OTP bots: What they are and how to prevent attacks
Learn what OTP bots are, how they exploit one-time passwords with real cases, and strategies to protect your business from these cyber threats. This guide offers actionable tips for professionals in product development and enterprise management.
With the increasing reliance on online services, multi-factor authentication (MFA) has become a critical line of defense against cyberattacks. Among the most widely used MFA elements is the one-time password (OTP), a temporary, unique code meant to secure accounts against unauthorized access. However, OTPs are no longer as foolproof as they once seemed. A new wave of cybercriminal activity involving OTP bots is challenging their effectiveness and posing a serious threat to businesses and individuals alike.
Understanding how OTP bots function, their methods of attack, and strategies to defend against them is essential. This guide will break down the mechanics behind OTP bots and provide actionable steps your organization can take to bolster security.
What is an OTP?
A one-time password (OTP) is a unique, time-sensitive code used for single-use authentication. Generated through algorithms based on time synchronization or cryptographic computations, OTPs provide an additional layer of security for sign-ins or multi-factor authentication (MFA) systems.
OTPs can be delivered in several ways:
- SMS codes: Sent via text or voice message.
- Email codes: Sent directly to the user’s inbox.
- Authenticator apps: Locally generated through services like Google Authenticator or Microsoft Authenticator.
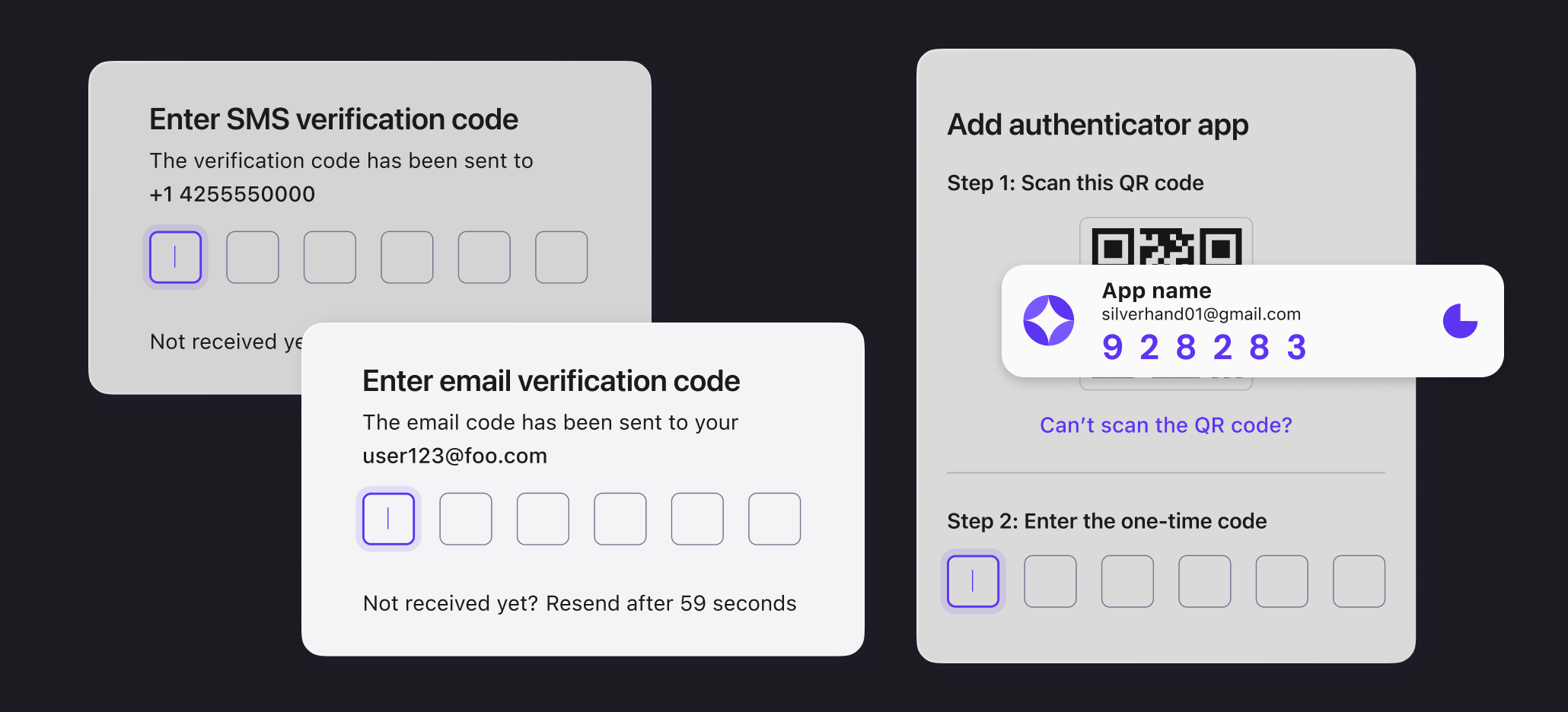
Their short-lived nature enhances security, with app-generated codes typically expiring in 30 to 60 seconds, while SMS or email codes last 5 to 10 minutes. This dynamic functionality makes OTPs far more secure than static passwords.
However, a key vulnerability lies in their delivery, as attackers may exploit system weaknesses or human error to intercept them. Despite this risk, OTPs remain a trusted and effective tool for bolstering online security.
What is the role of OTPs in MFA?
Understanding Multi-Factor Authentication (MFA) is crucial in today’s digital landscape. MFA strengthens security by requiring users to verify their identity through multiple factors, adding an extra layer of protection to prevent unauthorized access.
A typical MFA process involves the following steps:
- User identifier: This is how the system recognizes users. It could be a username, email address, phone number, user ID, employee ID, bank card number, or even a social identity.
- First authentication factor: Most commonly, this is a password, but it can also be an email OTP or SMS OTP.
- Second authentication factor: This step uses a method different from the first, such as SMS OTPs, authenticator app OTPs, physical security keys, or biometrics like fingerprints and facial recognition.
- Optional third authentication layer: In some cases, an additional layer is added. For example, logging into an Apple account on a new device may require extra verification.
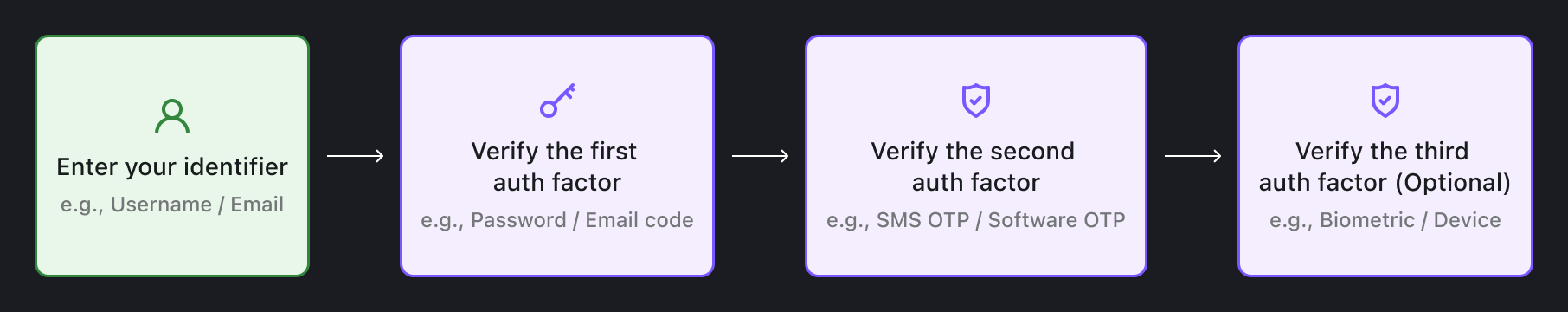
This multi-layered process significantly enhances security, as attackers would need to bypass each layer to gain access to an account.
MFA typically relies on three categories of authentication factors:
| What it means | Verification factors | |
|---|---|---|
| Knowledge | Something you know | Passwords, Email OTPs, Backup codes |
| Possession | Something you have | SMS OTPs, Authenticator app OTPs, Security keys, Smart cards |
| Inherence | Something you are | Biometrics like fingerprints or face ID |
By combining these methods, MFA creates a robust defense against unauthorized access. It ensures that even if one layer is compromised, the overall security of the account remains intact, providing users with enhanced protection in an increasingly connected world.
What are OTP bots?
OTP bots are automated tools specifically designed to steal one-time passwords (OTPs). Unlike brute-force attacks, these bots rely on deception and manipulation, exploiting human errors, social engineering tactics, or system vulnerabilities to bypass security protocols.
Taking the common verification process of "Email (as an identifier) + Password (as the first verification step) + Software/SMS OTP (as the second verification step)" as an example, the attack typically unfolds in the following steps:
- The attacker accesses the application’s login page or API, just like a regular user.
- The attacker inputs the victim’s fixed credentials, such as their email address and password. These credentials are often obtained from databases of leaked user information readily available for purchase online. Many users tend to reuse passwords across different platforms, making them more vulnerable. Additionally, phishing techniques are frequently used to trick users into revealing their account details.
- Using an OTP bot, the attacker intercepts or retrieves the victim’s one-time password. Within the valid time frame, they bypass the two-step verification process.
- Once the attacker gains access to the account, they may proceed to transfer assets or sensitive information. To delay the victim from discovering the breach, attackers often take steps such as deleting notification alerts or other warning signs.
Now, let’s explore in greater detail how OTP bots are implemented and the mechanisms that enable them to exploit these vulnerabilities.
How do OTP bots work?
Below are some of the most common techniques employed by OTP bots, outlined alongside real-world examples.
Phishing bots
Phishing is one of the most common methods used by OTP bots. Here’s how it works:
-
The bait (fraudulent message): The victim receives a fake email or text message pretending to be from a trusted source, such as their bank, social media platform, or a popular online service. The message usually claims there’s an urgent issue, like a suspicious login attempt, payment issue, or account suspension, pressuring the victim to take immediate action.
-
The phony login page: The message includes a link that directs the victim to a fake login page designed to look exactly like the official website. This page is set up by attackers to capture the victim's login credentials.
-
Credentials stolen and MFA triggered: When the victim enters their username and password on the fake page, the phishing bot quickly uses these stolen credentials to login to the real service. This login attempt then triggers a multi-factor authentication (MFA) request, such as a one-time password (OTP) sent to the victim’s phone.
-
Deceiving the victim for the OTP: The phishing bot tricks the victim into providing the OTP by displaying a prompt on the fake page (e.g., “Please enter the code sent to your phone for verification”). Thinking it's a legitimate process, the victim enters the OTP, unknowingly giving the attacker everything they need to complete the login on the actual service.
For example, in the U.K., tools like "SMS Bandits" have been used to deliver sophisticated phishing attacks via text messages. These messages mimic official communications, tricking victims into divulging their account credentials. Once the credentials are compromised, SMS Bandits enable criminals to bypass multi-factor authentication (MFA) by initiating OTP theft. Alarmingly, these bots achieve a success rate of approximately 80% once a target’s phone number is entered, highlighting the dangerous effectiveness of such phishing schemes.
Malware bots
Malware-based OTP bots are a serious threat, directly targeting devices to intercept SMS-based OTPs. Here’s how it works:
- Victims unknowingly download malicious apps: Attackers create apps that look like legitimate software, such as banking or productivity tools. Victims often install these fake apps through misleading ads, unofficial app stores, or phishing links sent via email or SMS.
- Malware gains access to sensitive permissions: Once installed, the app requests permissions to access SMS, notifications, or other sensitive data on the victim’s device. Many users, unaware of the risk, grant these permissions without realizing the app’s true intent.
- Malware monitors and steals OTPs: The malware runs silently in the background, monitoring incoming SMS messages. When an OTP is received, the malware automatically forwards it to the attackers, giving them the ability to bypass two-factor authentication.
A report revealed a campaign using malicious Android apps to steal SMS messages, including OTPs, affecting 113 countries, with India and Russia hit hardest. Over 107,000 malware samples were found. Infected phones may unknowingly be used to register for accounts and harvest 2FA OTPs, posing serious security risks.
SIM swapping
Through SIM swapping, an attacker takes control of a victim’s phone number by duping telecom providers. How it works:
- Impersonation: The attacker gathers personal information about the victim (like name, date of birth, or account details) through phishing, social engineering, or data breaches.
- Contacting the Provider: Using this information, the attacker calls the victim’s telecom provider, pretending to be the victim, and requests a SIM card replacement.
- Transfer Approval: The provider is duped into transferring the victim’s number to a new SIM card controlled by the attacker.
- Interception: Once the transfer is complete, the attacker gains access to calls, messages, and SMS-based one-time passwords (OTPs), allowing them to bypass security measures for bank accounts, email, and other sensitive services.
SIM-swapping attacks are on the rise, causing significant financial damage. In 2023 alone, the FBI investigated 1,075 SIM-swapping incidents, resulting in $48 million in losses.
Voice call bots
Voice bots use advanced social engineering techniques to trick victims into revealing their OTPs (one-time passwords). These bots are equipped with pre-set language scripts and customizable voice options, allowing them to impersonate legitimate call centers. By pretending to be trusted entities, they manipulate victims into disclosing sensitive codes over the phone. How it works:
- The bot makes the call: The bot contacts the victim, pretending to be from their bank or a service provider. It informs the victim of "suspicious activity" detected on their account to create urgency and fear.
- Identity verification request: The bot asks the victim to "verify their identity" to secure their account. This is done by requesting the victim to input their OTP (sent by the actual service provider) over the phone.
- Immediate account breach: Once the victim provides the OTP, the attacker uses it within seconds to gain access to the victim’s account, often stealing money or sensitive data.
The Telegram platform is frequently utilized by cybercriminals either to create and manage bots or to function as a customer support channel for their operations. One such example is BloodOTPbot, an SMS-based bot capable of generating automated calls that impersonate a bank’s customer support.
SS7 Attacks
SS7 (Signaling System 7) is a telecom protocol crucial for routing calls, SMS, and roaming. However, it has vulnerabilities that hackers can exploit to intercept SMS, including one-time passwords (OTPs), and bypassing two-factor authentication (2FA). These attacks, though complex, have been used in major cybercrimes to steal data and money. This highlights the need to replace SMS-based OTPs with more secure options like app-based authenticators or hardware tokens.
How to stop OTP bot attacks?
OTP bot attacks are becoming increasingly effective and widespread. The rising value of online accounts, including financial accounts, cryptocurrency wallets, and social media profiles, makes them lucrative targets for cybercriminals. Additionally, the automation of attacks through tools like Telegram-based bots has made these threats more accessible, even to amateur hackers. Finally, many users place blind trust in MFA systems, often underestimating how easily OTPs can be exploited.
Thus, protecting your organization from OTP bots requires strengthening your security across several key areas.
Strengthen primary authentication security
Gaining access to a user account requires overcoming multiple layers of protection, which makes the first layer of authentication critical. As mentioned earlier, passwords alone are highly vulnerable to OTP bot attacks.
- Leverage social login or enterprise SSO: Use secure third-party identity providers (IdPs) for primary authentication, such as Google, Microsoft, Apple for social login, or Okta, Google Workspace, and Microsoft Entra ID for SSO. These passwordless methods offer a safer alternative to passwords that attackers can easily exploit.
- Implement CAPTCHA and bot detection tools: Safeguard your system by deploying bot detection solutions to block automated access attempts.
- Strengthen password management: If passwords remain in use, enforce stricter password policies, encourage users to adopt password managers (e.g., Google Password Manager or iCloud Passwords), and require periodic password updates for enhanced security.
Apply smarter Multi-Factor Authentication
When the first line of defense is breached, the second layer of verification becomes critical.
- Switch to hardware-based authentication: Replace SMS OTPs with security keys (like YubiKey) or passkeys following the FIDO2 standard. These require physical possession, which are resistant to phishing, SIM swapping, and man-in-the-middle attacks, offering a much stronger layer of security.
- Implement adaptive MFA: Adaptive MFA continuously analyzes contextual factors such as the user's location, device, network behavior, and login patterns. For example, if a login attempt is made from an unrecognized device or an unusual geographic location, the system can automatically request additional steps like answering a security question, or verifying identity through biometric authentication.
User education
Humans remain the weakest link, so making education a top priority.
- Use clear branding and URLs to minimize phishing risks.
- Train users and employees to recognize phishing attempts and malicious apps. Regularly remind users to avoid sharing OTPs over voice calls or phishing pages, no matter how convincing they seem.
- When abnormal account activity is detected, promptly notify administrators or programmatically terminate the operation. Audit logs and webhooks can help this process work.
Rethink authentication with dedicated tools
Implementing an in-house identity management system is costly and resource-intensive. Instead, businesses can protect user accounts more efficiently by partnering with professional authentication services.
Solutions like Logto offer a powerful combination of flexibility and robust security. With adaptive features and easy-to-integrate options, Logto helps organizations stay ahead of evolving security threats like OTP bots. It’s also a cost-effective choice for scaling security as your business grows.
Discover the full range of Logto's capabilities, including Logto Cloud and Logto OSS, by visiting the Logto website:

