What makes a good identity and access management solution
Explores the key elements of an effective IAM solution including user experience, security, integration capabilities, documentation, cost-effectiveness, support, and future readiness based on Logto's experience serving developers.
After serving business customers and developers for over three years, we at Logto have gained a deep understanding of the challenges and needs that companies face in the identity and access management (IAM) space.
Based on our practical experience, daily conversations with users, and tracking industry trends, we have a clearer view of what makes a good IAM solution. In this article, I would like to share some of our thoughts and lessons learned.
Ease of use and user experience
IAM is the gateway to any application. It is often the first thing users see. A difficult or confusing system not only increases the workload for developers but also directly hurts the experience of end users.
We believe user experience has two sides: the experience for developers, and the experience for end users.
Developer experience
Before we started building Logto, we did a lot of research on existing IAM solutions. Many developers shared the same frustration — it was hard to find a solution that was powerful but also easy to use.
For example, a CTO of a restaurant chain told us they initially tried to deploy Keycloak, a well-known open-source solution. However, they found the setup process very complicated. They had to learn many concepts and understand how different resources were organized. Even after spending a lot of time, it was still hard for their team members to understand. On top of that, they were unhappy with the user interface quality of the default login pages. In the end, they decided not to use it.
We heard many similar stories. On the surface, IAM seems simple — it is just about user login. But once it involves modern needs like OAuth 2.0, OpenID Connect, social login, MFA, and SSO, things quickly get complex. If you add features like API access control, RBAC, user groups, and permissions, poor system design can make everything even harder.
This inspired us to reduce the mental burden on users as much as possible. In Logto, we design from a regular developer’s point of view. We make every module and function clear, embed quick start guides into the UI, and provide easy-to-use SDKs.
End user experience
For end users, the login and authorization pages should look clean, modern, and nice to use. Good design makes the experience pleasant and fits most product styles without extra work.
Many customers tell us one reason they choose Logto is because our out-of-the-box login page is good-looking and user-friendly.
But that is just the basics. Developers often want the login page to match their brand style. So Logto supports full branding customization, including primary color, brand name, logo, and different settings for dark and light mode. We also allow custom CSS, with detailed documentation, so that every part of the login flow can match the style of their product.
Still, some developers want even more control. They want to build their own login pages from scratch. To meet this need, we introduced the "Bring your UI" feature, along with a set of experience APIs to help developers create their own flows.
With these options, developers can fully control the end-user login experience, either by using Logto’s pages or by building their own.
Security
Security is the foundation of all software systems. It is the bottom line that IAM solutions must never compromise.
For end users, username and password alone are no longer safe enough. A modern system must support safer methods like passwordless login (email or SMS), social login, enterprise SSO, and multi-factor authentication (MFA).
For developers, the system must also offer strong security protections: CAPTCHA, identifier lockout, CSRF protection, DoS protection, signing key rotation for JWT and cookies, backend channel logout for OIDC, and more.
Logto not only supports all of these but also follows these key principles:
-
Always open source
All core Logto components are open-source and fully transparent. This allows the community and third-party security experts to audit the code, and users can also verify it themselves. We believe open source supervision is critical for real security. -
Strictly follow standard protocols
Logto sticks to widely accepted standards like OAuth 2.0, OpenID Connect, and SAML 2.0. These standards have been tested over time and help ensure compatibility and security, avoiding the risks of custom implementations. -
Compliance
Logto meets major security and privacy compliance requirements and has achieved SOC 2 Type II certification. We stay updated with changes in laws and regulations to keep user data safe.
Of course, balancing security and user experience is not easy. Sometimes we have to make trade-offs.
For example, some developers wanted users to enter credentials directly in their app without being redirected to the Logto login page. But this would break the security model defined by standard protocols (see I need my users to fill in their credentials in my app).
Instead, we provided strong support for custom login pages. This way, users can still enjoy a smooth experience without sacrificing security.
Strong integration capabilities
In today's application ecosystem, an identity system must integrate easily into different tech stacks. Many developers only think about account management, but true power comes from deeper integration with the ecosystem — something Logto achieves by following open standards.
Integrating third-party identity systems
Through our research, we found that using third-party social login is a very common need. However, developers often complain that these flows are messy, poorly documented, and hard to debug.
To solve this, Logto provides nearly 30 built-in social connectors, including standard OIDC and OAuth 2.0 connectors. We also offer connectors for major SSO platforms like Microsoft Entra ID (SAML + OIDC), Google Workspace, Okta, and generic OIDC/SAML SSO connectors.
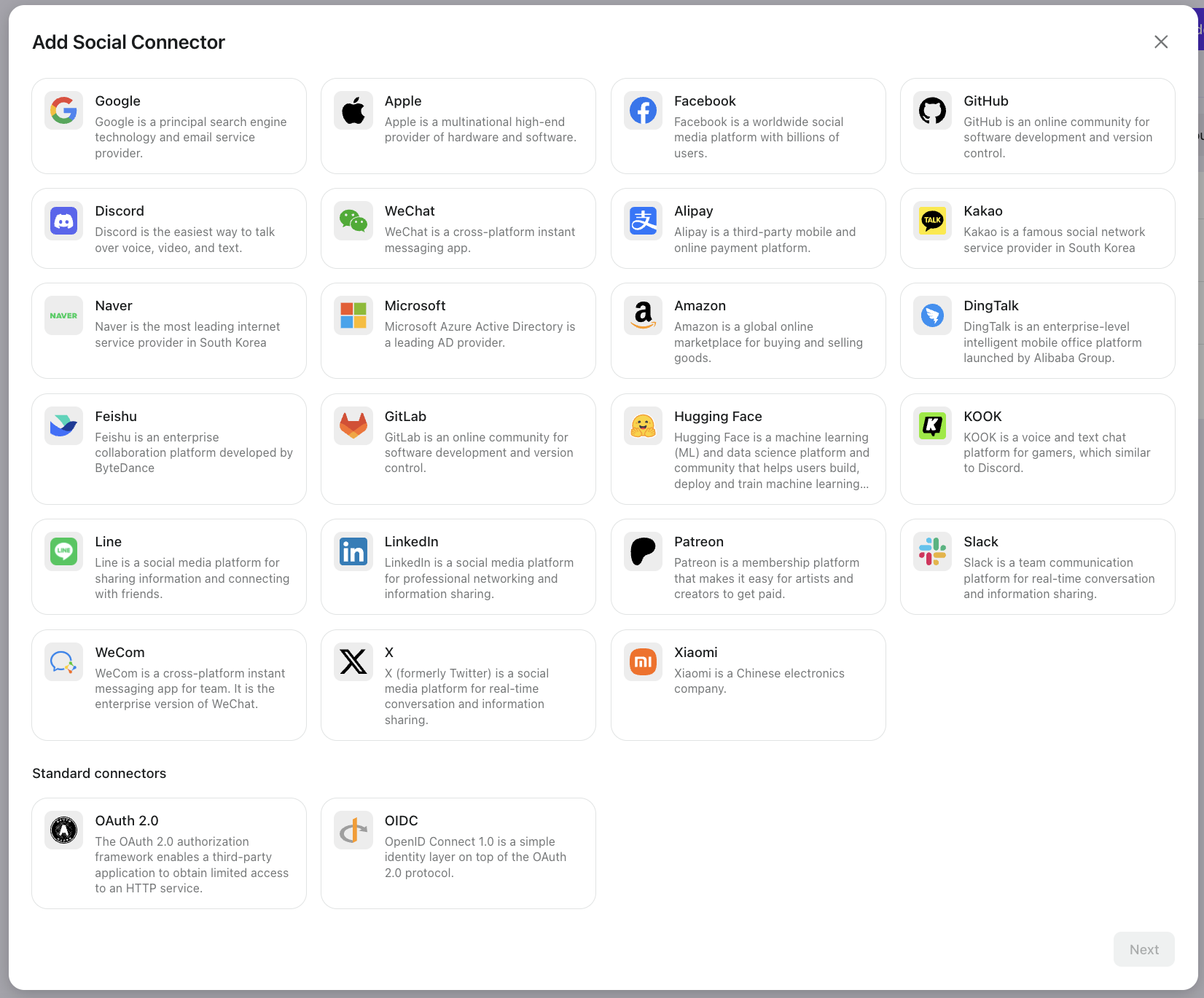
Developers can easily set them up by following step-by-step guides in the Logto console.
Integrating with your ecosystem
Logto allows you to use it as an identity provider for third-party applications. This means you can connect your Logto user system to the broader ecosystem around your product.
For example, if you launch a waiting list page or presale page, users can sign in with Logto. Later, when your product goes live, these users can log in directly with the same accounts, and you can know their user status.
If you later build a community site, you can integrate it with Logto to allow seamless user access. See Logto in action: Integrate Apache Answer to launch a community for your users.
You can also connect APIs through standard tokens, like using personal access tokens to let a local MCP Server access your system on behalf of users (check out Empower your business: Connect AI tools to your existing service with access control).
In the future, remote MCP Servers will work as resource servers protected by Logto tokens.
Clear and complete documentation
Many developers complain that the documentation for existing IAM solutions is fragmented, outdated, and hard to follow.
Some have pointed out that Auth0’s docs are "too large and sometimes self-contradictory", and Azure AD’s docs are "too general and lack case-specific examples."
Before we rebuilt our docs, we also received similar complaints.
Logto listened carefully to developer feedback. We invested a lot of effort into creating clear, practical documents, including quick start guides, detailed API references, and integration examples. Documentation is closely tied to product updates, always keeping in sync with new features.
Our blog updates weekly with articles about auth concepts, product usage, and tutorials, such as:
- RBAC in practice: Implementing secure authorization for your application
- Build a multi-tenant SaaS application: A complete guide from design to implementation
We are also building an auth resources library, including:
At Logto, we treat documentation as part of the product. We keep improving its readability, completeness, and usability to help every developer get started quickly.
Cost-effectiveness
Cost is a key factor when choosing any technical solution, and IAM solutions are no exception.
Many users feel that mainstream IAM solutions are "way too expensive" — not because they are bad, but because it is hard to justify the high price.
Logto offers a transparent and predictable pricing model, with both open-source and cloud-hosted options.
For the cloud version, we offer a generous free plan for up to 50,000 MAUs, and a Pro plan starting at $16/month with unlimited MAUs and advanced features. For enterprise needs, we offer custom Enterprise Plans based on each company’s situation.
Check out Logto pricing for more information.
Reliable customer support
Even the best products can have issues. High-quality support is essential.
Many customers told us, "I didn’t expect you to solve my problem so fast! Other services made me wait forever."
Sadly, slow and ineffective support is common with other providers. For IAM solutions, any downtime can be fatal because users cannot log in.
Logto provides community support via Discord, a self-service AI Bot, and email ticket support for Pro users. Enterprise users get advanced support with SLAs and access to solution engineers.
Our engineers handle support directly to make sure technical problems get resolved properly. We also value user feedback and use it to improve the product.
Built for the future
While we already mentioned the importance of standards, it is worth emphasizing:
Embracing the future means embracing open standards.
Standards like OAuth 2.0 and OIDC make integration easier today and prepare you for future tech changes. They are maintained by expert communities and updated to meet new security needs.
This is why Logto builds on open standards from the start — to ensure long-term flexibility and safety.
In the AI era, IAM needs are more complex than ever. OAuth 2.0 and OIDC are now more important, such as:
- Remote MCP server authorization – OAuth enables third-party agents to securely request context or actions without sharing user passwords.
- Open ecosystem integration – Your APIs can easily connect with third-party services using token-based access.
- Building AI agents – OAuth 2.0 allows agents to act on behalf of users in different apps.
- Smart devices – Device authorization flows help smart tools authenticate and access cloud services.
See Why your product needs OAuth 2.0 and OIDC — Especially in the AI era for more.
Logto strictly follows OAuth 2.0 and OIDC, ensuring both current security and future readiness.
Summary
A good IAM solution must balance ease of use, security, user choice, scalability, integration, cost-effectiveness, documentation, support, and future adaptability.
It should not only meet today’s needs but also prepare for tomorrow’s changes.
Logto aims to build a secure, easy-to-use, flexible, and affordable IAM platform based on real-world needs.
Whether for startups, large companies, traditional apps, or next-generation AI services, our goal is to provide a solution that truly meets modern identity and access management needs.

