Why you might see a 404 when signing in to your Logto-integrated app
Have you ever encountered a "404 Not Found" error when you tried to sign in to a Logto-integrated app? This blog post explains why this happens and what you can do to avoid it.
Background
Have you ever tried signing in to an app that uses Logto for authentication and encountered a "404 not found" error? Have any of your end-users reported the same issue?
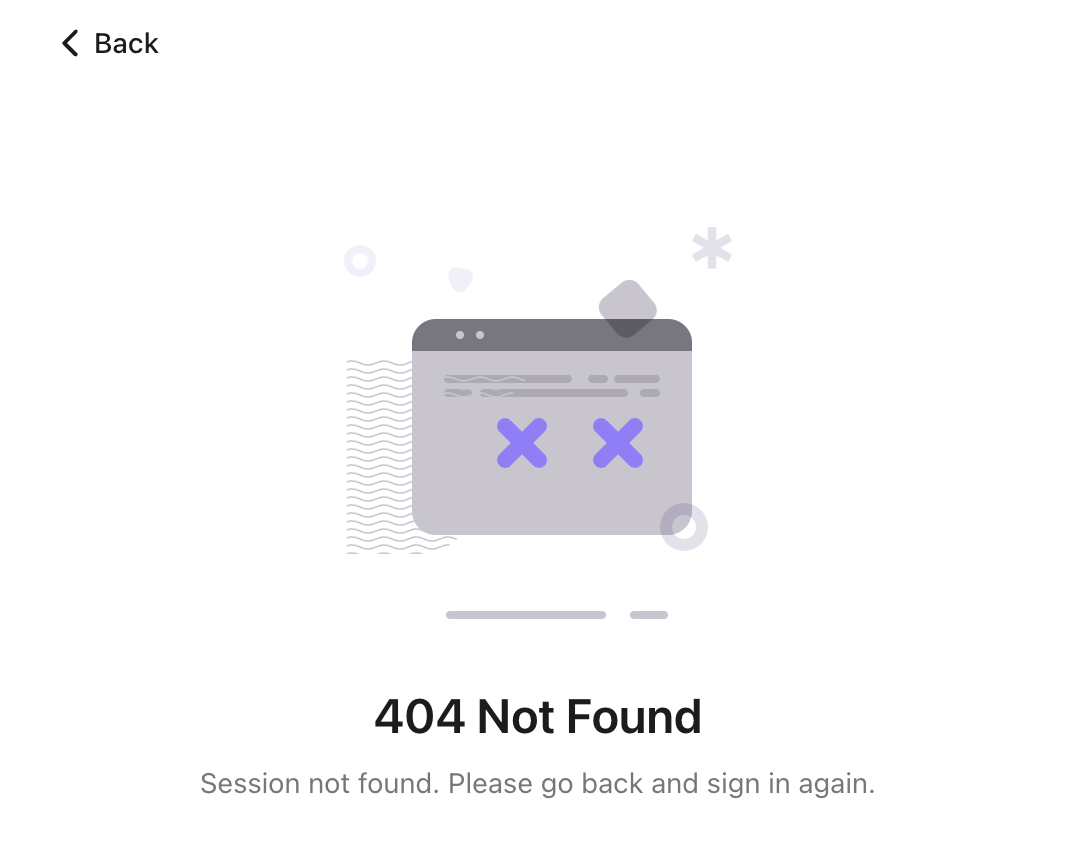
This can happen when you directly access the sign-in page (e.g., https://your-app.com/sign-in) without going through the intended sign-in flow from your application.
Here's why:
The importance of the OIDC flow
Logto relies on the OpenID Connect (OIDC) protocol for secure authentication. When you sign in through the normal application flow (e.g., typically by clicking a sign-in button from your application), the application initiates a communication with Logto’s OIDC server. This communication, called the “authorization request,” is important because it does various validations against the caller first, and then establishes a secure session between your browser and the server (managed by cookies).
The problem arises when users directly navigate to the “/sign-in” page, as this bypasses the application's internal logic that triggers the OIDC authorization request. Consequently, the server doesn't recognize your browser as having a valid session, which then leads to the 404 error.
The solution
There are two main ways to avoid this issue:
Always use the app's sign-in button
Instead of directly accessing the "/sign-in" page, follow the intended login flow provided by the application. When you click the "Sign in" button within the app, it initiates the proper OIDC authorization request, and establishing the necessary session.
Redirect users automatically
If you only have one application in your Logto instance, you may try to implement logic to automatically intercept user attempts to "/sign-in" page without a valid session, and redirect them back to your main page where a sign-in button is displayed.
To handle this, Logto introduced an “Unknown session redirect URL” setting. When you set this URL, Logto will automatically redirect users to the specified page instead of showing the 404 error. For example, you might redirect them to your app’s homepage or a custom login screen. After redirection, your client application should initiate a new sign-in flow.
To configure this, go to the Logto Console under Logto Cloud > Sign-in experience > Sign-up and sign-in > Advanced options and enter your fallback URL.
For instance, Logto Cloud sets this to https://cloud.logto.io/. Once set, users who hit /sign-in without a valid session will be sent to that URL to restart authentication.
Additional thoughts on experience improvement
We are trying to improve the user experience, by at least adding helpful messages on the "/unknown-session" page, explaining the reason for the 404 and let the users know what to do instead of being confused and clueless. For example, Logto supports custom support email and website address for sign-in error pages. Users encountering an error will then see your contact details and can reach out for assistance.
We may also consider implementing other safely measures to mitigate the problem, such as automatically redirecting to "Sign-out redirect URI" (usually the main page of the application) when there's only one application detected for the current Logto instance, or adding additional configuration to show customized message on such case.
Conclusion
The 404 not found (invalid session) error on the "/sign-in" page is usually caused by directly accessing the sign-in page URL, which bypasses the normal application sign-in flow that triggers the authorization request, and hence no valid session (managed by cookies) is established.
By understanding this flow and its importance, you can avoid the error and enjoy a seamless sign-in experience with your Logto-integrated app.
Please feel free to contact us if you would like to share your ideas.

