Personal Access Tokens, M2M authentication, and API Keys definition and their real-world scenarios
Learn the differences between Personal Access Tokens (PATs), Machine-to-Machine (M2M) authentication, and API Keys, and how they can be used.
If you’re building a software or SaaS product, you’ll often encounter a broad use case or feature request: API requests. Especially larger enterprise clients may want programmatic access to resources, either at a personal or organizational level.
In these cases, API keys, Personal Access Tokens (PATs), and Machine-to-Machine (M2M) authentication are often needed. In this article, we’ll explore the differences between these methods and how they can be used in B2B product development for developers.
The similarities
Let’s first take a look at the similarities between those three.
- Security purpose: All three methods are used to secure and control access to APIs, services, or resources. They all serve as a means of authentication and/or authorization.
- Token-based approach: Each method typically involves the use of a unique string or token for identification. These tokens are usually sent with API requests, often in headers or as query parameters.
- Revocable: Tokens or keys in all three methods can be revoked or invalidated if compromised or no longer needed. This allows for quick security responses without changing the underlying system.
- Programmable access: All three methods facilitate programmatic access to APIs or services. They enable automation and integration between different systems or applications.
- Auditable: Usage of these authentication methods can be logged and audited. This enables tracking of API access, monitoring for suspicious activities, and compliance reporting.
- Adaptable to access control: All three methods can be implemented with varying levels of access control and permissions. They can be adapted to different security models and architectural requirements.
- Protocol independence: While often used with REST APIs, these methods can be applied to various types of APIs and protocols.
Understanding these similarities helps recognize the common foundations of these authentication methods. Their differences allow you to choose the most appropriate solution for specific use cases and security requirements.
Now, let’s discuss their differences, focusing on their use cases and when to use each method.
The differences
API Keys
API keys are used to identify and authorize the calling application or service. They are typically long-lived and static until rotated and often have a fixed set of permissions. They are primarily used for server-to-server communications or accessing public data, these tokens generally do not represent a specific user.
How do API keys work?
An API key is issued by an API provider and given to a registered API consumer [1], who includes it with each request. The API server then checks the API key to validate the consumer’s identity before returning the requested data.
API keys are not as effective as other forms of API authentication, such as OAuth and JWT, but they still play an important role in helping API producers monitor usage while keeping sensitive data secure.
[1]: An API consumer is any application, service, or user that interacts with an API to access its functionality or data. They send requests to the API to perform operations such as retrieving, creating, updating, or deleting resources. API consumers can be web applications, mobile apps, other servers, or even individual developers who use the API to integrate with other services or to build new functionalities on top of existing platforms.
Postman: What is an API key?
Use cases
When people discuss API key use cases, they often mention automation, data sharing, testing, development, and security control. However, these are quite technical. In real-world scenarios, the most common purpose when building products is integration.
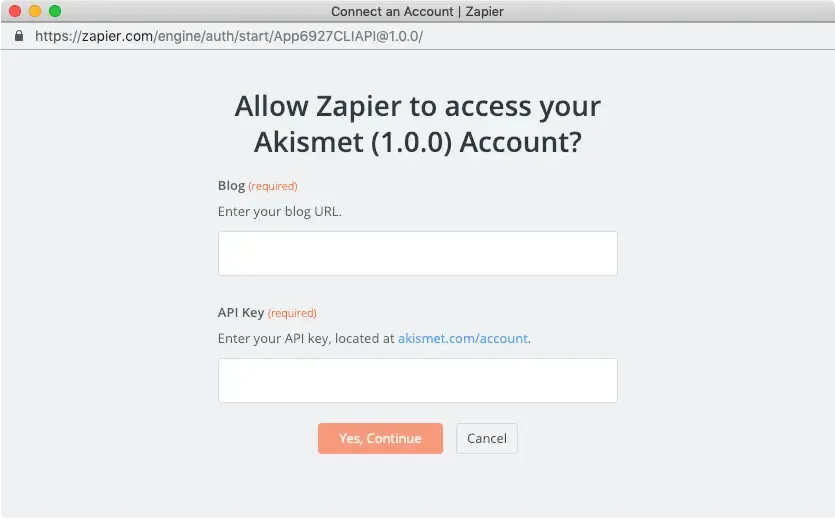
Example 1: Integration with Zapier
Zapier: Add authentication with API Key
Zapier is a popular automation tool that connects different web applications. When integrating an application with Zapier, API keys are used to authenticate and authorize access to the application's API. For instance, if you want to automate tasks between a CRM system and an email marketing tool, you would generate an API key from the CRM system and provide it to Zapier. This key is then used to authenticate requests from Zapier to the CRM's API, allowing data to flow securely between the two systems.
Example 2: Integration with Stripe
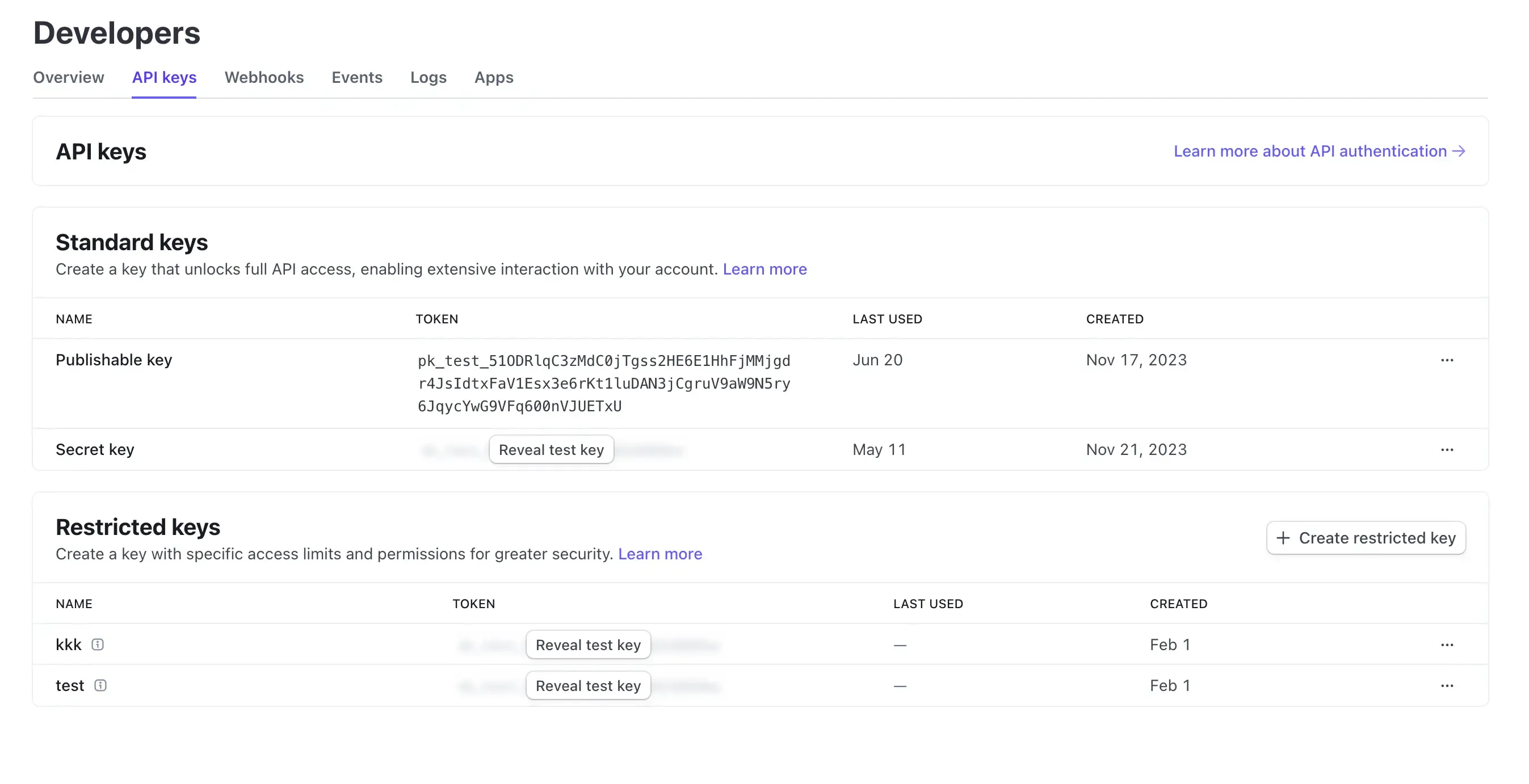
Stripe leverages API keys for secure integration with various platforms and applications. Use the Developers Dashboard to create, reveal, delete, and roll API keys.
Personal Access Tokens (PATs)
A personal access token is another similar concept but represents a specific user’s identity and permissions, is dynamically generated upon successful authentication or login, and typically has a limited lifespan but can be refreshed. They provide fine-grained access control to user-specific data and capabilities and are commonly used for CLI tools, scripts, or personal API access.
How do PATs work
- Creation and management: Users generate PATs through their account settings in the respective platform.
- For example, in GitHub, users can create fine-grained or classic PATs with specific permissions and expiration dates.
- In Atlassian products like Jira and Confluence, users can create PATs from their profile settings, specifying the token's name and optional expiration.
- Usage: PATs are used as bearer tokens in the Authorization header of API requests. This means they are included in the HTTP headers to authenticate the request.
- They enable secure access to API resources, allowing users to perform actions such as creating, reading, updating, and deleting resources based on the permissions granted to the token.
- PATs can be used across multiple applications within a platform, providing a unified way to manage access and permissions.
- Revoke and set up expiration:
- PATs offer enhanced security by allowing users to revoke tokens if they are compromised, without needing to change the account password.
- Platforms often recommend setting expiration dates for PATs to reduce the risk of long-lived tokens being exploited.
Use cases
There are two typical scenarios,
Automation and scripting
This means when a developer uses a PAT to automate the deployment of code from a repository to a production environment, reducing manual intervention and ensuring consistency.
For example, GitHub users can create PATs to authenticate Git operations over HTTPS and interact with GitHub's REST API. This is useful for developers who need to automate tasks such as cloning repositories, pushing commits, or managing issues and pull requests.
Integration with external applications
This means, enabling secure communication between different systems and applications. This looks like similar with the scenario where API key integration but PAT represents the user, not the client or application.
For example, a project manager uses a PAT to integrate a project management tool with an external issue tracking system, allowing seamless data exchange and synchronization, like Atlassian (Jira and Confluence).
The above scenarios are more like developer tools. Are PATs only useful for these kinds of products? No. Here are two additional examples: one is a CMS system, and one is a productivity tool.
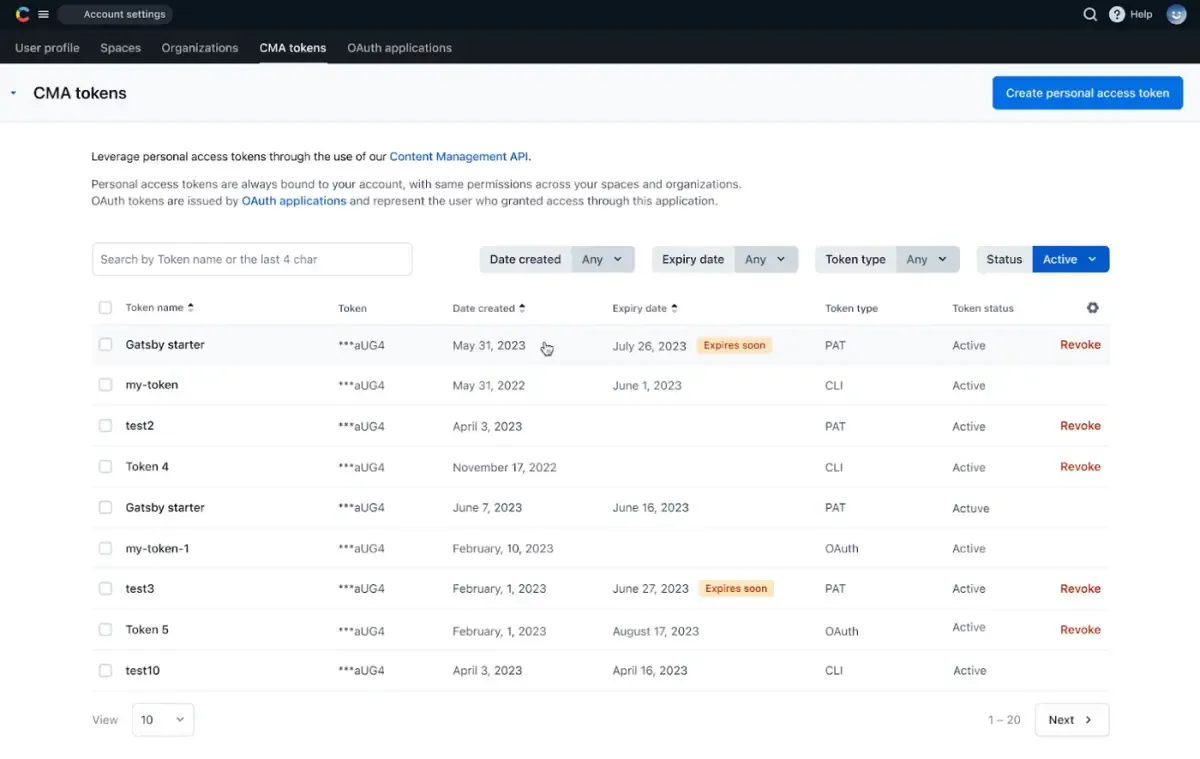
Example 1: Contentful
Contentful: Personal Access Tokens
Contentful is a headless CMS platform, offers PATs as an alternative to OAuth tokens for accessing their Content Management API (CMA).
Key features include:
- Users can create multiple tokens with different scopes and permissions.
- Tokens are tied to the user's account, inheriting their permissions.
- PATs are particularly useful for development and automation purposes.
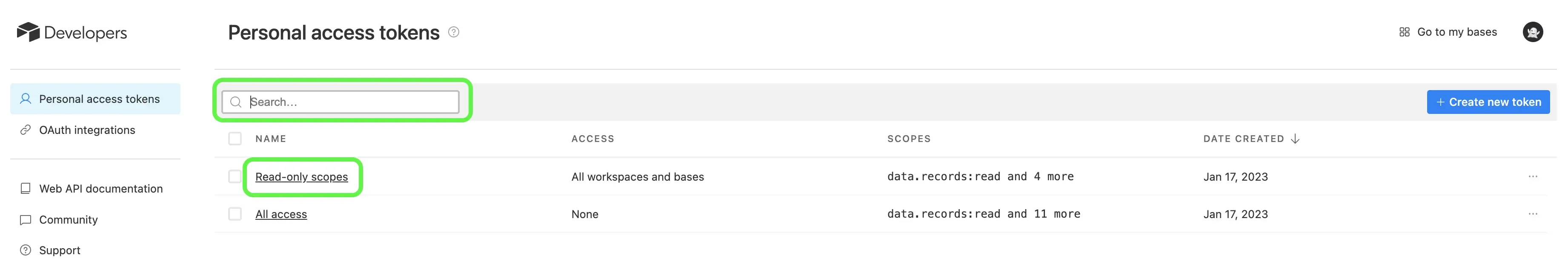
Example 2: Airtable
Creating Personal Access Tokens | Airtable Support
Airtable - a cloud collaboration platform, implements PATs for API access.
Their system allows:
- Creation of multiple tokens with varying scopes and access levels.
- Tokens can be limited to specific bases or workspaces.
- Enterprise admins can create tokens with broader access across the organization.
Machine-to-Machine (M2M) authentication
M2M is designed for service-to-service communication without human intervention. It stems from the idea that usernames and passwords are insufficient for protecting services and are not efficient for effective automation.
Machine-to-machine (M2M) applications now adopt the Client Credentials Flow, which is defined in the OAuth 2.0 RFC 6749 authorization protocol. It can also support similar standard protocols. Yes, M2M authentication is more stricter to open-standard when compared to PATs and API keys.
It authenticates the application or service itself, not a user, and often implements JWT (JSON Web Tokens) for stateless authentication. This provides a secure way for services to interact with each other in distributed systems.
How machine-to-machine authentication work
It follow the similar process:
- Client Credentials: Each machine (or service) has a unique client ID and secret.
- Token Request: The service sends these credentials to the authorization server.
- Access Token: Upon validation, the authorization server issues an access token, often a JWT (JSON Web Token).
- API Requests: The service uses this token to authenticate and authorize API requests to another service.
- Validation: The receiving service validates the token before granting access to its resources.
Use cases
Here's a concise example of using machine-to-machine (M2M) authentication for backend-to-backend communication:
Scenario: Service A needs to access data from Service B's API.
-
Setup:
- Service A is registered as a client with an authorization server.
- Service A is given a client ID and client secret.
-
Authentication:
-
Service A requests an access token from the authorization server:
-
-
Token Issuance:
- The authorization server verifies the credentials and issues a JWT access token.
-
API Request:
-
Service A uses the token to request data from Service B:
-
-
Validation:
- Service B validates the token with the authorization server.
-
Response:
- If valid, Service B returns the requested data to Service A.
This process allows secure, automated communication between Service A and Service B without user intervention, using the OAuth 2.0 client credentials flow.
Device-to-device communication
Device-to-device communication, particularly in the context of IoT (Internet of Things), relies heavily on machine-to-machine (M2M) authentication to ensure secure and efficient data exchange.
For example, like smart home devices, a smart thermostat communicates with a central home automation hub to adjust temperature settings based on user preferences. The thermostat uses M2M authentication to securely send data to the hub and receive commands, ensuring that only authorized devices can interact with the home’s heating system.
Key summary
Ok, you’ve reached the end of this article. Can I get a quick summary? Sure! Here’s a look at the key points:
- Scope: API keys are broad, PATs (Personal Access Tokens) are user-specific, and M2M (Machine-to-Machine) tokens are service-specific.
- Lifespan: API keys are long-lived, PATs have a shorter lifespan, and M2M tokens can vary.
- Representation: API keys are opaque strings, PATs can be opaque or structured, and M2M tokens often use JWTs.
- Use Case: API keys are for simple API access, PATs are for user-centric operations, and M2M tokens are for service-to-service communication.

