Magic link authentication
Learn to implement magic links for passwordless sign-in, invitation-only registration, and organization member invites using one-time tokens.
What is a magic link?
A magic link is a passwordless authentication method where a user receives a one-time login URL via email (or SMS). Clicking the link logs them in without requiring a password.
Here are some key security features of magic links:
- Single-use token: Once clicked, the token becomes invalid to prevent reuse.
- Link expiry: The magic link should have a short expiration time (e.g., 10 minutes) for added security.
- Rate limiting: Prevent abuse by limiting how many magic links can be sent in a specific timeframe.
- Device/browser binding (Optional): Restrict the link's usage to the original device or IP to prevent interception.
Composition of a magic link
A magic link consists of:
- The URL route: Points to the landing page for your app.
- One-time token: A unique and one-time-consumption token used for passwordless authentication.
- User email: Used to validate the authenticity of the token and the user's identity.
- Additional parameters: Optional, depending on your app’s needs.
For example, a magic link might look like this:
To create a magic link, you need to generate a one-time token, send it securely to the user, and then validate it when the user clicks the link.
Workflow of a magic link
- User requests a magic link: The user enters their email on your app.
- One-time token generation: The server generates a token and sends it as a link via email.
- User clicks the link: The user clicks the link in the email.
- Token validation: The server checks if the token is valid.
- User is authenticated: If the token is valid, the user is logged in.
How to implement magic links with Logto?
Step 1: Request one-time token
Use Logto Management API to create a one-time token.
Sample request body payload:
Step 2: Compose your magic link
After you get the one-time token, you can compose a magic link and send it to the end user's email address. The magic link should at least contain the token and the user email as parameters, and should navigate to a landing page in your own application. E.g. https://yourapp.com/landing-page.
Here's a simple example of what the magic link may look like:
Note:
The parameter names in the magic link can be fully customized. You may add additional information to the magic link based on your application's requirements, as well as encoding all the URL parameters.
Step 3: Trigger the authentication flow via Logto SDK
After the end user clicks the magic link and navigated to your application, you can extract the token and email parameters from the URL, and then call the signIn() function from Logto SDK to trigger the auth flow.
For more details, check the Logto Docs - Magic Link (One-time Token).
Magic link use cases
Magic links can replace the first-factor authentication step, but cannot bypass Multi-Factor Authentication (MFA).
In Logto, when generating a magic link with a one-time token, you don’t need to specify whether it’s for sign-in or sign-up. We automatically determine the flow based on the email's registration status:
- Unregistered email: Clicking the magic link redirects users to the account creation flow, skipping email entry and verification. Users proceed to set a password, add profile details (e.g., full name), or set up MFA, based on your sign-up settings.
- Registered email: Clicking the magic link bypasses the first-step verification (e.g., “email + password” or “email + verification code”). The user is either signed in directly or prompted to complete MFA, based on your sign-in settings.
Logto supports the following scenarios with magic links:
- Invitation-only registration: For internal tools or AI products in the testing phase, you can disable public registration and invite specific users via a magic link.
- Organization member invitation: For SaaS products, use magic links to invite new members to an organization, making the membership process easier.
- Sign-in / Sign-up: Send a magic link for sign-in or sign-up via email.
Currently not supported:
- Password reset with magic link.
- Using phone number or username as the identifier.
Let us know if you need further customization.
Invitation-only registration with magic link
For new products (e.g., AI tools) in internal testing or for internal tools, you may want to disable public registration and allow only specific users to access your app. To implement this with Logto:
-
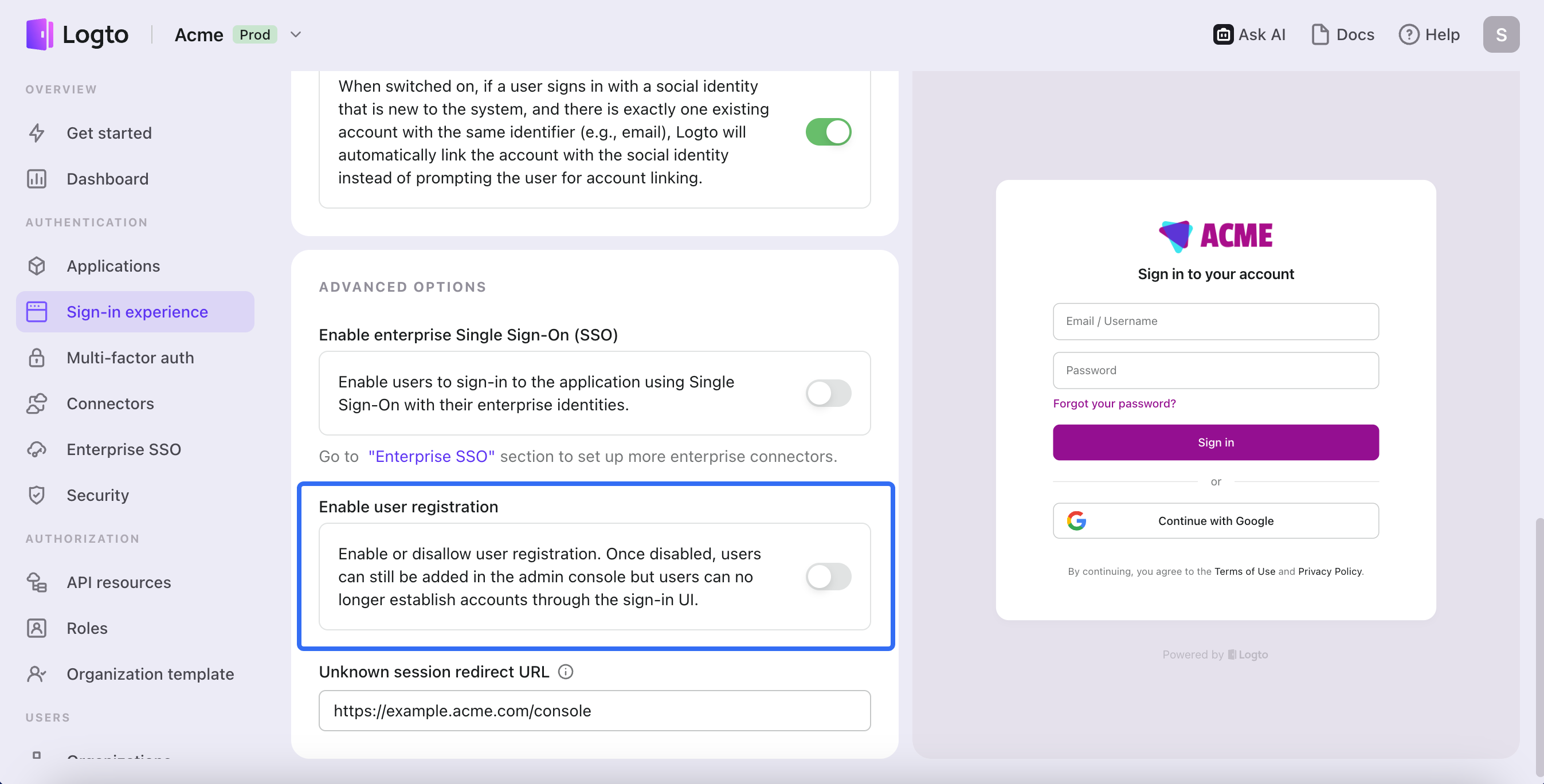
Go to Console > Sign-in experience > Sign-in and sign-up > Advanced options, and toggle off "Enable user registration" to close public registration.
-
Collect the email addresses of the users you want to invite (e.g., via your website or recommendations from existing users).
-
Create and send the magic invitation link as outlined above (request the one-time token, compose the magic link, trigger authentication via Logto SDK).
Note: Set an expiration time for the invitation link. It’s recommended to make the link valid for at least one day. Use the following request body to generate the one-time token:
-
Send the magic link to the user’s email (e.g.,
https://yourapp.com/landing-page?type=registrationInvitation&token=YHwbXSXxQfL02IoxFqr1hGvkB13uTqcd&[email protected]). Customize the email template, such as:
When users click "Accept the invitation", they will automatically register for your service, even with public registration disabled. This is referred to as "Targeted user invitation".
Organization member invitation with magic link
For multi-tenant products (e.g., SaaS apps like Slack, GitHub, Vercel), provide a seamless member invitation process to manage organization memberships. Use magic links for higher conversion rates in member invitations.
-
Follow Logto Docs to implement organization creation, organization role-based access control, and organization management: Logto Organizations.
-
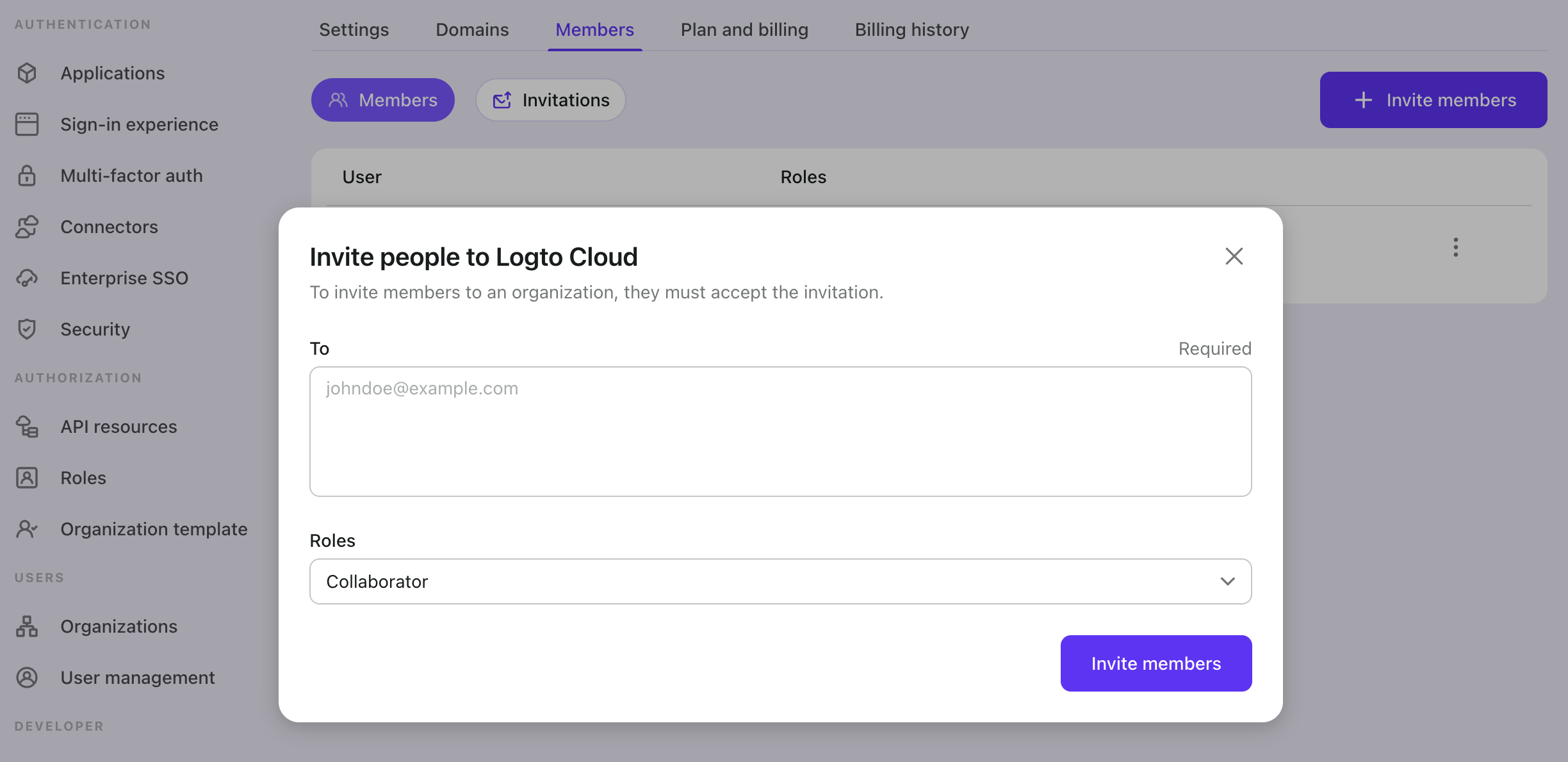
Set up the "Invite members" workflow in your product. Example:
-
Follow this guide to Invite Organization Members. Note: When inviting members, ensure the request payload includes:
context: jitOrganizationIdsto specify which organization(s) the user will join.- Set a longer
expiresIntime (e.g., 2 days or 1 week) to allow sufficient time for users to accept the invitation.
Example request payload:
-
Send the invitation link to the user’s email (e.g.,
https://yourapp.com/landing-page?type=organizationMemberInvitation&token=YHwbXSXxQfL02IoxFqr1hGvkB13uTqcd&[email protected]). Customize your email template, for example:
When users click "Accept the invitation", they will automatically sign in or sign up and auto-join the organization.
Handle account conflicts
What happens if a user is already signed in and clicks another magic link?
To handle account conflicts correctly, ensure the following:
- Avoid adding
loginin the "sign-in prompt": Do not set the sign-in prompt including theloginin it. If set incorrectly, Logto will automatically sign in the account associated with the magic link token, bypassing the account switch prompt. - Preserve existing tokens: When calling the
signIn()function, specify theclearTokens: falseparameter to prevent clearing existing tokens. If this option is used, ensure you manually clear tokens in the sign-in callback page.
After proper configuration, the user experience will be as follows:
- Magic link for the current account: If the user is already signed in and clicks a magic link for the same account, Logto will verify the one-time token and provision the user to the specified organizations if needed.
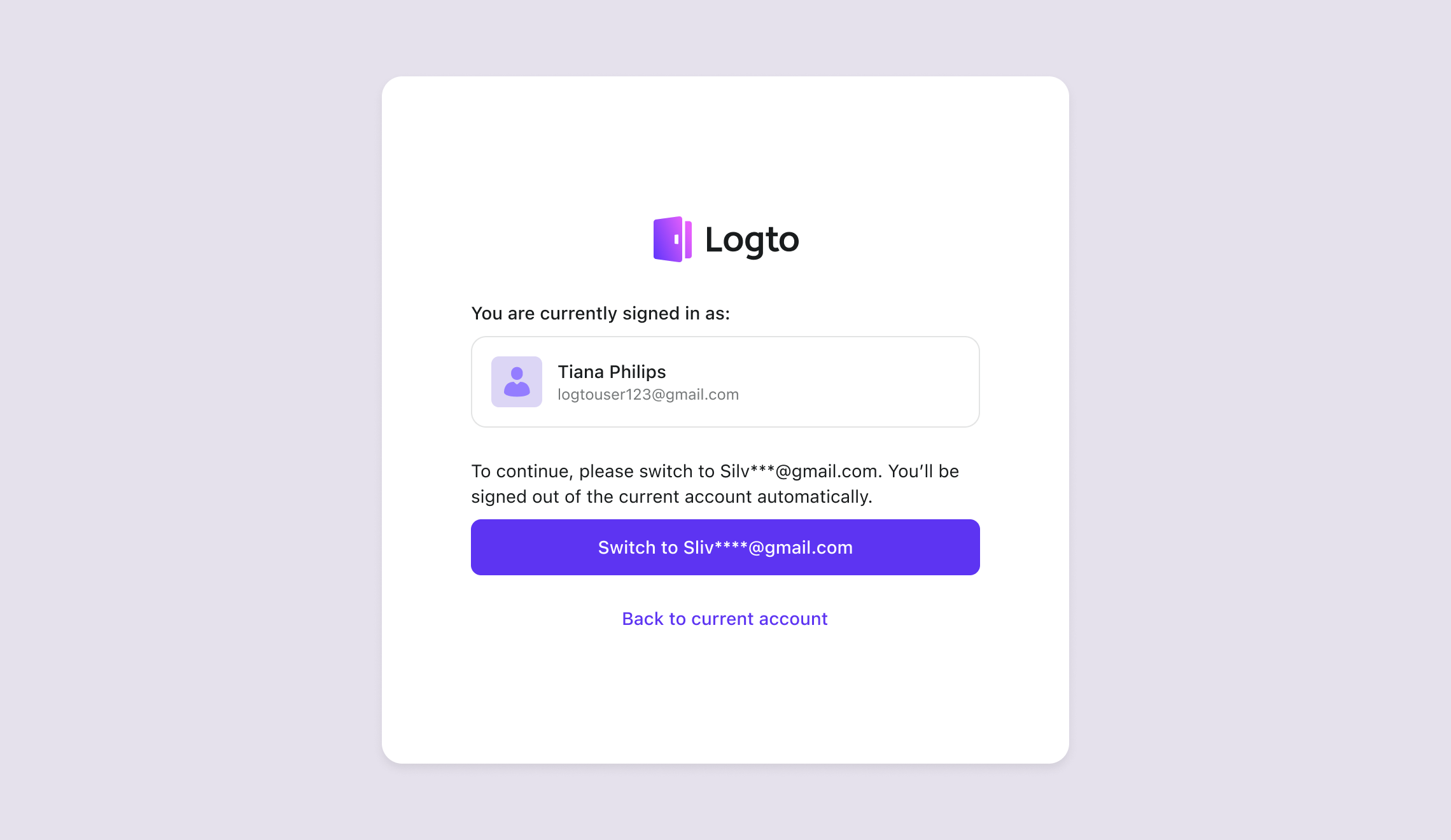
- Magic link for a different account: If the user is signed in and clicks a magic link for a different account, Logto will prompt the user to either:
- Continue as the new account: Logto switches to the new account after token verification.
- Stick with the current account: Logto skips token verification and returns the user to the current account.
Handle error pages for magic link invalidated
When users click on an invalid magic link, they will be redirected to an error page with a clear explanation of the issue. Below are the possible error scenarios and their messages:
| Name | Description |
|---|---|
| token_not_found | Active token not found with given email and token. |
| email_mismatch | Email mismatch with given token. |
| token_expired | The token is expired. |
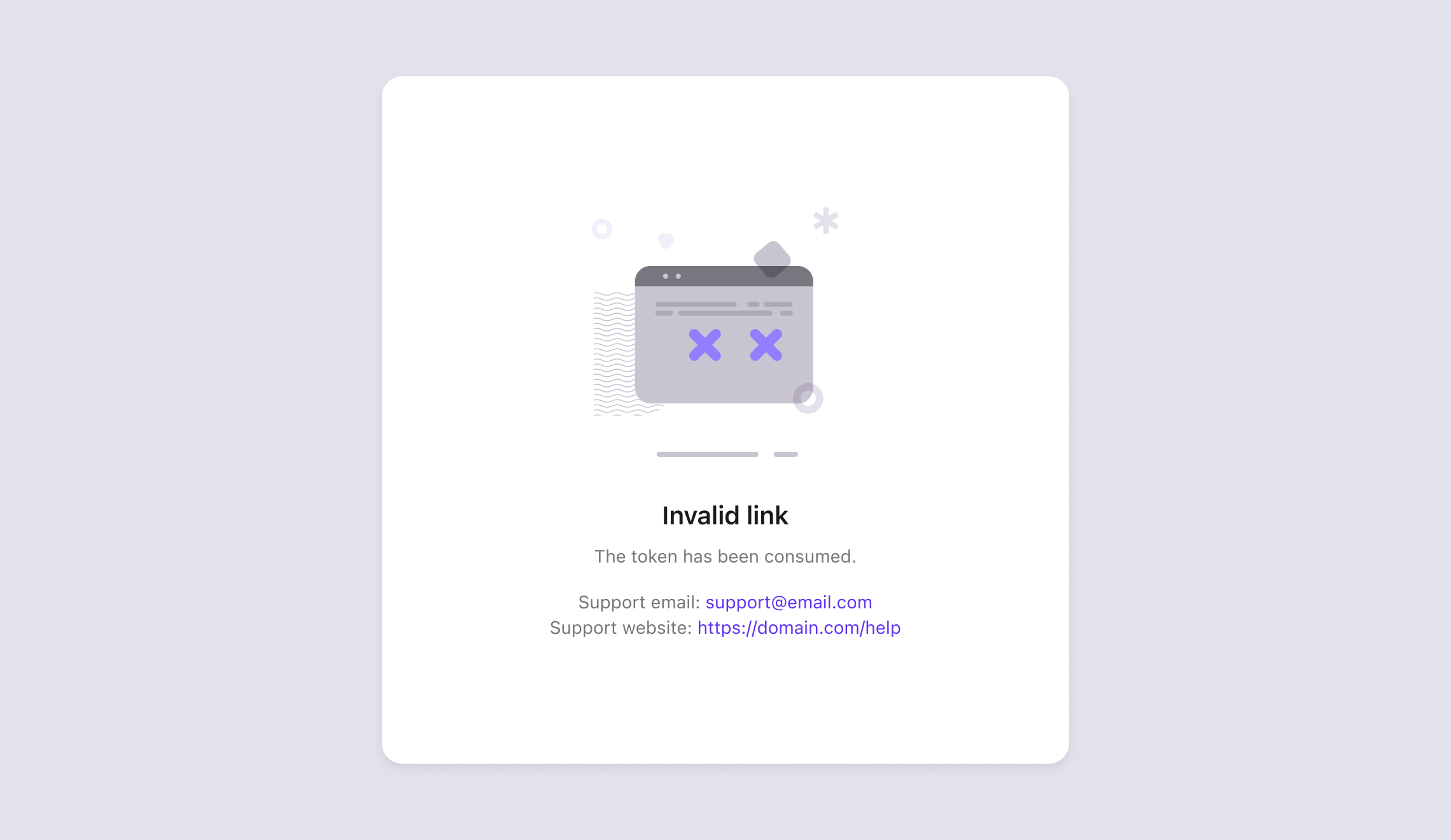
| token_consumed | The token has been consumed. |
| token_revoked | The token has been revoked. |
| cannot_reactivate_token | Cannot reactivate the token. |
Each error page will provide a specific message, helping users understand the reason behind the invalid magic link and guiding them on the next steps. For example:
Conclusion
Logto delivers enterprise-level security through flexible, passwordless sign-in flows using magic links. It's a simple but powerful way to create smooth user experiences—whether you're inviting users to join an organization, letting them create accounts effortlessly, or providing hassle-free authentication. And because Logto handles tricky situations like account conflicts and expired tokens, your users get a secure, frustration-free process every time.
Ready to modernize your IAM with bulletproof authentication?

