What is impersonation in cybersecurity and identity management? How can AI agents use it?
Learn how impersonation is used in cybersecurity and identity management, and how AI agents can use this feature.
Impersonation is a built-in feature of Logto, and in this article, we’ll explain what it is and when it can be used. As AI agents become more common in 2025, we are seeing more use cases involving impersonation in cybersecurity and identity management.
What is impersonation in authentication and authorization?
Impersonation in the authentication and authorization field is when a system or user temporarily assumes the identity of another user to perform actions on their behalf. This is typically done with proper authorization and is different from identity theft or malicious impersonation.
A common example is when you have a problem with your account and email the customer service team for help. They check your account on your behalf to troubleshoot the issue.
How impersonation works
There are a few typical steps involved in the impersonation flow.
- Request permission: The impersonator (e.g., admin or AI agent) requests permission to act on behalf of the user.
- Token exchange: The system validates the request and exchanges tokens, granting access to the impersonator with the necessary permissions.
- Action on behalf of user: The impersonator performs actions (e.g., updating settings, troubleshooting) as if they were the user.
The impersonator can then perform actions or access resources as if they were the impersonated user.
What are the valid use cases of impersonation?
Customer support
Just like what we mentioned above, in customer support scenarios, impersonation allows support agents or administrators to access user accounts to diagnose and resolve issues without requiring the user’s credentials.
Here are some examples
- Troubleshooting: An admin impersonates a user to recreate the reported issue and understand what’s happening.
- Account recovery: An admin updates a user’s profile or resets settings on their behalf.
- Subscription management: A billing support agent fixes subscription errors by accessing the user’s account directly.
AI agents
AI agents can leverage impersonation to act on behalf of users, performing tasks automatically or assisting with workflows. As AI becomes more involved in business processes, impersonation plays a key role in enabling autonomous actions while ensuring identity security and access control.
Here are some examples
- Virtual assistants: An AI agent schedules meetings and sends calendar invites on behalf of the user.
- Automated responses: An AI chatbot responds to customer inquiries and uses a support agent’s profile to solve issues directly.
- Task automation: An AI assistant updates project management boards or submits reports on behalf of users. For example, update ticket statuses (e.g., from “In Progress” to “Completed”). Post comments or feedback from a manager’s profile.
Audit and testing
Impersonation is also commonly used for auditing, testing, and quality assurance purposes. By impersonating different roles, admins or testers can check user experiences, workflows, and permissions to ensure system performance and quality.
Here are some examples
- Role testing: An admin impersonates different user roles (like manager, employee, or guest) to check access controls and ensure each role has the correct permissions to the right resources.
- Workflow testing: A QA engineer simulates transactions from various user profiles to test system behavior.
- Security audits: An auditor impersonates users to verify that sensitive actions trigger appropriate alerts or require multi-factor authentication (MFA).
Delegated access
Delegated access allows one user to perform actions on behalf of another, often seen in enterprise and team collaboration settings. This use case differs from typical impersonation because both the actor and delegator identities are preserved.
Here are some examples
- Manager approvals: A manager submits timesheets or expense reports on behalf of their team members.
- Team collaboration: An assistant schedules meetings or sends emails from an executive’s account.
- Enterprise workflows: HR representatives update employee records without needing their passwords.
To implement impersonation, what are the security considerations for this
Impersonation allows a user to temporarily act on behalf of others within the system, which gives them significant power and control. That’s why it’s necessary to address several security considerations to prevent misuse.
Detailed audit logging
Log every impersonation action, including who did it, what was done, when it happened, and where it occurred. Make sure the logs show both the impersonator and the impersonated user. Store logs securely, set reasonable retention periods, and enable alerts for any unusual activity.
Role-based access control (RBAC)
Only allow authorized roles (e.g., support agents) to impersonate. While limit impersonation scope (e.g., support agents can only impersonate customers not admin). Follow the principle of least privilege and regularly review permissions to keep things secure.
Consent and notification
Sometimes, the flow should include consent and notifications. For example:
- Before impersonation: Request user approval for sensitive actions.
- After impersonation: Notify users with details of what was done.
- For sensitive industries (e.g., healthcare, finance), consent is a must.
AI agent use cases for impersonation in authentication and authorization
As AI agents become more prevalent in 2025, impersonation is increasingly used to enable agents to act on behalf of users while maintaining security and accountability.
Here are some practical use cases:
AI customer support agents
Scenario: A user contacts support via chat for account issues. The AI agent accesses their account and performs actions without needing the user’s password.
How does it work, and how is it designed?
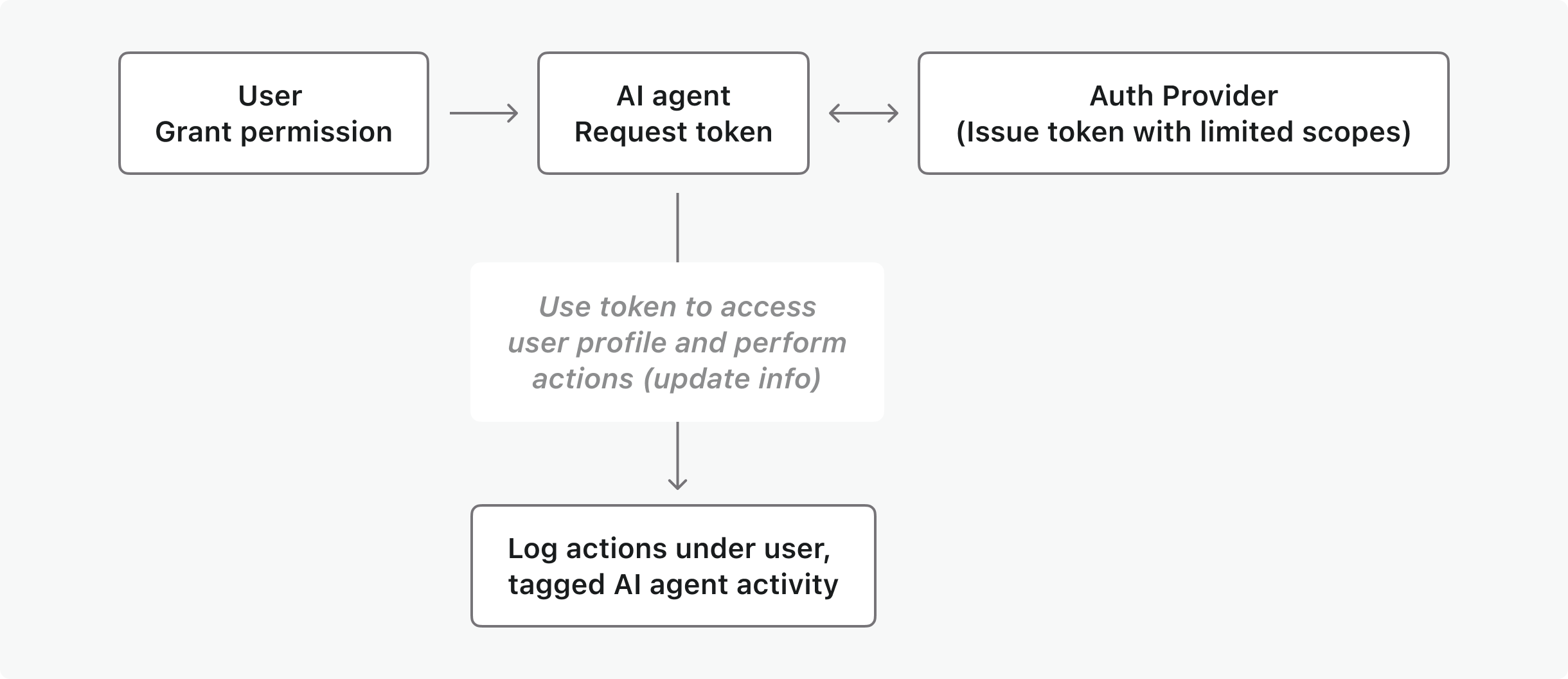
- OIDC/OAuth flow: The AI agent requests permission to impersonate the user to update their information. It uses an exchanged token to access the user’s profile and make the changes.
- Logging: Actions are logged under the user but tagged as performed by the AI agent.
- Limited scopes: The agent’s permissions are limited to specific actions (e.g., resetting passwords but not viewing sensitive payment data).
AI security agents for account monitoring
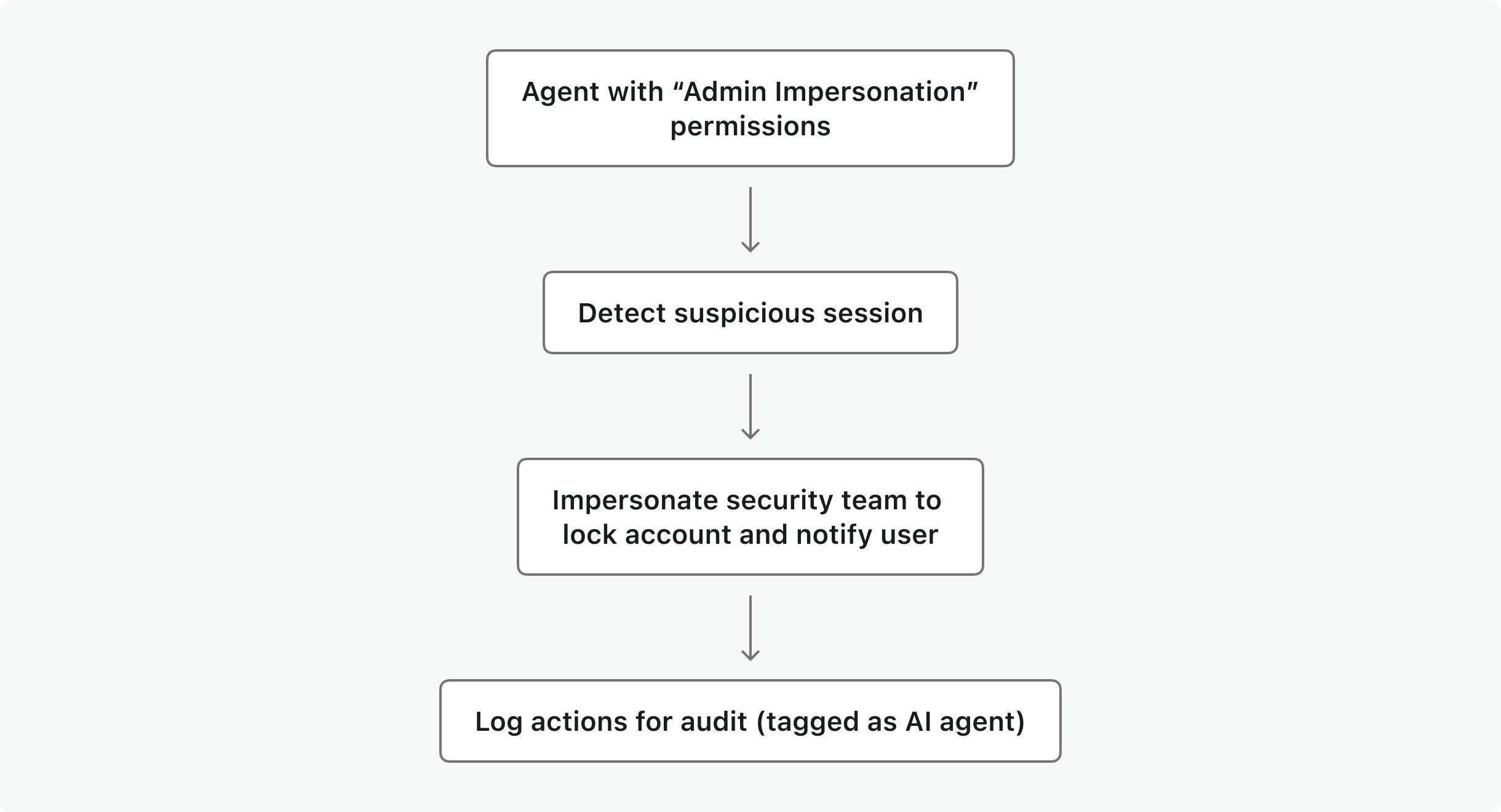
Scenario: An AI agent monitors user sessions and locks compromised accounts automatically.
How does it work, and how is it designed?
- The agent has “admin impersonation” permissions to inspect and terminate suspicious sessions.
- If a risk is detected, it impersonates the security team to lock the account and notify the user.
- All actions are recorded with the agent’s identity for audit purposes.
AI workflow automation for teams
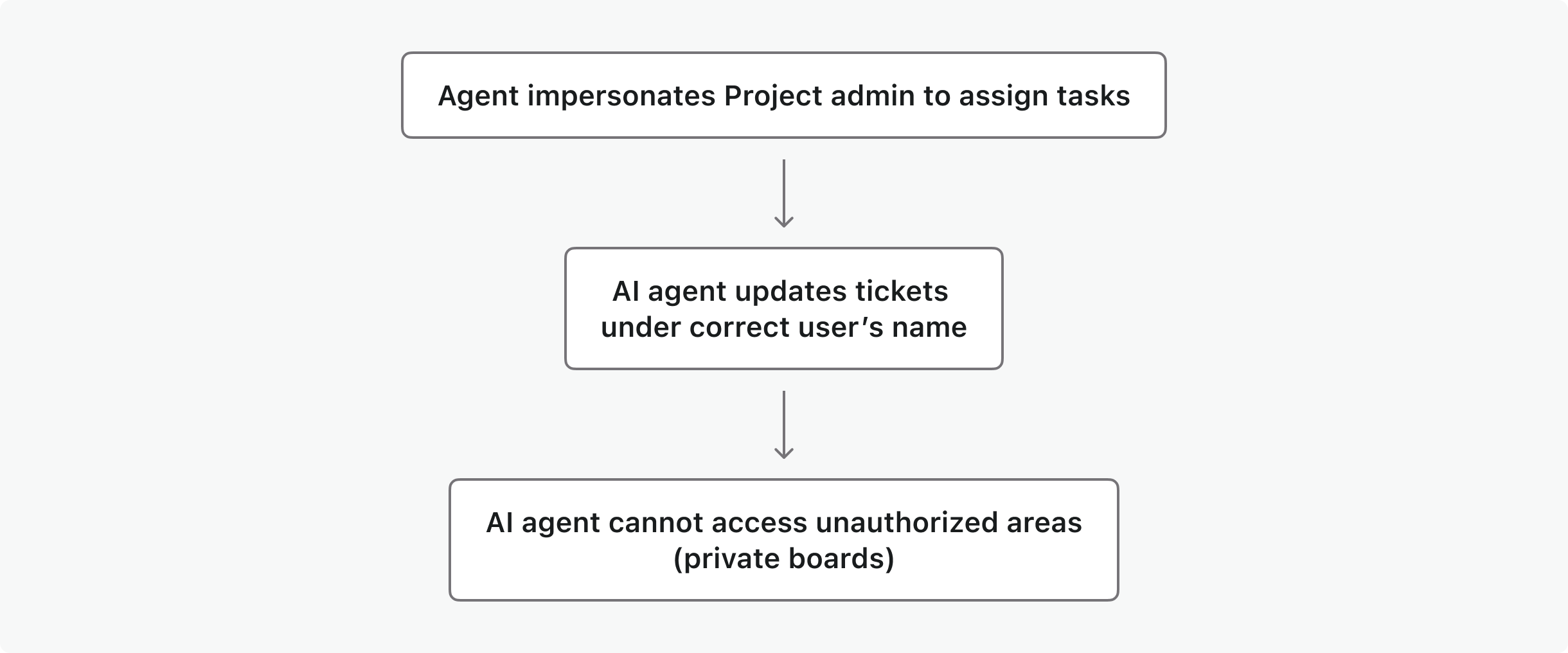
Scenario: In a project management tool, an AI agent automatically assigns tasks and updates status on behalf of team members.
How does it work, and how is it designed?
- The AI automated workflow can impersonate the project admin to update tickets under the correct user’s name.
- The agent cannot access unauthorized areas (e.g., private boards) due to strict RBAC.
Security best practices for building impersonation
Based on the above scenarios, there are a few principles designed in mind to achieve those goals.
- Token scoping: Use limited scopes. Make sure to definie and limit what actions or resources an access token can authorize.
- Custom claims: This can be useful for adding additional context or metadata to the impersonation process, such as the reason for impersonation or the associated support ticket.
- Role-based access control (RBAC): Only allow certain roles (e.g., support agents) to impersonate users and restrict the scope based on the role’s needs.
- Detailed logging: Record all impersonation actions, including who performed them and what was done, to ensure accountability and traceability.
- Consent management: Notify users when impersonation occurs and give them the option to approve or revoke access.
How Logto implements impersonation?
Logto supports impersonation through its management API.
Check out this guide - user impersonation for more details. Logto also offers additional features that integrate impersonation, supporting real-world product scenarios.
| Features | Description | Doc link |
|---|---|---|
| Role-based access control | Assigning permissions to users based on their roles | https://docs.logto.io/authorization/role-based-access-control |
| Custom token claims | Add customize claims within access tokens. | https://docs.logto.io/developers/custom-token-claims |
| Audit logs | Easily monitor user activity and events. | https://docs.logto.io/developers/audit-logs |

