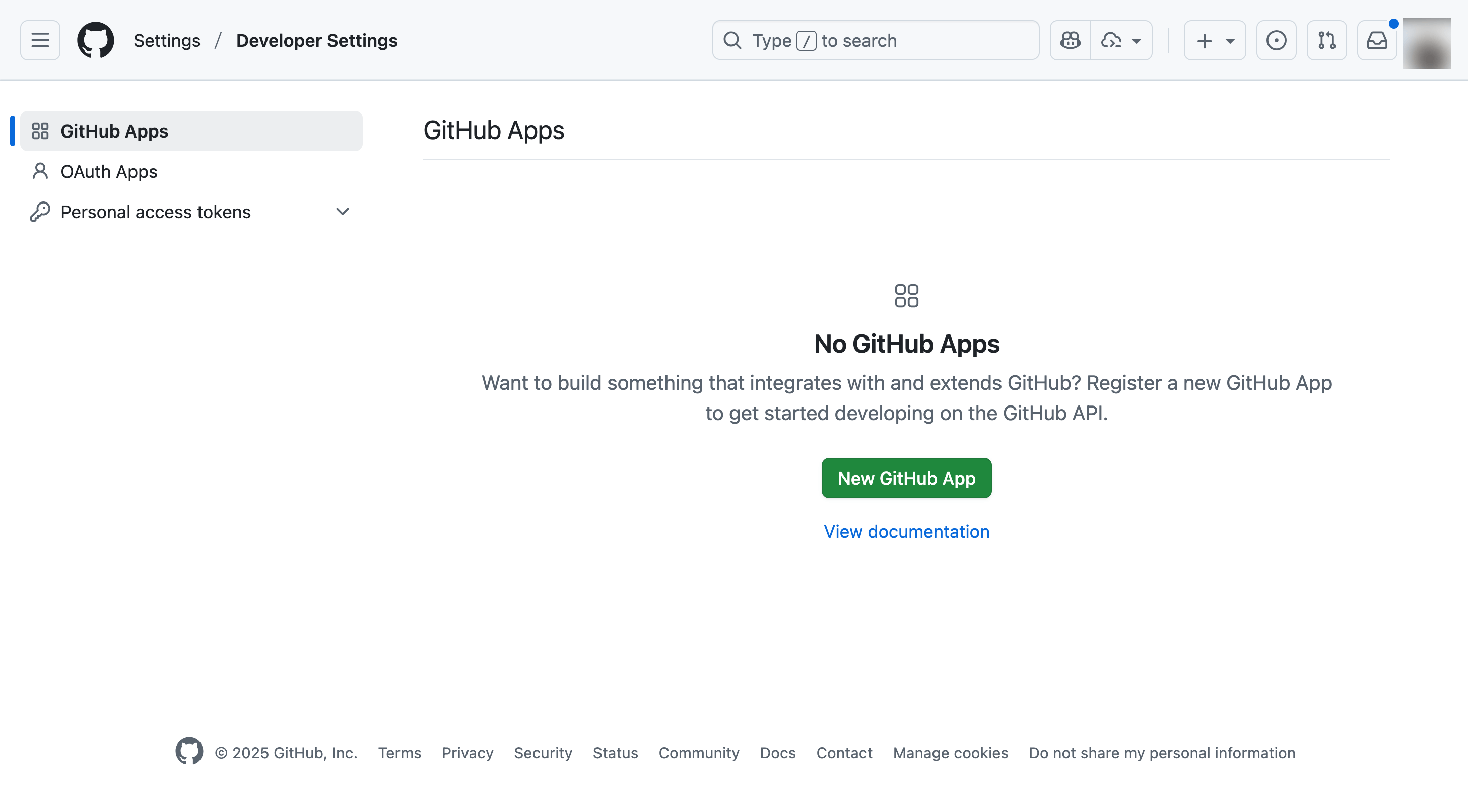
Creating a GitHub App
-
Navigate to "GitHub Settings > Developer settings > GitHub Apps"
-
Click "New GitHub App"
-
Configure:
- GitHub App name: Your app's unique identifier
- Homepage URL: Your application's website
- Callback URL: Your Logto connector's callback URI (same as OAuth App)
- Request user authorization (OAuth) during installation: Enable this
- Webhook: Optional, based on your needs
- Permissions: Select fine-grained permissions (e.g., "Issues: Read")
- User permissions: Add account permissions if acting on behalf of users
-
Generate a client secret (same as OAuth App)
Configuring in Logto
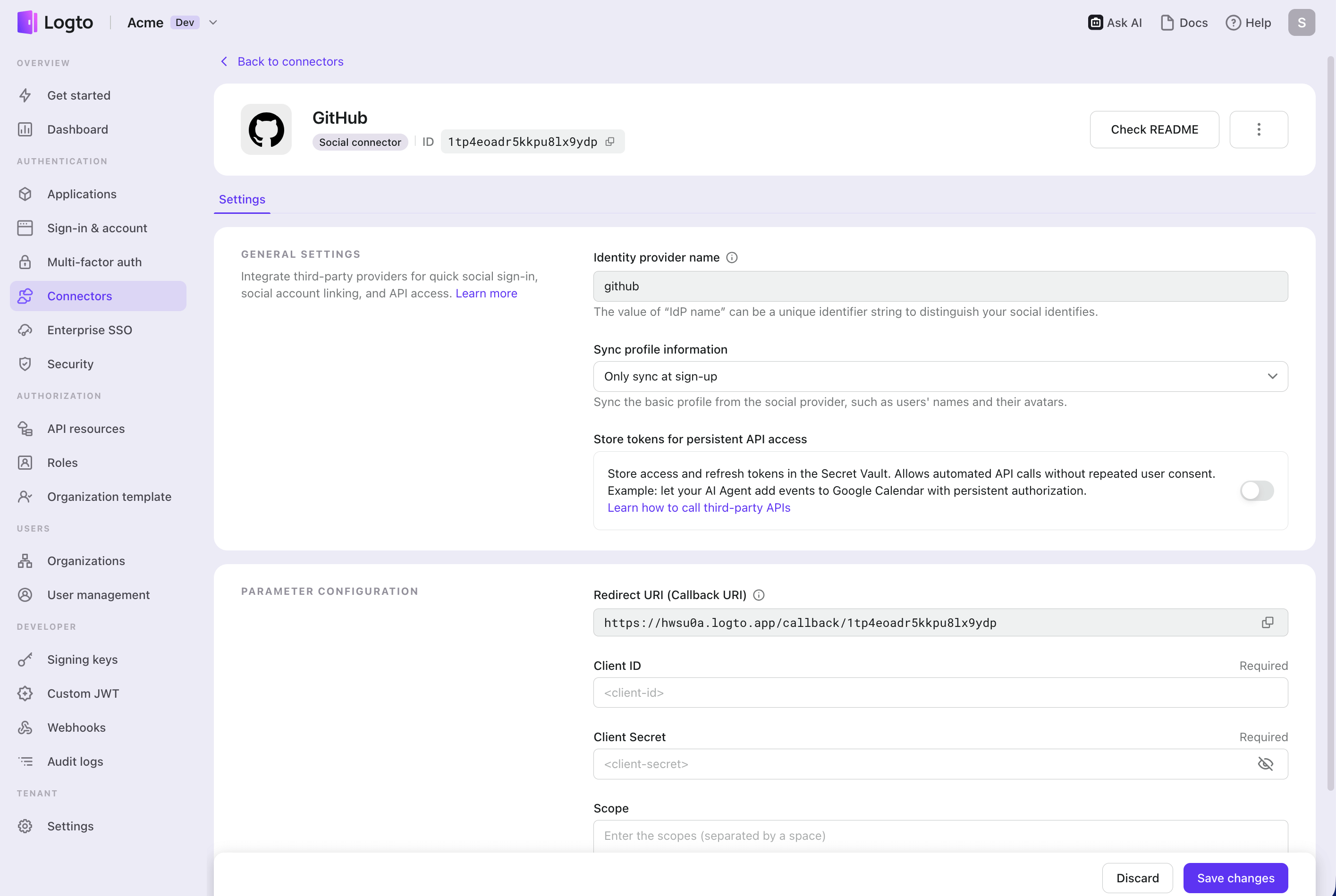
The Logto connector configuration is nearly identical:
- Enter the Client ID from your GitHub App
- Add the Client secret
- Enable "Store tokens for persistent API access" if you need to call GitHub APIs
- Critical difference - Scopes:
- Unlike OAuth Apps (which require adding scopes in Logto's scope field), GitHub App permissions are selected in your GitHub App settings.
- Just leave the scope field empty in Logto
- Request refresh token (optional)
- Add
offline_accessto the scope field in Logto to enable refresh tokens - GitHub automatically issues a refresh token, and Logto handles rotation and stores both tokens in Secret Vault
- Note: OAuth Apps don't support refresh tokens—their access tokens never expire, so
offline_accessdoesn't apply. This is different with using GitHub Apps for integration.
- Add
Conclusion
While OAuth Apps remain a valid option for basic authentication, GitHub Apps represent the future of GitHub integrations. They offer superior security through token expiration, more precise permission models, and better user control over access.
For Logto users, both options work with the social connector. The choice comes down to your specific needs:
- Start simple with OAuth Apps if you only need authentication
- Graduate to GitHub Apps when you need API access, automation, or enhanced security
And remember—Logto's Secret Vault and automatic token refresh capabilities make managing GitHub App tokens as simple as OAuth Apps, without sacrificing security. Whether you're building an AI coding assistant, a project management platform, or a developer productivity tool, you now have the knowledge to choose the right GitHub integration for your Logto application.
Ready to get started? Check out Logto's GitHub connector to begin integrating GitHub authentication today.

