Using Logto as an third-party identity provider (IdP)
Logto can be used as an identity provider for your third-party applications. This article explains how to configure Logto as an IdP.
Logto is a cloud-based identity and access management (IAM) platform that provides a comprehensive set of authentication, authorization, and user management capabilities. It can be used as an identity provider (IdP) for your third-party applications or services, allowing you to authenticate users and manage their access to these applications.
In this article, we will explain how to configure Logto as an IdP for your third-party applications and how to use it to authenticate users and manage their permissions.
What is an identity provider (IdP)?
An Identity Provider (IdP) is a service that verifies user identities and manages their login credentials. After confirming a user's identity, the IdP generates authentication tokens or assertions and allows the user to access various applications or services without needing to log in again. Essentially, it's the go-to system for managing employee identities and permissions in your enterprise.
What is a third-party IdP?
A third-party IdP is an IdP that is owned by a different organization than the service provider (SP). The SP is requesting access to the user data that is not owned by itself. For example, if you are using Logto as your IdP, and sign in to a third-party social App, then Logto is a third-party IdP for the social App.
In the real world, many applications use Google, Facebook, or other third-party services as their IdP. It's called Single Sign-On (SSO). To learn more about SSO, please check out our article CIAM 101: Authentication, Identity, SSO.
Now let's see how to integrate Logto as a third-party IdP for your applications.
How to integrate a third-party IdP for your applications and its best practice
Prerequisites
-
Before you begin, you need to have a Logto account. If you don't have one, you can sign up for a free account at Logto.
-
A third-party application that you want to set up Logto as a IdP. Users can sign in with their Logto accounts.
Create an third-party OIDC application in Logto
To create a third-party OIDC application in Logto, follow these steps:
-
Go to the Logto Console and navigate to the Applications page.
-
Click on the create application button located in the top-right corner of the page. Select "Third-party app -> OIDC" as the application type.
-
Fill in the basic application details, including the name and description, in the pop-up modal. Click the create button. This will generate a new third-party application entity in Logto and jump to the details page.
Set up the OIDC configuration
Follow these steps to configure the OIDC settings under the application details page:
-
Navigate to the application details page of the third-party application you just created.
-
Provide a redirect URI of your third-party application. This is the URL that the third-party application will redirect users to after they are authenticated by Logto. You can usually find this information in the third-party application's IdP connection settings page.

(Logto supports multiple redirect URIs. You can add more redirect URIs by clicking on the Add another button.)
-
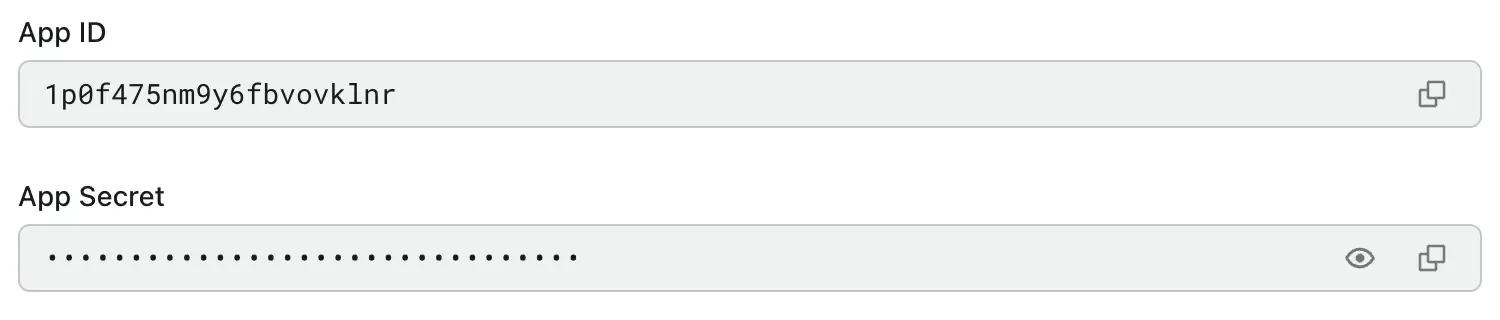
Copy the client ID and client secret from Logto and enter them into your service provider's IdP connection settings page.
-
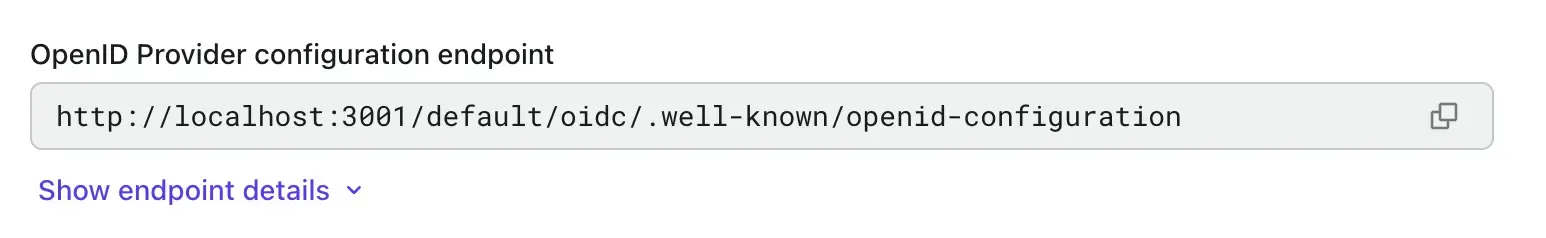
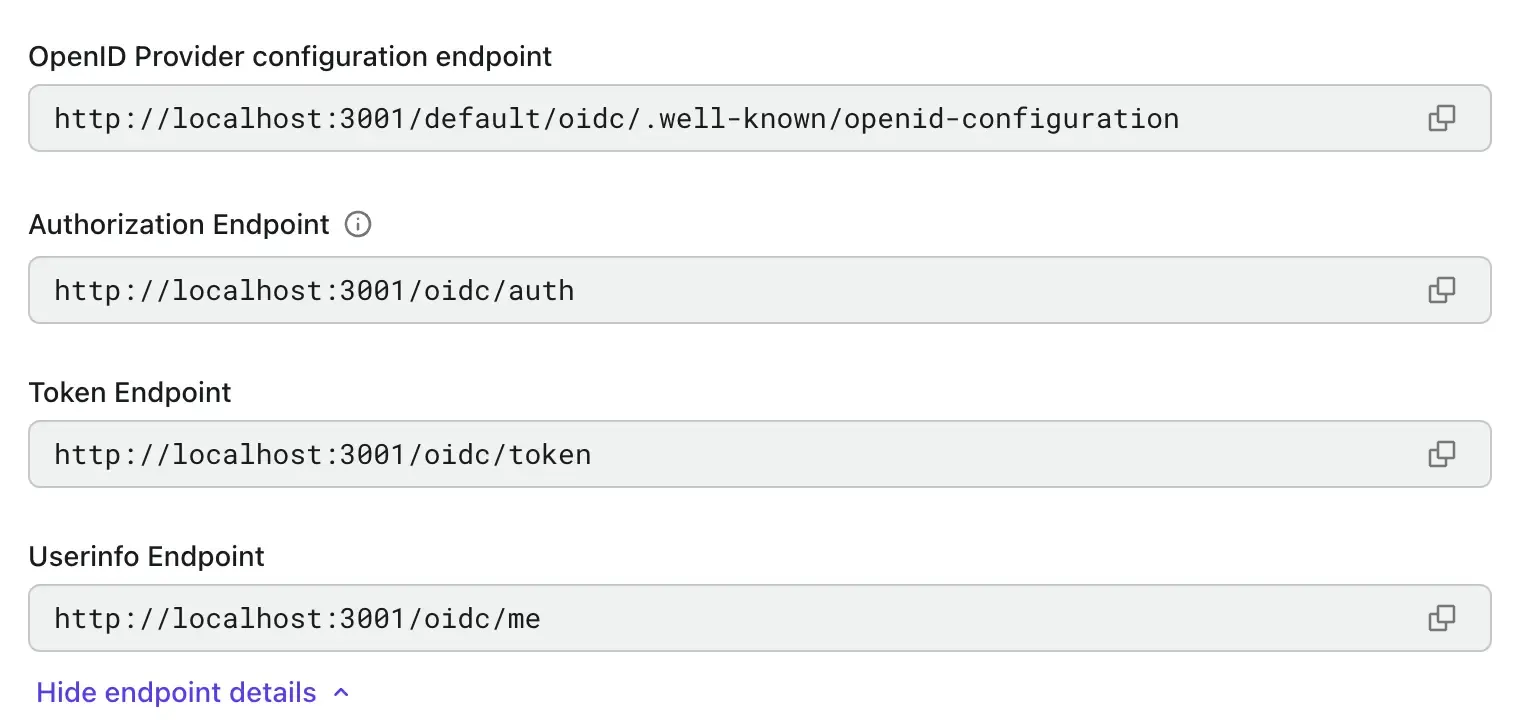
Copy the OIDC discovery endpoint from Logto and enter it into your service provider's IdP connection settings page.
The OIDC discovery endpoint is a URL that the service provider can use to discover the OIDC configuration details of the IdP. It contains information such as the authorization endpoint, token endpoint, and user info endpoint your service provider needs to authenticate users with Logto.
Check point
With all the OIDC configuration details in place, you can now use Logto as a third-party IdP for your applications. Test the integration on your third-party application to ensure that users can sign in with their Logto accounts.
Manage application permissions
Unlike first-party applications, third-party applications are applications that are not owned by Logto. They are usually owned by third-party service providers use Logto as a external IdP to authenticate users. For example, Slack, Zoom, and Notion are all third-party applications.
It is important to ensure to grant the correct permissions to third-party applications when they are requesting access to your users' information. Logto allows you to manage the permissions of your third-party applications, including the user profile scopes, API resource scopes, and organization scopes.
Requesting a non-enabled scopes will result in an error. This is to ensure that your users' information is protected and only accessible by the third-party applications that you trust. Once the scopes are enabled, the third-party applications may request access to these enabled scopes. These scopes will be displayed on the consent page for your users to review and grant access to the third-party applications.
Please check out our article User consent screen for more details about what is a user consent screen.
Add permissions to your third-party applications
Go to the Application details page and navigate to the Permissions tab. Click on the Add permissions button to and the permissions of your third-party applications.
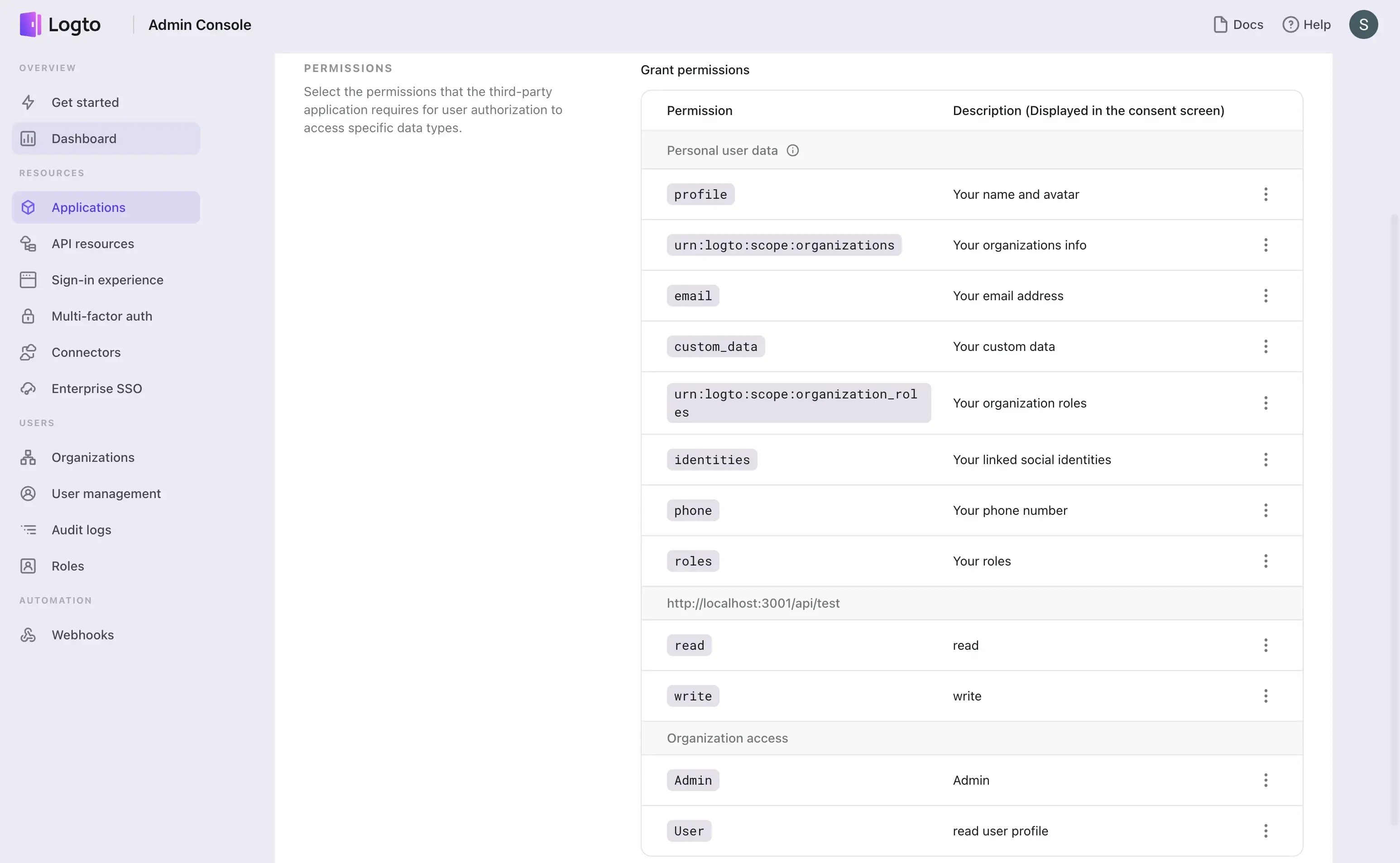
User permissions (User profile scopes)
Those permissions are OIDC standard and Logto's essential user profile scopes used for accessing user claims. User claims will be returned in the ID token and userinfo endpoint accordingly.
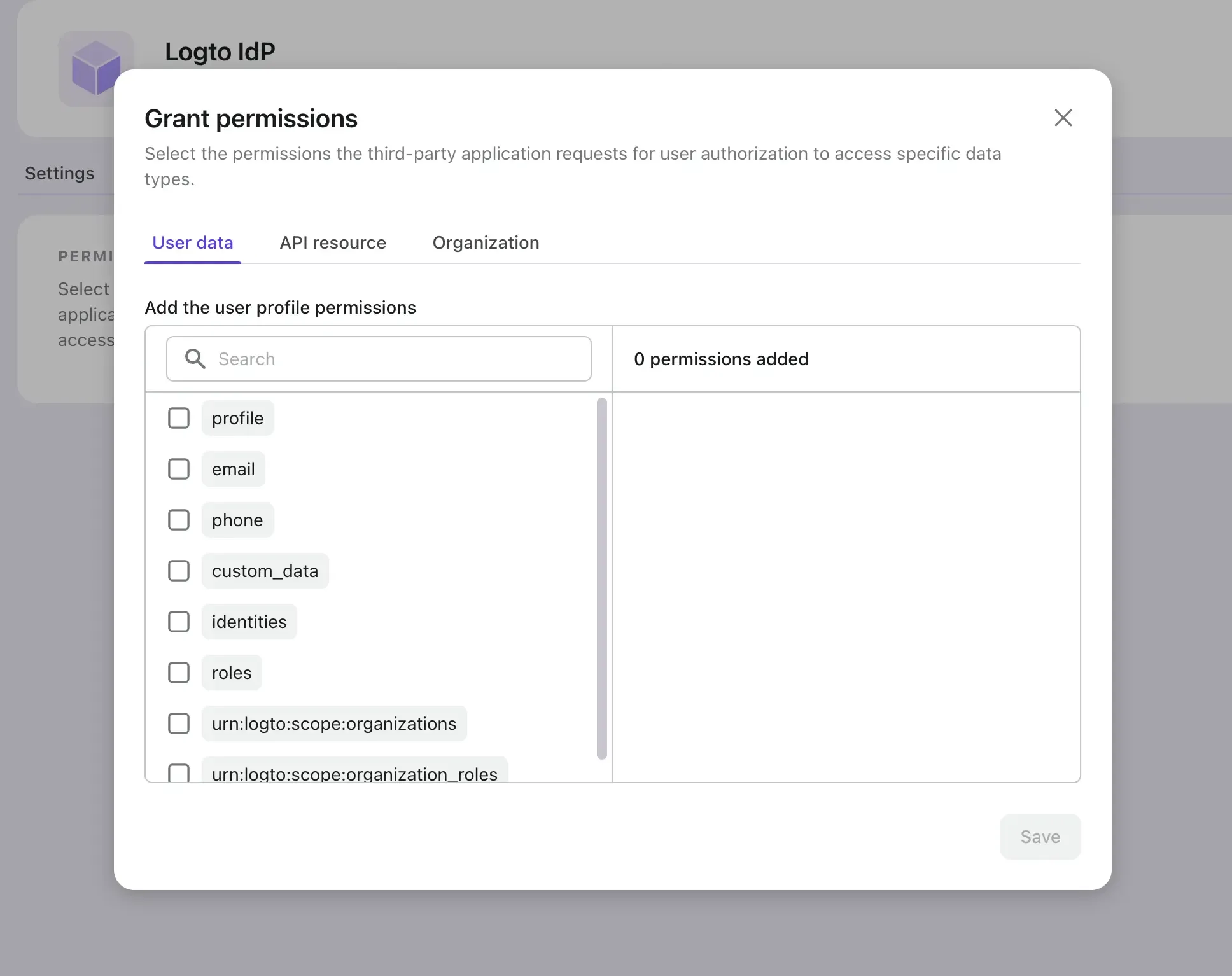
API resource permissions (API resource scopes)
Logto provides RBAC (Role-based access control) for API resources. API resources are the resources that are owned by your service and are protected by Logto. You may assign self-define API scopes to the third-party applications to access your API resources. If you don't know how to use these API resource scopes Please check our RBAC and protect your API guides.
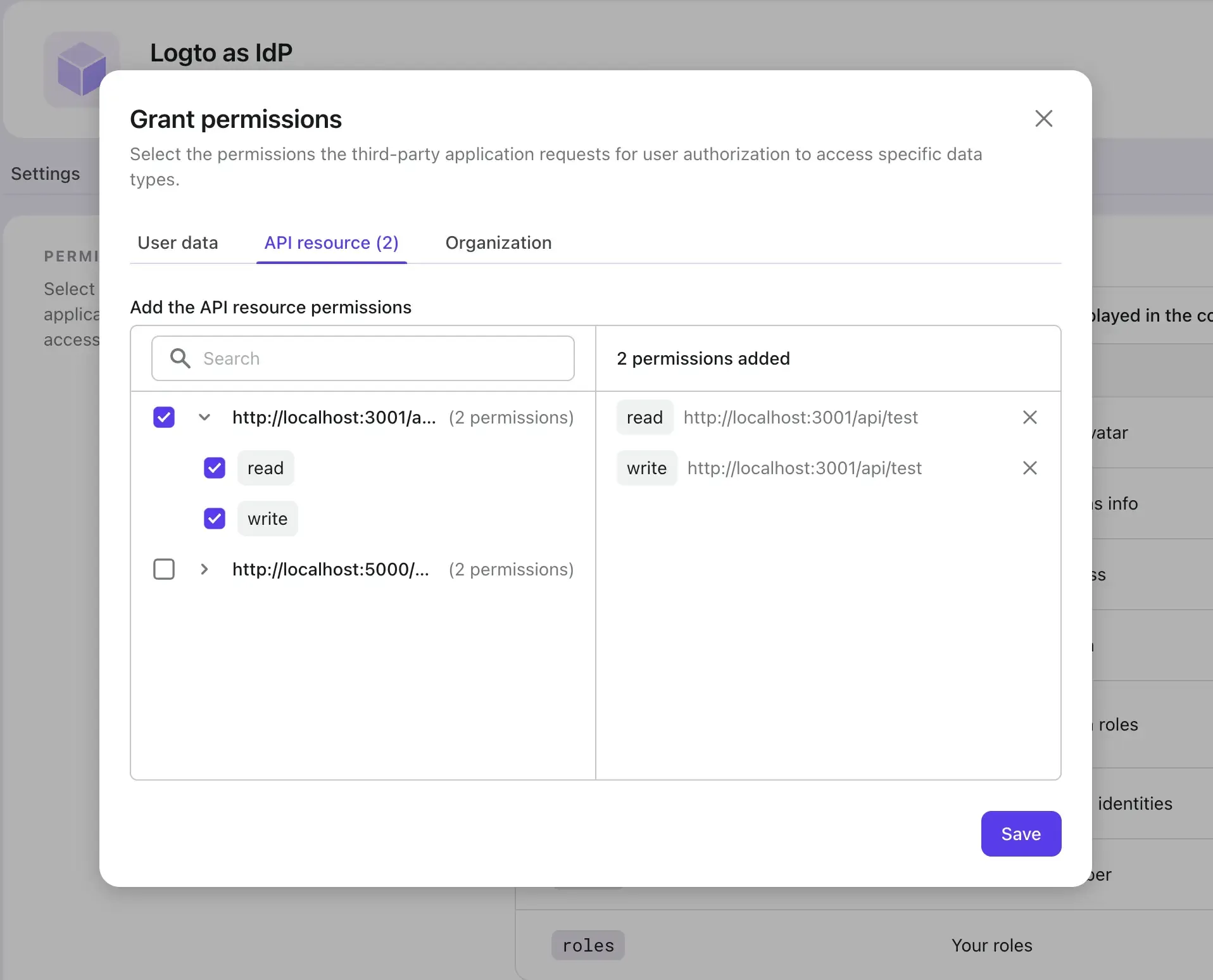
You may create and manage your API resource scopes under the API resources page in Logto console.
Organization permissions (Organization scopes)
Organization permissions are the scopes that defined exclusively for Logto organizations. They are used for accessing organization information and resources. To learn more about organizations and how to use organization scopes, please check our organization guide.
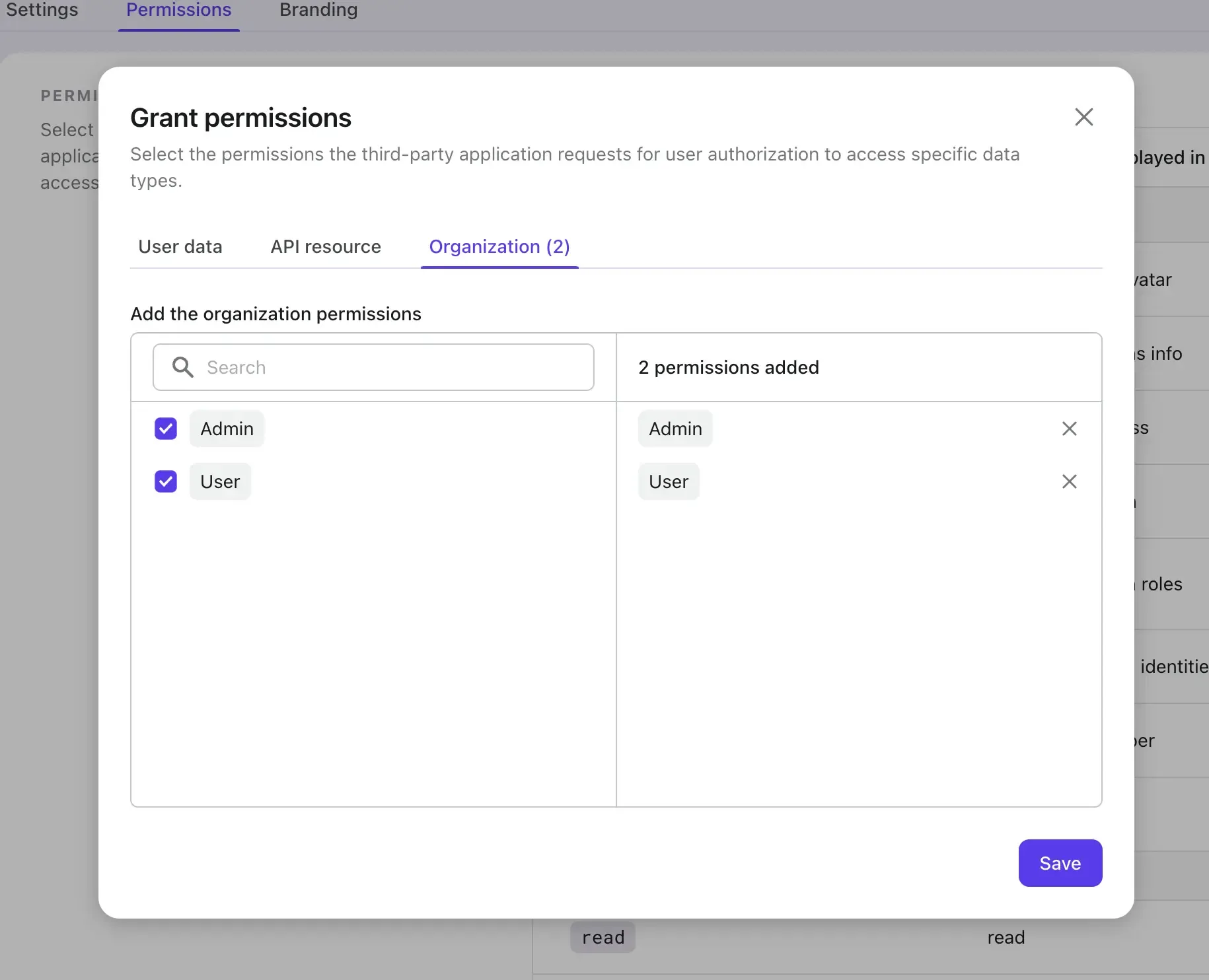
To create and manage your organization scopes go to the Organization template page in Logto console. Please see Configure organizations for more details.
Consent page
Once all the permissions are enabled, the third-party applications may request access to the enabled permissions. These permissions will be displayed on the consent page for your users to review and grant access to the third-party applications.
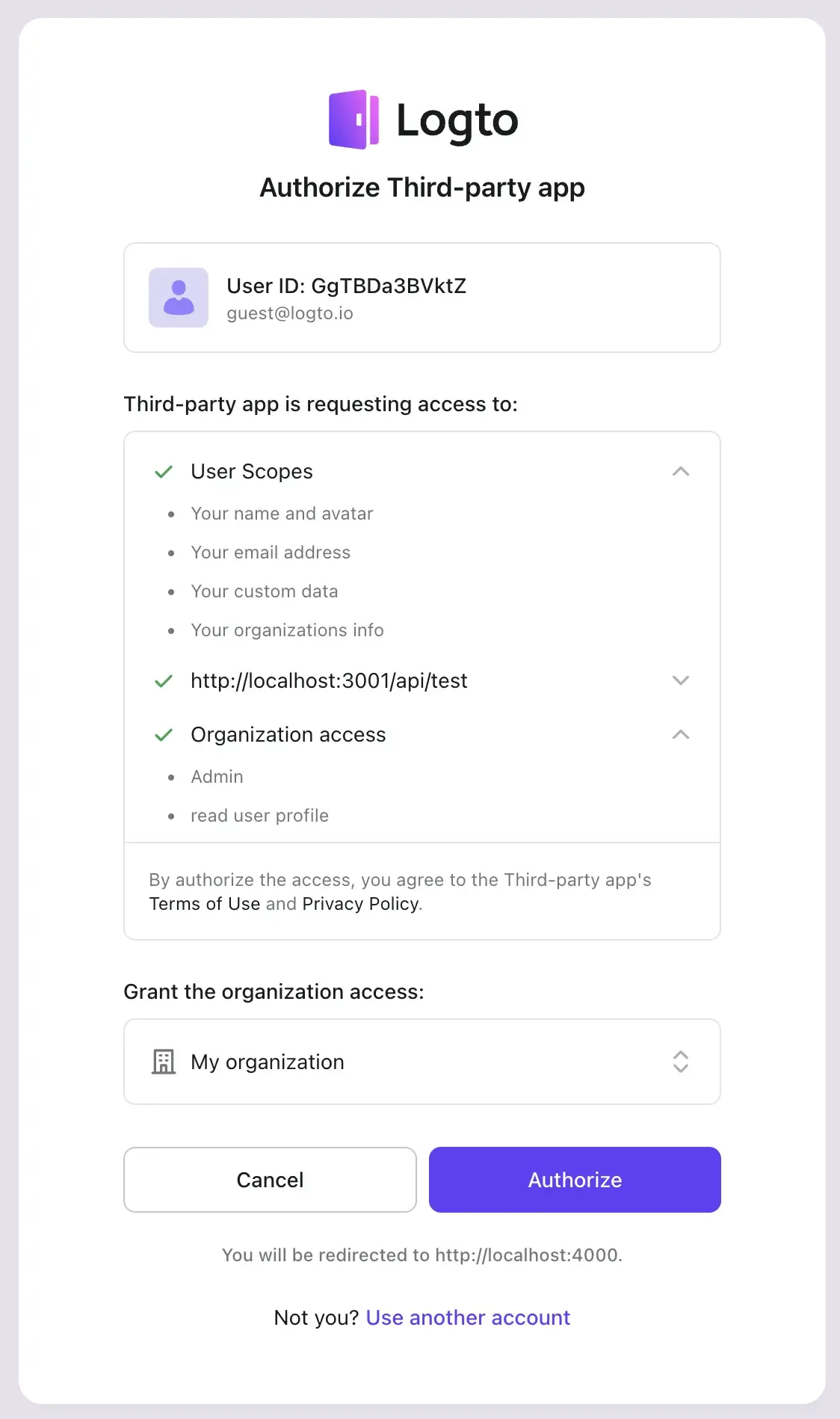
By clicking on the Authorize button, the user will grant access to the third-party applications to access those requested permissions.
Customize the consent screen
Last but not least, it is important to ensure the third-party's branding information and privacy link is properly displayed to the users when they are redirected to the third-party application's consent page.
Apart from first-party applications' universal sign-in experience, Logto allows you to customize these additional branding information of your third-party applications, including the application name, logo, and terms link.
-
Go to the Logto Console and navigate to third-party application's details page.
-
Navigate to the Branding tab.
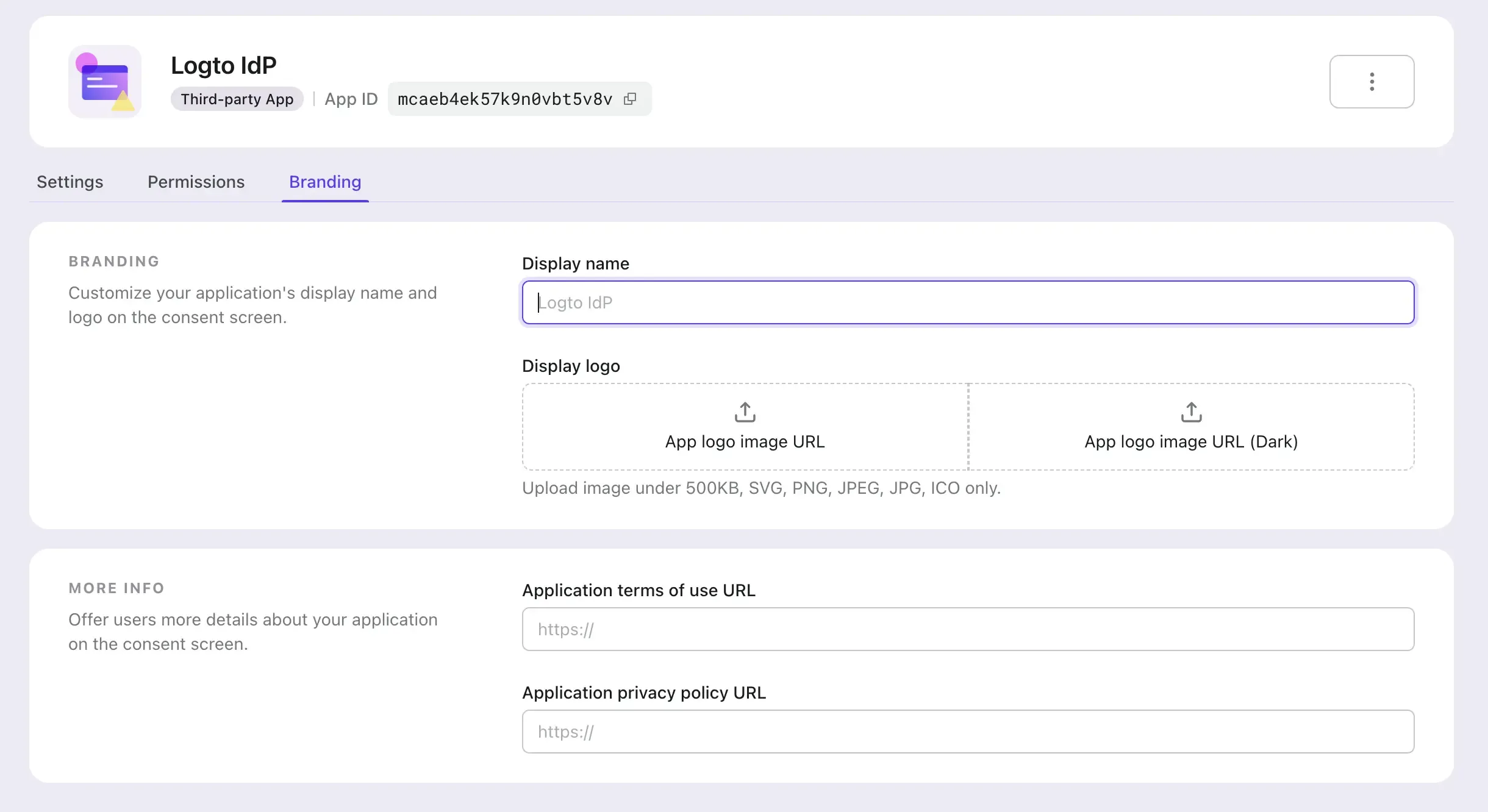
- Display name: The name of the third-party application that will be displayed on the consent page. It will represent the third-party application's name who is requesting access to your users' information. Application name will be used if this field is left empty.
- Logo: The logo of the third-party application that will be displayed on the consent page. It will represent the third-party application's brand who is requesting access to your users' information. Both third-party application's logo and Logto universal sign-in-experience logo will be displayed on the consent page if both are provided.
- Dark logto: Only available when dark-mode sign-in experience is enabled. Manage the dark-mode settings at the Sign-in experience page.
- Terms link: The terms link of the third-party application that will be displayed on the consent page.
- Privacy link: The privacy link of the third-party application that will be displayed on the consent page.
Summary
Congratulations! You've effectively integrated Logto as a third-party IdP for your applications. By configuring the OIDC settings, you've established a robust and secure mechanism for user authentication and authorization. With Logto in place, you now have a smooth process to authenticate users and regulate their access to any third-party applications.

