One-click MFA integration: Software OTP, Passkey, and backup code
Learn how to integrate MFA into your sign-in experience with one-click.
In the digital world, securing user accounts is paramount. Did you know using multi-factor authentication (MFA) blocks a whopping 99.9% of account hacks, especially those pesky password breaches? It's an extremely cost-effective method to enhance your authentication system's security.
We're excited to announce that Logto's highly anticipated MFA feature is now available and has been launched on Product Hunt. We'd love your support and feedback!
Watch our quick guide video here:
Configuration steps
Configuring MFA with Logto is straightforward and efficient. Just three simple steps to add an extra layer of defense to your product’s authentication. Here’s how:
Step 1: Choose your authentication factorPick between the Authenticator app or WebAuthn, or why not both, as your primary method.
- Authenticator app OTP, a.k.a. the software security key, is a crowd favorite.
- WebAuthn supports Passkeys for biometrics and hardware security keys – it's gaining traction for its high security and compatibility with various devices.
Don’t forget to set up a backup method too.
- Those 10 auto-generated, one-time backup codes can be lifesavers when your primary method takes a day off.
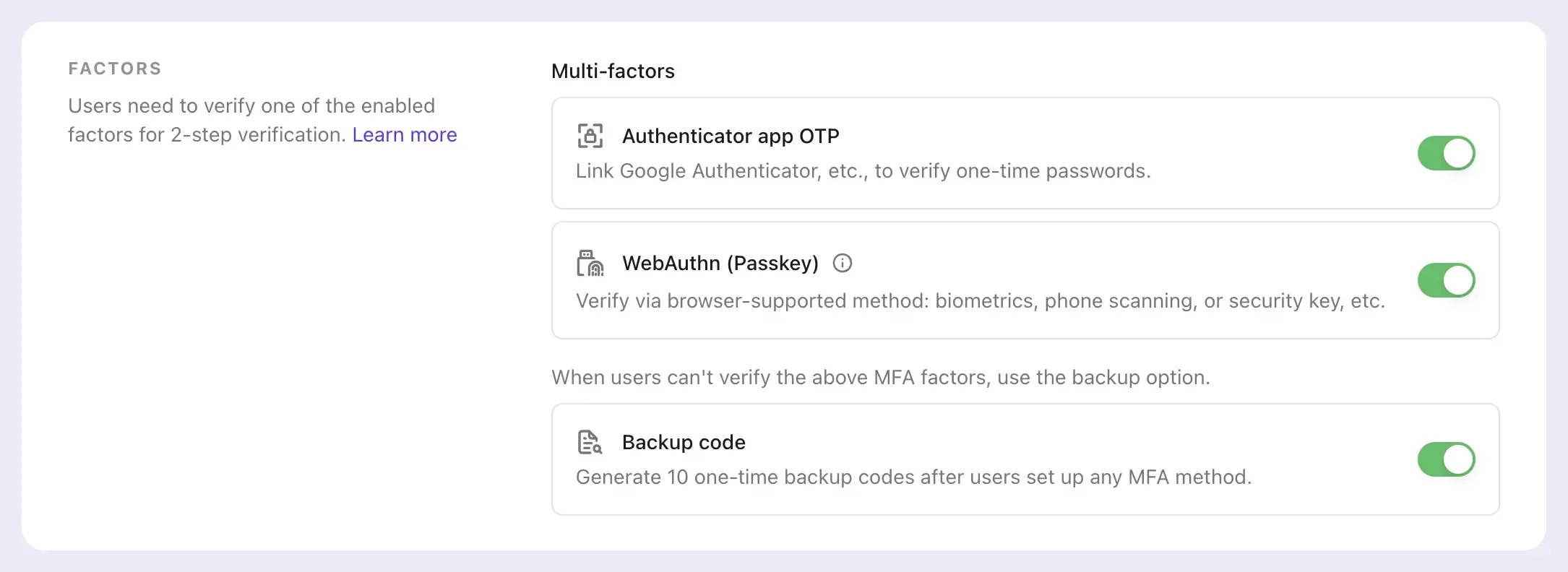
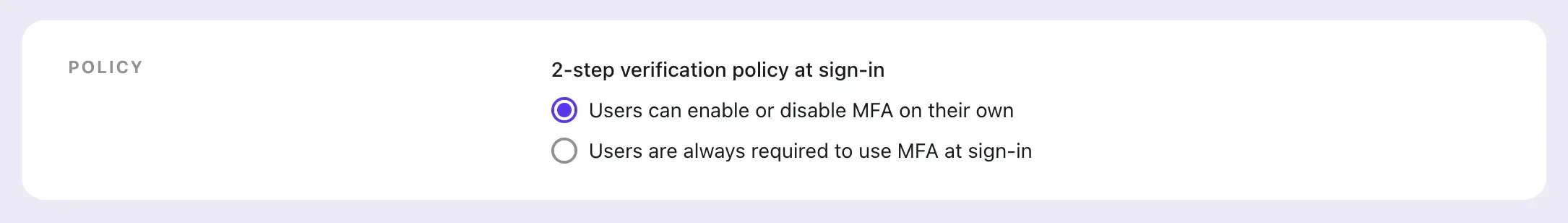
Logto offers two flavors: User-controlled MFA, ideal for consumer products or SaaS; and Mandatory MFA, suited for enterprise or financial applications.
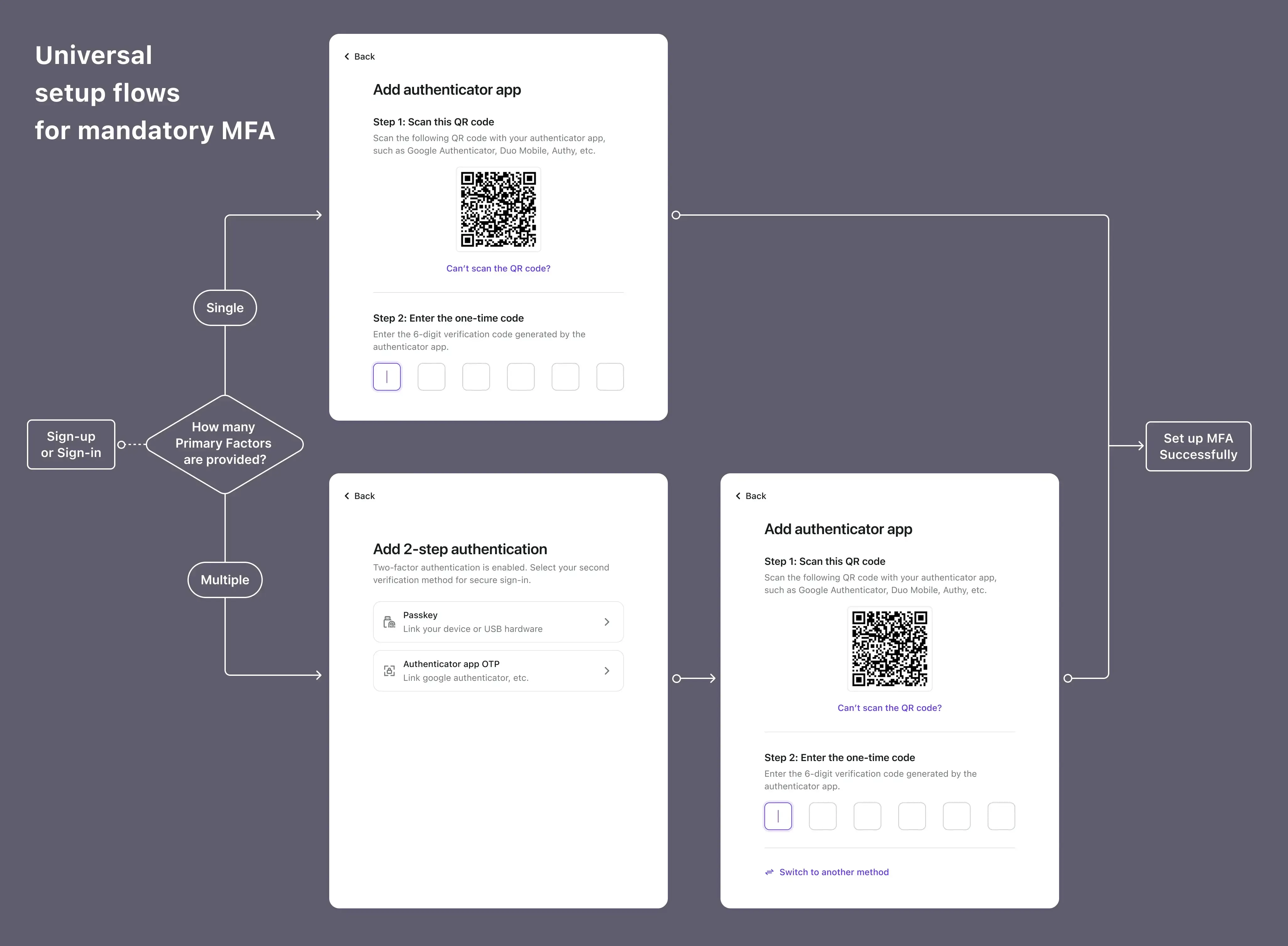
After a breezy, no-code setup, dive into the Live preview in Sign-in Experience of Logto Console or demo it in your app. Experience the smooth and complete auth flows, from setting up to verifying MFA. For detailed insights and to explore the core authentication flow interfaces, please refer to our comprehensive documentation.
Frequently asked questions
Got questions? We’ve got answers:
Is Logto's MFA auth flow secure enough?
Absolutely. Logto’s MFA sign-in experience is rock-solid for both new and existing users, following your product’s MFA policy. Even if an admin deletes a user’s MFA in the console, they’ll be prompted to set it up again at the next login.
What about WebAuthn?
Sure, WebAuthn offers top-notch security and a device-native experience, but it’s a bit of a newbie in some browsers and products. For those new to WebAuthn, our WebAuthn and Passkey 101 article is a treasure trove of info. Logto now supports WebAuthn for MFA to meet most development needs, although it doesn't yet replace passwords for the first step of authentication. Note: WebAuthn in Logto is currently available for all types of applications except Native ones.
How do users manage MFA in their account settings?
Through Logto’s Management API, integrate the configuration abilities of the Application app OTP and Backup codes, including setup, modification, and deletion. As WebAuthn is domain-bound, it doesn’t have a management API yet, but a solution is planned. You can also manage individual users’ authentication methods in the User management of Logto console.
Give it a try
Join us on this journey with Logto MFA – we hope it makes your setup and authentication experience smooth and secure. During our beta phase, your feedback and suggestions are invaluable to us, and we look forward to engaging more deeply with developers and product builders.

